- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: PVLAN and Trunk on SG300
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PVLAN and Trunk on SG300
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2020 06:40 PM
Hello Community,
I use three SG300 switches to run my network. One is connected to a (free) ESX server running an OPNsense VM that acts as router. I have several VLANs that are connected using trunks between the switches and ESX. The OPNsense VM is configured to use tagged frames, and I configured multiple VLAN interfaces in OPNsense directly. So there is one vNIC using tagged frames attached to the virtual machine.
I have a separate VLAN for (IoT) devices. I want to stop communication between those devices. But they are connected to different switches, so "protected-port" setting is not enough.
I tried to setup a Private VLAN (one primary, one isolated secondary) and configured a switchport to use the isolated VLAN using the following command:
switchport private-vlan host-association [primary-id] [isolated-id]
But I don't know how to tell the switch, ESX or the VM that it is the promiscuous port. Is this possible on SG 300 series? In my current configuration, the port is not able to access the router.
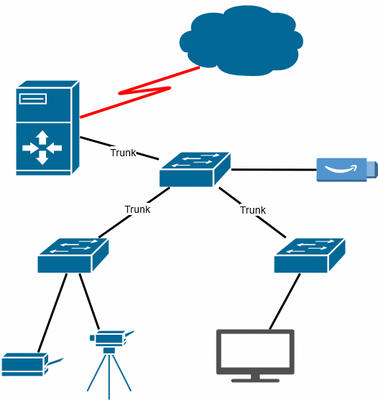
Here you can see a rough sketch of my network:
I hope someone can help me to find a solution.
Kind regards,
mfuerni
- Labels:
-
Other Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2020 05:38 AM - edited 12-26-2020 05:41 AM
Hello
I have neve had any exposure to this make/model of switch however for PVLAN to work I would assume its the same for this switch as
it is for any other make/model that supports PVLAN.
First of all the switch require to be in vtp transparent mode for PVLAN and then you need to create the vlans and assign them to either to be community or isolated pvlan.
Lastly you need to assign the port to there related vlans and also specify a promiscuous port so all hosts can communicate to/through.
See attached example:
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2020 09:53 AM
Hi Paul,
thank you for your response. I'm aware of basic PVLAN configuration. My problem is the promiscuous port which goes to the firewall: It is a trunk from one switch to the hypervisor and an additional trunk from the hypervisor to the OPNsense VM. Your configuration would need a physical port for each PVLAN.
Maybe a promiscuous trunk port would solve that problem, but on SG300 this option seems to be unavailable.
Kind regards,
mfuerni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2020 04:57 PM
Hello
@mfuerni wrote:Maybe a promiscuous trunk port would solve that problem, but on SG300 this option seems to be unavailable.
FYI - Promiscuous trunk ports are applicable in PVLAN
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 08:31 AM - edited 12-28-2020 08:31 AM
Unfortunately, on my SG300 only the following commands are available in interface configuration:
sw1(config-if)#switchport mode private-vlan ?
promiscuous private-vlan promiscuous port
host private-vlan host port
sw1(config-if)#switchport private-vlan ?
host-association configure the membership of host port within the
associated primary-secondary VLANs
mapping configure the membership of promiscuous port within
the associated primary-secondary VLANsSo the command switchport mode private-vlan trunk promiscuous seems to be not available. Is there an alternative solution for my scenario?
Or do I have to either use a different VLAN on every switch or provide a physical promiscuous port for every VLAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 10:04 AM
Hello
@mfuerni wrote:
So the command switchport mode private-vlan trunk promiscuous seems to be not available. Is there an alternative solution for my scenario?
Or do I have to either use a different VLAN on every switch or provide a physical promiscuous port for every VLAN?
Okay if its possible you could use two ports, one for the promiscuous port (access-port) for the server and another port (trunk) for all other vlans?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 06:22 PM
@paul driver wrote:Okay if its possible you could use two ports, one for the promiscuous port (access-port) for the server and another port (trunk) for all other vlans?
Hello Paul,
I hoped there is another, more elegant solution without 'wasting' a dedicated port per VLAN.
But I'll use that approach, thank you!
If anyone has a better solution, I would be glad to see it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide