- Cisco Community
- Technology and Support
- Networking
- Switching
- once you have 356 switch no
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Router on a Stick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 10:27 AM - edited 03-08-2019 03:14 AM
Hi,
I have a classique router on a stick configuration, and I want to implement some of the intervlan ACLs on the switch to take the load off the router.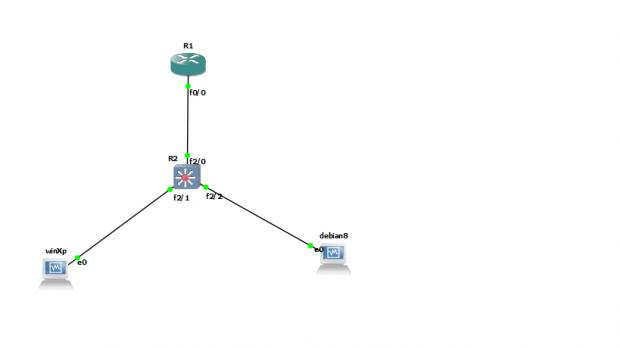
I've configured an ACL on the SVI to prevent communication between the hosts on both vlans, but this doesn't seem to work !
The setup is: each host receiving an IP from the router (DHCP), and the subinterface is its gateway, The switch is L3, and there 2 SVIs !
Am I missing something here ?
Thanks
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 10:58 AM
The access-list on the SVI will only take effect if the traffic is routed through that SVI IP address.
I don't know what switch you have, but try moving the access-list to the switch port that the router is plugged into. Not sure out this interacts with VLANs on a trunk port.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:10 AM
Hi, thanks for the replies,
1. The switch is 3560, and the "ip routing" is enabled on the switch !
2. I've set the ACL on the SVI outbound (to prevent hosts going to other vlans)
3. The SVI has an IP in the same subnet as the hosts !
4. Can't apply ACL on the trunk link because of the "no switchport"
Is there any configuration possible with preserving the current setup ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:16 AM
You could make the 3560 the default gateway for the VLANs. Then create a routed connected to the router rather than a layer 2 connection (aka no switchport).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:49 AM
But that way, can the router see the vlans ? can the router see the hosts on each vlan ?
I guess the core switch will be just another router ! I do not want that :s
I want to preserver the actual setup, and status of the links as "no switchport" !
Why doesn't the ACLs work on the core switch ?
I just want to migrate some of the control work from the router to the switch !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:53 AM
You have applied a layer 3 ACL to a layer 3 interface on the switch, but the switch is not doing any layer 3 processing of the traffic, so it has no effect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 06:54 AM
Hello
Just to clarify the switch is performing the interian routing and NOT the router?
If so then a RACL is all that is required on the switchs svi of either vlan to prohibit communication.
Please note svi acl logic
IN ---> hosts traffic from within the vlan
OUT <--- outside hosts traffic into the vlan
Lastly please share your rtr and switch configurations for clarity
Res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 09:39 AM
Hi,
That's what I intended to do, the switch to do the inter routing and not the router but leaving the links of the switch intact (that is, trunk must stay trunk, and access must stay access).
In the attached the packet tracer file if you want to give it a try !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 11:00 AM
Hi,
Since the default gateway for your hosts in different subnets is the router, you need to deploy the access list on the router and not the switch. In this case your switch is layer-2
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 12:13 PM
once you have 3560 switch no need for router on stick the switch can make inter-vlan routing
so
First configure the default Gateway of the Pcs to be the svi ip address
second ip route 0.0.0.0 0.0.0.0 (ip address of the router)
you need to create two extended access-list
for example lets say you have two vlans 5,2 and want to deny connection between hosts on these vlans
- int vlan 2 ip address 172.16.1.1/24
- int vlan 5 ip address 192.168.1.1/24
-
This access list denies traffic that comes from VLAN 2 to get to VLAN 5.
Switch#configure terminal Switch(config)#access-list 102 deny ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255 Switch(config)#access-list 102 permit ip 172.16.1.0 0.0.0.255 any
-
This access list denies traffic that comes from VLAN 5 to get to VLAN 2.
Switch#configure terminal Switch(config)#access-list 105 deny ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255 Switch(config)#access-list 105 permit ip 192.168.1.0 0.0.0.255 any
now apply the acl
Switch#configure terminal Switch(config)#interface vlan 2 Switch(config-if)#ip access-group 102 in Switch(config-if)#exit Switch#configure terminal Switch(config)#interface vlan 5 Switch(config-if)#ip access-group 105 in Switch(config-if)#end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 12:40 PM
I see what you mean, but another constraint is that the router must be there, it has to be the dhcp server and the default gateway for the clients !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 12:41 PM
I see what you mean, but another constraint is that the router must be there, it has to be the dhcp server and the default gateway for the clients !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 09:40 PM
you can configure the switch to be DHCP (CHECK WITHER THE 3650 SUPPORT THIS OR NOT),
and if NOT use the router you could use
DHCP Relay Agent by applying IP HELPER (ADDRESS OF THE ROUTER INTERFACE) ON EACH SVI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2015 12:22 AM
Alright despite all of that, is there any method to apply ACL on the core switch without actually modify the configuration of the switch ?
Thank you !
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
