- Cisco Community
- Technology and Support
- Networking
- Switching
- Radius not working Nexus 9000
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Radius not working Nexus 9000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2022 11:46 AM - edited 03-30-2022 11:48 AM
We have radius configured as follows on a Nexus 9000 switch. However the Nexus switch is not sending the radius authentication requests to the Windows NPS server. Are any configuration steps missing in the following lines?
Questions:
Is the command "radius distribute" required?
Is configuration of the management port with a vrf required? Does the vrf ip address have to be on a different subnet than the vlan interface?
Radius config:
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication accounting
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication
aaa group server radius groupname
server nexus
use-vrf management
aaa authentication login default group groupname
aaa authentication login console group groupname
radius-server directed-request
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2022 12:05 PM - edited 03-30-2022 01:03 PM
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication accounting
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication
aaa group server radius groupname
server nexus<- you use the hostname not IP address are you sure the DNS can resolve it?
use-vhf management<- are you config the manag. interface and default route for VRF management ?
aaa authentication login default group groupname
aaa authentication login console group groupname
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2022 01:01 PM
Hello,
a few things:
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication accounting
radius-server host x.x.x.x key xyz auth-port 1645 acct-port 1646 authentication
!
aaa group server radius groupname
--> server nexus <-- is this the actual config, or are you using an IP address ?
!
use-vrf management
!
aaa authentication login default group groupname
aaa authentication login console group groupname
--> ip radius source-interface mgmt 0 <-- is this in your config ?
!
--> radius-server directed-request <-- how do users login, with username@vrfname:hostname
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2022 01:53 PM
This my working config : using VRF mgmt
radius-server host 10.10.10.10 key mykey auth-port 1645 acct-port 1646 authentication accounting
!
aaa group server radius MSNPS
server 10.10.10.10
use-vrf management
!
aaa authentication login default group MSNPS
aaa authentication login console local
NPS side make sure you have roles :
priv-lvl=15
Cisco-AVPair = shell:roles="network-operator vdc-admin"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2022 04:09 PM - edited 03-30-2022 04:09 PM
Yes, it can resolve hostnames. A name server was configured. I removed use vrf-management in the aaa group server radius line. Now the switch is sending requests to the NPS server. However the requests are being rejected on the NPS server, not sure why.
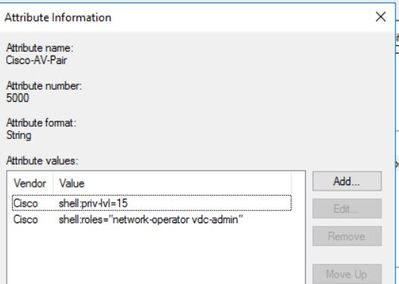
I've added the role lines as follows in NPS. Is this correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 12:04 PM
Anyone ever figure this out?
I keep getting:
9372-02# show run
% Permission denied for the role
I have NPS side setup with "shell:roles*network-admin",
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 12:11 PM
can you post #show priv
as we mentioned the steps : shell:roles=*”network-admin vdc-admin”
You need post more information what is configured on the nexus side config :
or refer to below guides :
https://itecnotes.com/network/cisco-nexus-radius-authentication-privilege-issue/
https://www.802101.com/cisco-nexus-aaa-authentication-radius/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 12:19 PM - edited 12-27-2022 12:38 PM
9372-02# show priv
User name: williamsst
Current privilege level: -1
Feature privilege: Disabled
9372-02#
username StarAdmin password 5 ***** role network-admin
radius-server host 10.1.15.15 key 7 "*******" authentication accounting
radius-server host 10.1.15.16 key 7 "*******" authentication accounting
aaa group server radius NPS
server 10.1.15.15
server 10.1.15.16
source-interface Vlan150
9372-02(config)# show user-account
user:admin
this user account has no expiry date
roles:network-admin
user:williamsst
roles:network-operator
account created through REMOTE authentication
Credentials such as ssh server key will be cached temporarily only for this user account
Local login not possible
user:StarAdmin
this user account has no expiry date
roles:network-admin
Why is my radius AD account coming back as network-operator? How can you make these Radius Windows accounts Network-Admin?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 01:54 PM
user:williamsst
roles:network-operator
is this user from AD or a Local NPS account? check the user belongs to what group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 02:43 PM
AD Windows Group from the NPS server. So how do you get it to be in a different role?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 02:48 PM
instead, create a new account and test group, and in NPS select that user group as network-admin. rather testing with already exiting users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 02:52 PM
How do you select that user group as network-admin?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 03:09 PM
follow below guide : and add user groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2022 08:09 AM - edited 12-28-2022 12:00 PM
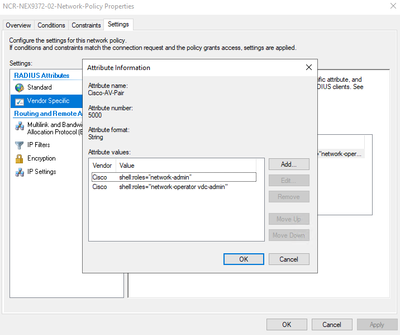
Unfortunately, this article doesn't describe Nexus. What I am asking is when I auth to the Nexus with williamsst and I am assigned the role of "network-operator" which is read only and limits my commands. I am asking how when I auth my user williamsst gets assigned to "network-admin"?
This is my NPS setup.
I am running NX-OS 7.0(3)I4(6), is there a bug?
2022 Dec 28 13:59:25.178148 radius: radius_process_fd_set
2022 Dec 28 13:59:25.178165 radius: radius_process_fd_set: mtscallback
2022 Dec 28 13:59:25.178249 radius: Src: 0x00000101/111 Dst: 0x00000101/0 ID: 0xE926E9F8 Size: 380 [REQ] Opc: 8441 (MTS_OPC_RADIUS_NEW_AAA_REQ) RR: 0x6926E9F8 HA_SEQNO: 0x00000000 TS: Wed Dec 28 14:00:26 2022 at msecs 556 REJ:0 SYNC:0 OPTIONS:0x0 Trx Id: 0
2022 Dec 28 13:59:25.178263 radius: 01 01 0C 00 00 00 00 00 00 00 00 00 01 00 02 01
2022 Dec 28 13:59:25.178272 radius: 00 00 00 00 00 00 00 06 08 00 0A 03 0A 00 00 00
2022 Dec 28 13:59:25.178280 radius: 0E 00 00 00 00 4E 50 53 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178288 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178295 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178304 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178312 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178321 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178329 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178337 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178345 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178353 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178361 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178369 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178377 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178385 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178393 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178402 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178409 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178418 radius: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
2022 Dec 28 13:59:25.178425 radius: 00 00 00 00 00 00 00 00 33 6C 6F 67 69 6E 00 64
2022 Dec 28 13:59:25.178432 radius: 65 66 61 75 6C 74 00 77 69 6C 6C 69 61 6D 73 73
2022 Dec 28 13:59:25.178439 radius: 74 73 73 68 31 30 2E 33 2E 32 34 2E 32 33 21 34
2022 Dec 28 13:59:25.178446 radius: 43 65 6E 74 65 72 40 32 30 32 32 21
2022 Dec 28 13:59:25.178459 radius: fsrv didnt consume 8441 opcode
2022 Dec 28 13:59:25.178472 radius: process_implicit_cfs_session_start: entering...
2022 Dec 28 13:59:25.178481 radius: process_implicit_cfs_session_start: exiting; we are in distribution disabled state
2022 Dec 28 13:59:25.178490 radius: sm count 0:
2022 Dec 28 13:59:25.178497 radius: process_aaa_radius_request: entering for aaa session id 0
2022 Dec 28 13:59:25.178504 radius: process_aaa_radius_request:Check for state of mgmt0 port with servergroup 'NPS'
2022 Dec 28 13:59:25.178514 radius: radius_new_global_config: entering ...
2022 Dec 28 13:59:25.178541 radius: radius_new_global_config: got back the return value of global Protocol configuration operation:SUCCESS
2022 Dec 28 13:59:25.178549 radius: radius_new_global_config: REQ:num server 2
2022 Dec 28 13:59:25.178555 radius: radius_new_global_config: REQ:num group 2
2022 Dec 28 13:59:25.178559 radius: radius_new_global_config: REQ:num timeout 5
2022 Dec 28 13:59:25.178565 radius: radius_new_global_config: REQ:num encryption_type 0
2022 Dec 28 13:59:25.178571 radius: radius_global_config: REQ:num if_index 0x0, intf
2022 Dec 28 13:59:25.178580 radius: radius_new_global_config: returning retval 0
2022 Dec 28 13:59:25.178588 radius: process_aaa_radius_request:group_info is populated in aaa_req, so Using servergroup NPS
2022 Dec 28 13:59:25.178594 radius: radius_new_servergroup_config: entering for server group, index 0
2022 Dec 28 13:59:25.178604 radius: radius_new_servergroup_config: GETNEXT_REQ for Protocol server group index:0 name:
2022 Dec 28 13:59:25.178982 radius: radius_pss_move2key: rcode = 40480003 syserr2str = no such pss key
2022 Dec 28 13:59:25.178994 radius: radius_pss_move2key: calling pss2_getkey
2022 Dec 28 13:59:25.179002 radius: radius_new_servergroup_config: GETNEXT_REQ got Protocol server group index:1 name:radius
2022 Dec 28 13:59:25.179008 radius: radius_new_servergroup_config: got back the return value of Protocol group operation:SUCCESS
2022 Dec 28 13:59:25.179013 radius: radius_new_servergroup_config: returning retval 0 for Protocol server group:radius
2022 Dec 28 13:59:25.179019 radius: radius_new_servergroup_config: entering for server groupradius, index 1
2022 Dec 28 13:59:25.179025 radius: radius_new_servergroup_config: GETNEXT_REQ for Protocol server group index:1 name:radius
2022 Dec 28 13:59:25.179039 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179054 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179061 radius: radius_new_servergroup_config: GETNEXT_REQ got Protocol server group index:2 name:NPS
2022 Dec 28 13:59:25.179067 radius: radius_new_servergroup_config: got back the return value of Protocol group operation:SUCCESS
2022 Dec 28 13:59:25.179072 radius: radius_new_servergroup_config: returning retval 0 for Protocol server group:NPS
2022 Dec 28 13:59:25.179078 radius: process_aaa_radius_request: Group NPS found. corresponding vrf is default, source_intf 151060630
2022 Dec 28 13:59:25.179086 radius: process_aaa_radius_request: checking formgmt0 vrf:management against vrf:default of requested group
2022 Dec 28 13:59:25.179107 radius: process_aaa_radius_request:mgmt_if 83886080
2022 Dec 28 13:59:25.179115 radius: process_aaa_radius_request:global_src_intf : 0, local src_intf is 151060630 and vrf_name is default
2022 Dec 28 13:59:25.179121 radius: process_aaa_radius_request: calling radius_pap_authenticate with user williamsst,servergroup NPS, hostname
2022 Dec 28 13:59:25.179127 radius: radius_pap_authenticate: received PAP authentication request for williamsst
2022 Dec 28 13:59:25.179141 radius: fill_radius_processing_state: with state: 0x121a4004
2022 Dec 28 13:59:25.179155 radius: radius_new_global_config: entering ...
2022 Dec 28 13:59:25.179167 radius: radius_new_global_config: got back the return value of global Protocol configuration operation:SUCCESS
2022 Dec 28 13:59:25.179174 radius: radius_new_global_config: REQ:num server 2
2022 Dec 28 13:59:25.179179 radius: radius_new_global_config: REQ:num group 2
2022 Dec 28 13:59:25.179185 radius: radius_new_global_config: REQ:num timeout 5
2022 Dec 28 13:59:25.179189 radius: radius_new_global_config: REQ:num encryption_type 0
2022 Dec 28 13:59:25.179195 radius: radius_global_config: REQ:num if_index 0x0, intf
2022 Dec 28 13:59:25.179204 radius: radius_new_global_config: returning retval 0
2022 Dec 28 13:59:25.179210 radius: get_radius_server_group_info: entering...
2022 Dec 28 13:59:25.179217 radius: radius_new_servergroup_config: entering for server groupNPS, index 0
2022 Dec 28 13:59:25.179222 radius: radius_new_servergroup_config: GET_REQ for Protocol server group index:0 name:NPS
2022 Dec 28 13:59:25.179228 radius: find_radius_new_servergroup: entering for server group NPS
2022 Dec 28 13:59:25.179237 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179243 radius: find_radius_new_servergroup: exiting for server group NPS index is 2
2022 Dec 28 13:59:25.179252 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179257 radius: radius_new_servergroup_config: GET_REQ got Protocol server group index:2 name:NPS
2022 Dec 28 13:59:25.179263 radius: radius_new_servergroup_config: got back the return value of Protocol group operation:SUCCESS
2022 Dec 28 13:59:25.179268 radius: radius_new_servergroup_config: returning retval 0 for Protocol server group:NPS
2022 Dec 28 13:59:25.179277 radius: radius_new_server_config: entering for server , index 1
2022 Dec 28 13:59:25.179284 radius: radius_new_server_config: GET request for Protocol server index:1 addr:
2022 Dec 28 13:59:25.179295 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179303 radius: radius_new_server_config: Got for Protocol server index:1 addr:10.1.15.156
2022 Dec 28 13:59:25.179309 radius: radius_new_server_config: got back the return value of Protocol server 10.1.15.156 operation: SUCCESS
2022 Dec 28 13:59:25.179314 radius: auth-port 1812 acct-port 1813
2022 Dec 28 13:59:25.179319 radius: radius_new_server_config: auth-port 1812 acct-port 1813
2022 Dec 28 13:59:25.179325 radius: radius_new_server_config: returning retval 0 for Protocol server:10.1.15.156
2022 Dec 28 13:59:25.179335 radius: radius_new_server_config: entering for server , index 2
2022 Dec 28 13:59:25.179341 radius: radius_new_server_config: GET request for Protocol server index:2 addr:
2022 Dec 28 13:59:25.179350 radius: radius_pss_move2key: rcode = 0 syserr2str = SUCCESS
2022 Dec 28 13:59:25.179356 radius: radius_new_server_config: Got for Protocol server index:2 addr:10.1.15.157
2022 Dec 28 13:59:25.179361 radius: radius_new_server_config: got back the return value of Protocol server 10.1.15.157 operation: SUCCESS
2022 Dec 28 13:59:25.179367 radius: auth-port 1812 acct-port 1813
2022 Dec 28 13:59:25.179372 radius: radius_new_server_config: auth-port 1812 acct-port 1813
2022 Dec 28 13:59:25.179377 radius: radius_new_server_config: returning retval 0 for Protocol server:10.1.15.157
2022 Dec 28 13:59:25.179385 radius: RADIUS_FREE 0x11db6344: radius_server_group_info_free
2022 Dec 28 13:59:25.179406 radius: build_radius_packet: entering for user williamsst
2022 Dec 28 13:59:25.179455 radius: radius_pap_authenticate: built the PAP RADIUS request packet, now send to the servers one by one
2022 Dec 28 13:59:25.179465 radius: radius_request_process: event: FIRST_REQUEST, switch to first server
2022 Dec 28 13:59:25.179470 radius: radius_request_process_next_server:
2022 Dec 28 13:59:25.179476 radius: radius_request_process_next_server: looping thru servers in servergroup...
2022 Dec 28 13:59:25.179481 radius: get_radius_server_info_from_group:
2022 Dec 28 13:59:25.179487 radius: radius_update_request_state_for_server:
2022 Dec 28 13:59:25.179492 radius: Using deadtime 0
2022 Dec 28 13:59:25.179497 radius: radius_new_global_config: entering ...
2022 Dec 28 13:59:25.179508 radius: radius_new_global_config: got back the return value of global Protocol configuration operation:SUCCESS
2022 Dec 28 13:59:25.179514 radius: radius_new_global_config: REQ:num server 2
2022 Dec 28 13:59:25.179519 radius: radius_new_global_config: REQ:num group 2
2022 Dec 28 13:59:25.179527 radius: radius_new_global_config: REQ:num timeout 5
2022 Dec 28 13:59:25.179535 radius: radius_new_global_config: REQ:num encryption_type 0
2022 Dec 28 13:59:25.179546 radius: radius_global_config: REQ:num if_index 0x0, intf
2022 Dec 28 13:59:25.179560 radius: radius_new_global_config: returning retval 0
2022 Dec 28 13:59:25.179568 radius: radius_update_request_state_for_server(1437):retrieved the global-conf.
2022 Dec 28 13:59:25.179591 radius: is_intf_up_with_valid_ip(1346):Proper IOD is found.
2022 Dec 28 13:59:25.179622 radius: is_intf_up_with_valid_ip(1349):Port is up.
2022 Dec 28 13:59:25.179778 radius: radius_update_request_state_for_server(1509):Using if_index Vlan150
2022 Dec 28 13:59:25.179791 radius: radius_update_request_state_for_server(1582):Server-shared-secret encryption-type is PROTO_NO_ENCRYPTION.
2022 Dec 28 13:59:25.179797 radius: radius_update_request_state_for_server(1643):Server-shared-secret is present in plain.
2022 Dec 28 13:59:25.179817 radius: radius_get_unique_id_or_lastglobalid: OUTPUT: 65
2022 Dec 28 13:59:25.179827 radius: radius_update_request_state_for_server(1670): request->id : 65
2022 Dec 28 13:59:25.179842 radius: radius_get_ip_local_from_src_index(389): Using intf Vlan150
2022 Dec 28 13:59:25.179850 radius: radius_get_ip_local_from_src_index(393):Retrieving ip from if_index
2022 Dec 28 13:59:25.179973 radius: num_inet_addrs: 1 first s_addr: 563478794 33.150.1.10 s6_addr : 0a01:9621::
2022 Dec 28 13:59:25.179985 radius: radius_get_ip_local_from_src_index(415):interface ip_type: IPV4
2022 Dec 28 13:59:25.179994 radius: s_addr no: 0, numeric_ip: 563478794, ip: 33.150.1.10
2022 Dec 28 13:59:25.180002 radius: radius_update_request_state_for_server(1695): Using source interface IP 10.1.150.33 as NAS IP.
2022 Dec 28 13:59:25.180008 radius: radius_update_request_state_for_server(1707): Adding NAS IP 10.1.150.33.
2022 Dec 28 13:59:25.180014 radius: get_destination_socket: last_id = 65
2022 Dec 28 13:59:25.180024 radius: getaddrinfo serv_port 1812
2022 Dec 28 13:59:25.180029 radius: get_destination_socket(260): vrf is default
2022 Dec 28 13:59:25.180050 radius: get_destination_socket(262): Context id 1
2022 Dec 28 13:59:25.180062 radius: cache id = 10.1.15.156:1812:1
2022 Dec 28 13:59:25.180074 radius: Entering : check_local_cache : Line : 1614
2022 Dec 28 13:59:25.180081 radius: list length : 4
2022 Dec 28 13:59:25.180089 radius: serv_id: 10.1.15.156:1812:1
2022 Dec 28 13:59:25.180098 radius: Entry Found
2022 Dec 28 13:59:25.180109 radius: Entering : get_res_back : Line : 615
2022 Dec 28 13:59:25.180116 radius: No of entries in server_procjob_data_t : 2
2022 Dec 28 13:59:25.180125 radius: Exiting: get_res_back , Line : 716
2022 Dec 28 13:59:25.180133 radius: check_local_cache(1643):get_res_back() ret_code is SUCCESS(0) and res is allocated.
2022 Dec 28 13:59:25.180142 radius: Found in Local Cache
2022 Dec 28 13:59:25.180152 radius: returning sockfd 49 for host 10.1.15.156:1812
2022 Dec 28 13:59:25.180159 radius: radius_request_process_next_server: found a valid server 10.1.15.156
2022 Dec 28 13:59:25.180165 radius: radius_request_process :Calling should_keywrap_attributes_be_added :3298
2022 Dec 28 13:59:25.181765 radius: Entering : should_keywrap_attributes_be_added
2022 Dec 28 13:59:25.181776 radius: should_keywrap_attributes_be_added: fips not enabled
2022 Dec 28 13:59:25.181783 radius: Entering : radius_message_authenticator_encode
2022 Dec 28 13:59:25.181789 radius: radius_request_process : Address family AF_INET
2022 Dec 28 13:59:25.181795 radius: Using vrf of src interface Vlan150
2022 Dec 28 13:59:25.181838 radius: radius_get_vrf_context_from_interface : Using VRF of the port Vlan150 : default
2022 Dec 28 13:59:25.181847 radius: sending 68 bytes to 10.1.15.156 port 1812 vrf default
2022 Dec 28 13:59:25.181949 radius: radius_set_src_intf(1932):setsockopt success, using src-intf:for server: 10.1.15.156 for sock: 49 Error returned:0x0 errno string:Operation not permitted
2022 Dec 28 13:59:25.182177 radius: radius_request_process: waiting for response from 10.1.15.156 onc vrf default 2 5 with session: dddwith state: sss
2022 Dec 28 13:59:25.182199 radius: radius_add_to_sm_table: for session : 0 with state: 0x121a4004
2022 Dec 28 13:59:25.182214 radius: radius_pap_authenticate: exiting
2022 Dec 28 13:59:25.182225 radius: process_aaa_radius_request: returning TRUE...
2022 Dec 28 13:59:25.208675 radius: radius_process_fd_set
2022 Dec 28 13:59:25.208691 radius: radius_process_fd_set: radius_data_available_callback
2022 Dec 28 13:59:25.208709 radius: radius_client_get_state on 49
2022 Dec 28 13:59:25.208724 radius: In sockaddr_compare_addr_vrf
2022 Dec 28 13:59:25.208732 radius: sockaddr_compare_addr_vrf returning success
2022 Dec 28 13:59:25.208738 radius: radius_get_state_from_addr: conditions matched
2022 Dec 28 13:59:25.208747 radius: radius_client_get_state: Retrieved correspondingstate: 0x121a4004 for the radius-server response
2022 Dec 28 13:59:25.208754 radius: radius_data_available_callback: for session : 0 and authen_type: 0 and author_type 0 with state 0x121a4004
2022 Dec 28 13:59:25.208761 radius: radius_request_process: DATA_AVAILABLE
2022 Dec 28 13:59:25.208767 radius: verify_packet: entering ...
2022 Dec 28 13:59:25.208774 radius: verify_packet: dumping the pkt ...
2022 Dec 28 13:59:25.208782 radius: radius_request_process: Calling should_keywrap_attributes_be_added :3195
2022 Dec 28 13:59:25.208787 radius: Entering : should_keywrap_attributes_be_added
2022 Dec 28 13:59:25.208793 radius: should_keywrap_attributes_be_added: fips not enabled
2022 Dec 28 13:59:25.208799 radius: verified the response from:10.1.15.156
2022 Dec 28 13:59:25.208805 radius: pap_data_available_func: entering for aaa session 0
2022 Dec 28 13:59:25.208811 radius: pap_data_available_func: RADIUS server sent accept for authentication aaa session 0
2022 Dec 28 13:59:25.208816 radius: pap_reply: entering for aaa session: 0
2022 Dec 28 13:59:25.208825 radius: find_attribute: offset is 0
2022 Dec 28 13:59:25.208832 radius: pap_reply: find_attribute PW_VENDOR_SPECIFIC attr length 12
2022 Dec 28 13:59:25 NCR-NEX9372-02 %USER-3-SYSTEM_MSG: parsing vsa:not a cisco vendor id:311 - radiusd
2022 Dec 28 13:59:25.208862 radius: rad_parse_vsa: parsing vsa:not a cisco vendor id:311
2022 Dec 28 13:59:25.208870 radius: pap_reply: rad_parse_vsa failed
2022 Dec 28 13:59:25.208878 radius: Will be calling rad_parse_vsa with new length 76
2022 Dec 28 13:59:25.208885 radius: find_attribute: offset is 76
2022 Dec 28 13:59:25.208891 radius: pap_reply: find_attribute PW_VENDOR_SPECIFIC attr length 12
2022 Dec 28 13:59:25.208905 radius: rad_parse_vsa: parsing vsa:not a cisco vendor id:311
2022 Dec 28 13:59:25.208912 radius: pap_reply: rad_parse_vsa failed
2022 Dec 28 13:59:25.208919 radius: Will be calling rad_parse_vsa with new length 88
2022 Dec 28 13:59:25.208925 radius: find_attribute: offset is 88
2022 Dec 28 13:59:25.208938 radius: send_aaa_radius_resp_mts: entering for aaa session 0
2022 Dec 28 13:59:25.208969 radius: send_aaa_radius_resp_mts: exiting for aaa session 0
2022 Dec 28 13:59:25.208981 radius: pap_reply: exiting for aaa session: 0
2022 Dec 28 13:59:25.208992 radius: free_radius_state:with state: 0x121a4004
2022 Dec 28 13:59:25.209003 radius: free_radius_state:with state: 0x121a4004, REMOVING THE ID 65
2022 Dec 28 13:59:25.209015 radius: radius_remove_from_sm_table: for session : 0 with state: 0x121a4004
2022 Dec 28 13:59:25.209027 radius: RADIUS_FREE 0x121a6ebc: free_radius_state
2022 Dec 28 13:59:25.209040 radius: RADIUS_FREE 0x121a4004: free_radius_state
2022 Dec 28 13:59:27.211104 radius: Calling radius_request_id_cleanup. Ticks elapsed = 51
no debug all
9372-02#
Nothing really stands out here on why my AD user is not getting the network admin role.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2022 12:38 PM
Ok creating a new AD-User group and New Test user in AD allows this work, but why?
9372-02# show user-account
user:admin
this user account has no expiry date
roles:network-admin
user:williamsst
roles:network-operator
account created through REMOTE authentication
Credentials such as ssh server key will be cached temporarily only for this user account
Local login not possible
user:StarAdmin
this user account has no expiry date
roles:network-admin
user:NexusTestUser
roles:network-admin
account created through REMOTE authentication
Credentials such as ssh server key will be cached temporarily only for this user account
Local login not possible
9372-02#
So how can I remove the cached user-data for williamsst?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide