- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Spanning Tree deisgn concepts/best practices for Catalyst sw
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Spanning Tree deisgn concepts/best practices for Catalyst sw
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2020 07:49 AM
I have a need to create redundant links to other switches for a mesh topology; however, I know spanning tree would elect different interfaces on Root and Blocking ports, yet I am new trying to tweak STP. What are some good design practices you have used to have a single port always the primary elected interface and determine which interface will become active when the BLOCK state changes?
Thank you
- Labels:
-
Catalyst 2000
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2020 07:55 AM
i would suggest to some good document and example :
https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/12-1E/configuration/guide/swcg/stp_enha.pdf
https://www.ciscopress.com/articles/article.asp?p=2832407&seqNum=6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2020 08:16 AM
Do you have a diagram that you can share (and your desired end state)? Typically you'd use the "spanning-tree vlan ... priority" command, at global configuration level, and "spanning-tree vlan ... cost " at the interface level to control how STP converges differently than would be done if left at default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 06:07 AM
So I have been doing my reading, and you mention 'vlans'. PVST+ has a spanning tree database per vlan; however, documentation says STP cannot work on TRUNKS. What does that mean exactly - I cannot get away with STP to have a conman path for the entire switch even when I have 20 vlans, since I do not need to detail different path topology for each vlan?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 06:48 AM
"..documentation says STP cannot work on TRUNKS. What does that mean exactly "
Without more context I cannot say for sure. Spanning tree protocol generally operates on all switchports whether they are operational as access or trunk. The primary purpose of STP is to run on trunks because its main job is to converge to a loop-free tree among a collection of switches interconnected by inter-switch links (which are usually trunk links).
It would really help to see a diagram. I will tell you that STP typically is confined to the access layer and the most common type of deployment at the access layer, in which tweaking is required, is when there are two distribution switches and each access closet uplinks to each of the distribution switches in essentially an inverted triangle (this is commonly known as the looped design). In this scenario, you tweak the STP configuration so that each distribution switch is the root bridge of some of the VLANs and roughly 50% of the traffic rides the uplink to each distribution switch. In practice it doesn't work this way because in practice people usually do not try to figure out what set of VLANs would result in an even split of traffic. Usually you'll just say something like "odd VLANs to switch one and even VLANs to switch two" or "data to switch one and voice to switch two".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2020 07:33 AM - edited 08-04-2020 07:35 AM
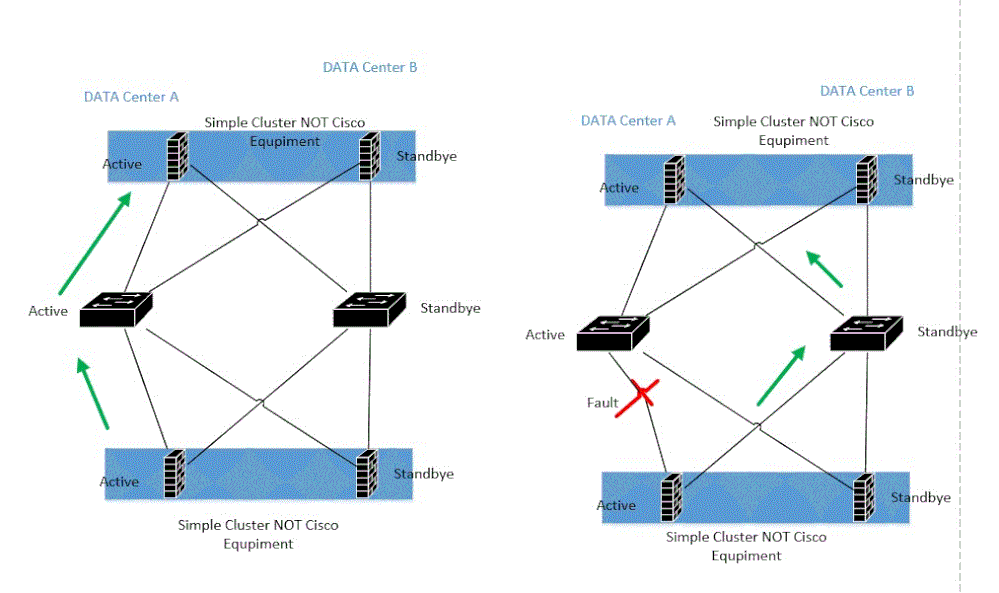
Here is a topology I am trying to build. North of the switch to the Firewalls, should see one link in Blocking state. I am reading through the STP chapters; however, been on other projects, so should be coming back to this build.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2020 08:06 AM
In this topology, how you have it wired, STP doesn't really even come into play because there are two completely separate switches and all of the connected devices are edge devices. You still need STP enabled but all ports will be forwarding. There's never going to be a blocking decision to be made. It would be different if you had the two Cisco switches connected via a trunk link.
How do these firewall clusters present an IP address when they have two separate network connections into the switch infrastructure? That looks a little odd to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2020 10:37 PM
Only one side is up at a time, so the IP is only assigned to the active unit. It is a Fortigate N+1 cluster in A/P deployment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2020 07:02 AM
Since the two interfaces connected at the 'cluster' will be UP/UP I was worried that the lower switch would see the same MAC address on two different interfaces and why I would need STP. I could totally be wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2020 10:03 AM
I'm not familiar with the details of how Fortinet does clustering but I'd be surprised if the mac used for the VIP is actively getting sent by both the primary and standby firewall. Of course all of the ports on the switch would have to be able to pass traffic between the primary and active firewall if those interfaces are also used to maintain the heartbeat/clustering protocol(s) to allow them to know which is primary. It would make sense for that traffic to use the physical (unique) mac addresses that belong to each firewall's interface(s). Otherwise that would be problematic for the switch as it would constantly have to update the mac address table (which wouldn't make any sense).
Is there a dedicated interface between the primary/secondary firewalls to pass heartbeat/clustering traffic or is it all done inband?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2020 11:41 AM
++Laugh++ I am not very familiar with the equipment as well... inherited from a project. "Don't you just love when that happens."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2020 08:47 AM
I have seen some example somewhere in Cisco Doc ...once i find it, i will post them; for now, I would recommend 3-4 chapters in older CCNP official cert guide book from cisco press. Here are Key points:
1. Use Rapid STP with command spanning-tree mode rapid (default is STP )
2. Determine the best switch to be Root switch and set Bridge Priority (spanning-tree vlan x priority 0)
3. Adjust ports costs to Root switch (spanning -tree vlan x cost x)
STP decisions are based on the following sequence of four conditions:
1. Lowest root bridge ID
2. Lowest root path cost to root bridge
3. Lowest sender bridge ID
4. Lowest sender port ID
Source: David Hucaby, CCNP_SWITCH_642-813_Official_Certification_Guide, Ciscopress, 2010
Regards, ML
**Please Rate All Helpful Responses **
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: