- Cisco Community
- Technology and Support
- Networking
- Switching
- Two networks behind ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Two networks behind ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 12:45 AM - edited 03-07-2019 03:45 AM
Dear all,
I would appreciate your help with configuring ASA!
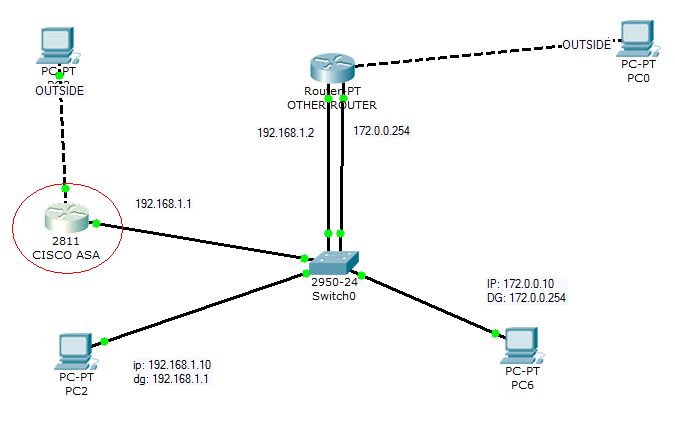
At first ASA was configured with inside (192.168.1.0 /24) and outside (NAT, VPN). Default gateway 192.168.1.1.
Recently new network has been added (172.0.0.0 /24) with default gateway 172.0.0.254. This network accesses the Internet via "OTHER ROUTER".
ASA has been configured with statis route 172.0.0.0 255.255.255.0 192.168.1.2. However, two networks are not able to communicate.
Could you please check this out and help me understanding the case? Thanks a lot!
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 03:24 AM
Hi
could you please give what is the importance of "same-security-traffic permit intra-interface" here.
Thanks
Vipin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 03:44 AM
Hi Vipin,
yep you're right as 192.168.1.0 network is directly connected the traffic isn't going to hairpin through the ASA.
I badly and too quickly read the post.
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 04:29 AM
Hi,
So what can be the possible solution here?
thanks
Vipin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 04:40 AM
Hi Alain,
Have similar environment as on example http://blogg.kvistofta.nu/cisco-asa-hairpinning/.
Have added:
static (inside,inside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0
static (inside,inside) 172.0.0.0 172.0.0.0 netmask 255.255.255.0
same-security-traffic permit inter-interface
Maybe I still need ACL?
access-list acl_inside extended permit ip 192.168.1.0 255.255.255.0 172.0.0.0 255.255.255.0
access-list acl_inside extended permit ip 172.0.0.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list acl_inside extended deny ip any any
!
access-group acl_inside in interface inside
Well, it is easy to play in testing environment, but cannot play around with productive (on remote location). That is why I appreciate your help all!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 04:51 AM
Hi sandra,
Finally if I understand correctly then my previous assumption was correct as the inside hosts have only a default gateway pointing to the ASA inside interface and so you have hairpinning and indeed your solution could work but with intra-interface as traffic is entering and leaving the same interface. But you could also try this instead without disrupting the network:
what about putting a static route to 172.0.0.0 subnet on inside host:
route add 172.0.0.0 mask 255.255.255.0 192.168.1.2 permanent
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 08:31 AM
Also, another option will be to set up trunking on the inside ASA interface and set ASA interface as default gw for both networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 04:42 AM
Hi,
Can the OP try to ping 172.0.0.10 from a machine into ASA inside subnet and do a traceroute also.
Can we also sniff on 172.0.0.10 and the inside machine we're trying to reach and post the capture file as well as ipconfig and arp cache output from both hosts.
Regards.
Alain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2011 07:35 AM
Hi,
Will set this evening some of suggested configuration; will keep you informed Thanks a lot !
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
