- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Private-VLAN and trunk configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Private-VLAN and trunk configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 11:53 AM
Hello, I need help with Private-VLAN configuration. This is something that I haven't done before and I have ran into issues during the configuration.
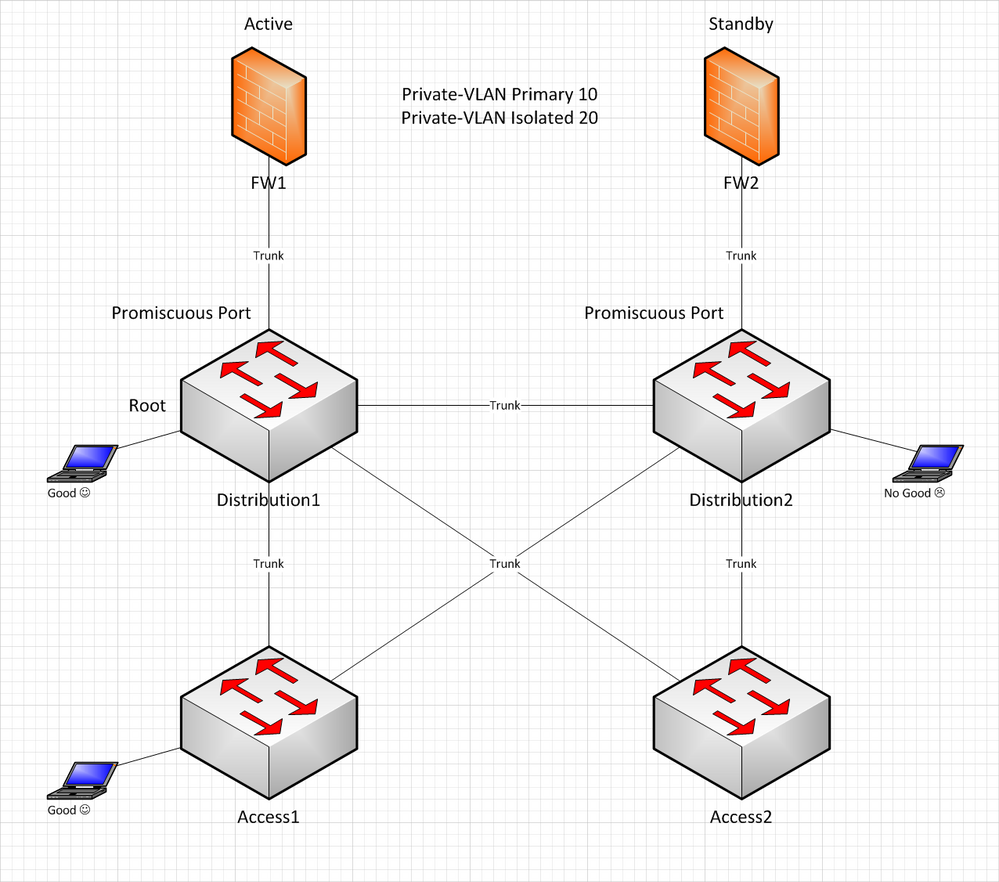
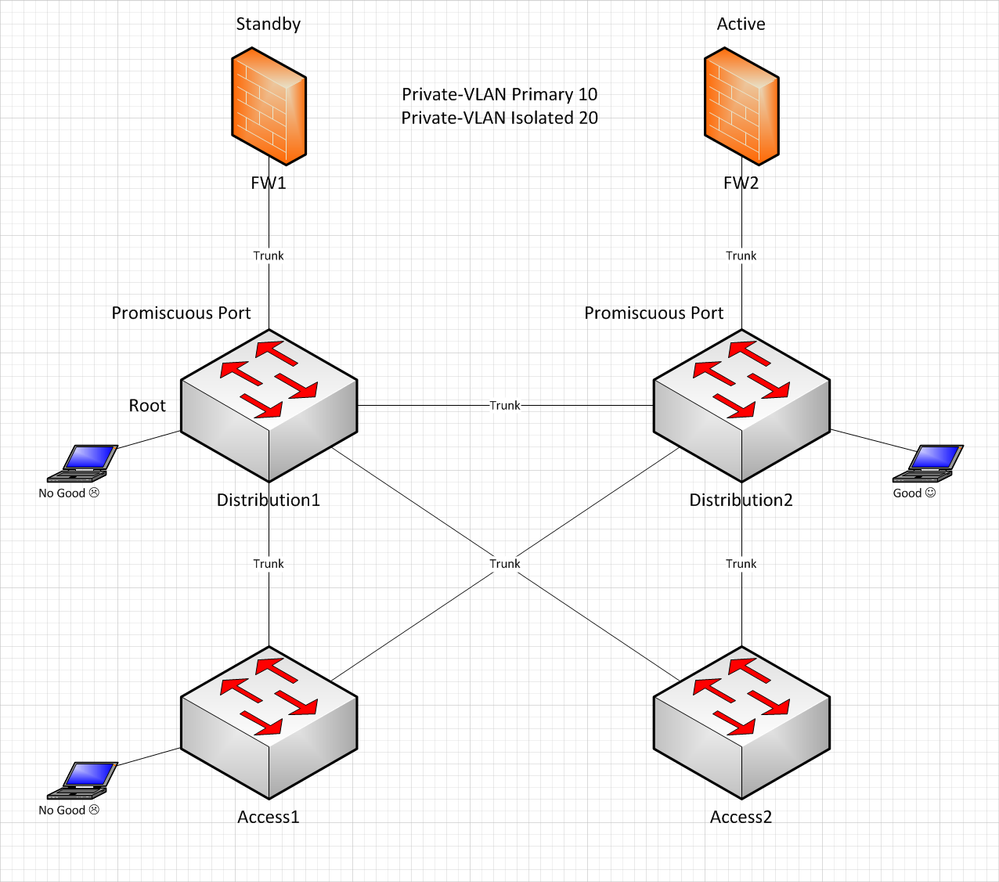
To give some background, I am trying to configure Private-VLAN for clients to be on isolated VLAN to prevent machine to machine communication. Gateway is at the firewall(HA pair) and all switches are configured with Private-VLAN with 10 as primary and 20 as isolated. Distribution1 is root bridge for all VLANs and trunk promiscuous ports are configured at the Distribution switches where FWs are connected.
Below is the simplified network diagram how devices are connected and outcome depending on which firewall is active.
Firewall Failover
Problem is when FW1 is active firewall, all seems well except the client(test) that is connected directly at Distribution2 switch. Upon firewall failover, everything fails except the client(test) that is directly connected at Distribution2 switch.
To me, it seems like there is an issue where Private-VLAN traffic cannot cross the trunk link between Distribution switches.
FYI, all trunks are regular except trunk links to the firewall. Those are set as private-vlan trunk promiscuous.
Does the trunk between Distribution requires special configuration other than regular trunk?
Any help will be greatly appreciated
Thank you and best regards
JJ
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 12:32 PM
Hello JJ,
Are you allowing all vlans across all trunks? Can you clarify what you mean by good/no good? Does that mean the client can't reach out to the internet or that the client can ping other clients so you are not getting the isolation you want?
Thanks!
CCIE# 60833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2019 12:41 PM
Thanks for the quick reply.
Yes, all VLANS are allowed across trunks between distribution switches and to firewalls. Only required VLANs are allowed between distribution and access layer. All trunks allow VLAN 10 and 20.
When good, client can reach the gateway(firewall) and communicate to other networks such as DNS, Internet and etc. When not good, client completely loses network connection and cannot reach the gateway(firewall).
Hope this answers your questions
Thank you
JJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 06:42 AM
Hello,
I put your setup into a sim (see attached) and it worked for me. I put iosv-1 and iosv-2 into HSRP with each other. I configured the ports connected to these as promiscuous ports. I configured the ports between iosvl2-1 and iosvl2-2 as a normal trunk. I think put gig1/1 on these ports as isolated host ports. I used iosv-3 and iosv-5 to simulate hosts. When I did this, each host could ping both routers but could not ping each other.
Is it possible to share your configuration? Thanks!
CCIE# 60833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 08:12 AM
I really appreciate your help on this.
Unfortunately, I cannot share the entire configuration as these devices are in production.
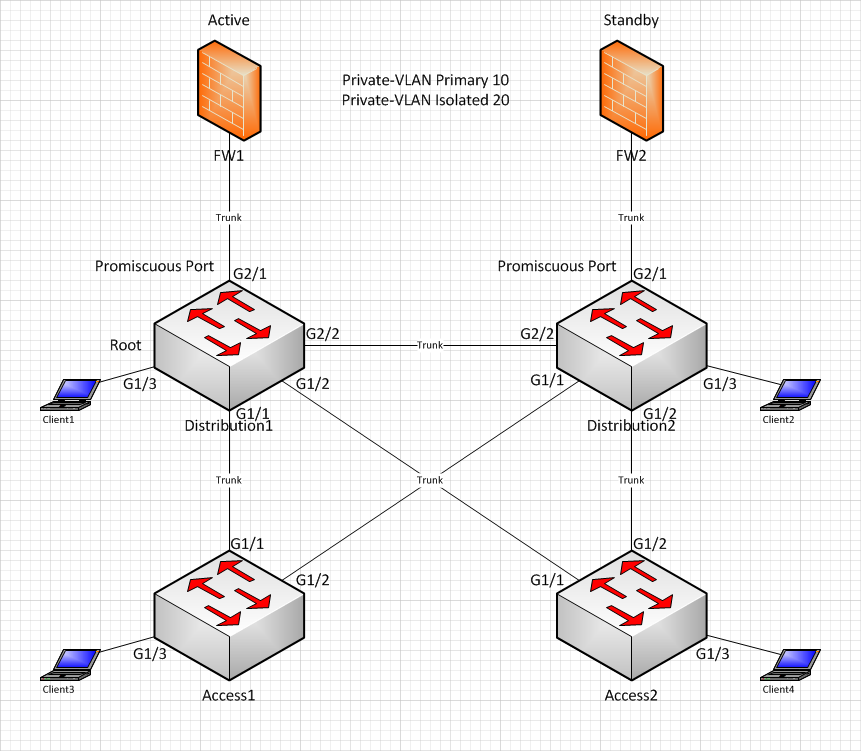
So, I trimmed it down to some VLAN configuration and modified interface numbering to simplify things a bit.
Below is the updated diagram and configuration
Here are common configuration shared between all switches
vtp mode transparent
vlan 10
name Primary
private-vlan primary
private-vlan association 20
vlan 20
name Isolated
private-vlan isolated
vlan 4094
name Native
Here are the interface configurations per switch
[Distribution1]
interface GigabitEthernet1/1
description Access1
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/2
description Access2
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/3
description client1
switchport private-vlan host-association 10 20
switchport mode private-vlan host
interface GigabitEthernet2/1
description FW1
switchport private-vlan trunk native vlan 4094
switchport private-vlan trunk allowed vlan 2-4094
switchport private-vlan mapping trunk 10 20
switchport mode private-vlan trunk promiscuous
interface GigabitEthernet2/2
description Distribution2
switchport trunk native vlan 4094
switchport mode trunk
[Distribution2]
interface GigabitEthernet1/1
description Access1
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/2
description Access2
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet2/1
description FW2
switchport private-vlan trunk native vlan 4094
switchport private-vlan trunk allowed vlan 2-4094
switchport private-vlan mapping trunk 10 20
switchport mode private-vlan trunk promiscuous
interface GigabitEthernet2/2
description Distribution1
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/3
description client
switchport private-vlan host-association 10 20
switchport mode private-vlan host
[Access1]
interface GigabitEthernet1/1
description Distribution1
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/2
description Distribution2
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/3
description client3
switchport private-vlan host-association 10 20
switchport mode private-vlan host
[Access2]
interface GigabitEthernet1/1
description Distribution1
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/2
description Distribution2
switchport trunk native vlan 4094
switchport mode trunk
interface GigabitEthernet1/3
description client4
switchport private-vlan host-association 10 20
switchport mode private-vlan host
Again, when FW1 is active, clients 1, 3, and 4 are good(able to reach the gateway and other networks)
When FW2 is active, only client 2 is good.
Let me know if you would like to see any additional configuration.
Thank you
JJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 11:45 AM
Hello,
Unfortunately, my simulator doesn't have the switchport mode private-vlan trunk promiscuous command. Just switchport mode private-vlan promiscuous so I can't validate the config 100%. However, it seems like it should work. Might be worth opening a support ticket if you have support.
Hope that helps!
CCIE# 60833
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2019 01:17 PM
Thanks for your help!!
I came here because above config didn't work :(
Hope I can something through the support.
Thanks again
JJ
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: