- Cisco Community
- Technology and Support
- Networking
- Switching
- VLAN access list not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VLAN access list not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 12:18 AM - edited 03-07-2019 08:43 AM
Extended IP access list VLAN20
10 permit tcp any any established
11 permit icmp any any
20 permit tcp any 192.168.20.0 0.0.0.255 eq 80
30 permit tcp any 192.168.20.0 0.0.0.255 eq 443
40 deny ip any any log
Extended IP access list VLAN30
10 permit tcp any any established
11 permit icmp any any
20 permit tcp any 192.168.30.0 0.0.0.255 eq 25 110
30 permit udp any 192.168.30.0 0.0.0.255 eq 53 123
40 deny ip any any log
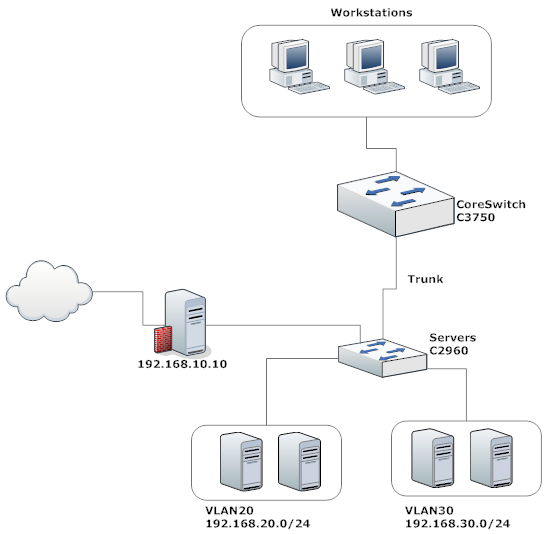
Above is the network diagram and access list for VLAN 20 and VLAN 30, applied on incoming direction of each valn.
But still able to access other port which is not on access list, tried changing the direction with no luck.
Inter vlan routing is enabled on CoreSwitch default router is 192.168.10.10
Any help would greatly be appreciated.
Thanks
Message was edited by: Ismail Fayaz
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 12:38 AM
Hi,
on which device and in which direction did you apply your ACLs ?
Regards.
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 12:49 AM
ACLs are applied on CoreSwitch with incoming direction. I also tried with outgoing direction.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 01:08 AM
Hi,
with the ACLs you provided outbound should work but what is puzzling me is the default-gateway that is connected to the 2960, why not link it to the 3750 as anyway I suppose the default-gateway of hosts is the corresponding SVI IP address on the 3750 ?
Could you provide your sanitized config please.
Regards.
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 03:36 AM
Yes, the default gateway of the hosts is the corresponding SVI IP address on 3750. Here is the config
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime localtime
service password-encryption
!
hostname CORESWITCH
!
boot-start-marker
boot-end-marker
!
switch 1 provision ws-c3750e-24td
system mtu routing 1500
ip routing
!
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
ip ssh source-interface Vlan1
ip ssh version 2
!
interface FastEthernet0
no ip address
no ip route-cache
no ip mroute-cache
shutdown
!
interface GigabitEthernet1/0/1
switchport access vlan 70
!
interface GigabitEthernet1/0/2
switchport access vlan 101
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
switchport access vlan 70
!
interface GigabitEthernet1/0/5
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/6
!
interface GigabitEthernet1/0/7
switchport trunk encapsulation dot1q
!
interface GigabitEthernet1/0/8
!
interface GigabitEthernet1/0/9
switchport access vlan 70
!
interface GigabitEthernet1/0/10
!
interface GigabitEthernet1/0/11
switchport access vlan 3
!
interface GigabitEthernet1/0/12
switchport access vlan 90
!
interface GigabitEthernet1/0/13
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/14
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/15
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/16
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/17
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/18
switchport access vlan 70
!
interface GigabitEthernet1/0/19
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/20
!
interface GigabitEthernet1/0/21
switchport access vlan 51
!
interface GigabitEthernet1/0/22
!
interface GigabitEthernet1/0/23
switchport access vlan 81
!
interface GigabitEthernet1/0/24
description Link to ServersSwitch
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface TenGigabitEthernet1/0/1
!
interface TenGigabitEthernet1/0/2
!
interface Vlan1
ip address 192.168.1.1 255.255.255.0
!
interface Vlan3
ip address 192.168.3.1 255.255.255.0
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
ip access-group VLAN20 in
no ip route-cache
no ip mroute-cache
!
interface Vlan30
ip address 192.168.30.1 255.255.255.0
ip access-group VLAN30 in
no ip route-cache
no ip mroute-cache
!
interface Vlan40
ip address 192.168.40.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan41
ip address 192.168.41.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan42
ip address 192.168.42.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan50
ip address 192.168.50.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan51
ip address 192.168.51.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan60
ip address 192.168.60.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan70
ip address 192.168.70.1 255.255.255.0
no ip route-cache
interface Vlan70
ip address 192.168.70.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan80
ip address 192.168.80.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan81
ip address 192.168.81.1 255.255.255.248
!
interface Vlan90
ip address 192.168.90.1 255.255.255.224
no ip route-cache
no ip mroute-cache
!
interface Vlan91
ip address 192.168.91.1 255.255.255.224
!
interface Vlan95
ip address 192.168.95.1 255.255.255.224
!
interface Vlan100
ip address 192.168.100.1 255.255.255.0
!
interface Vlan101
ip address 192.168.101.1 255.255.255.0
!
no ip http server
no ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 192.168.10.10 permanent
!
Extended IP access list VLAN20
10 permit tcp any any established
11 permit icmp any any
20 permit tcp any 192.168.20.0 0.0.0.255 eq 80
30 permit tcp any 192.168.20.0 0.0.0.255 eq 443
40 deny ip any any log
!
Extended IP access list VLAN30
10 permit tcp any any established
11 permit icmp any any
20 permit tcp any 192.168.30.0 0.0.0.255 eq 25 110
30 permit udp any 192.168.30.0 0.0.0.255 eq 53 123
40 deny ip any any log
!
logging esm config
no cdp advertise-v2
!
line con 0
logging synchronous
line vty 0 4
transport input ssh
line vty 5 15
transport input ssh
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2012 03:53 AM
Hi,
can you modify your ACLs like this:
no ip access-list extended VLAN20
ip access-list extended VLAN20
permit icmp any any
permit tcp 192.168.20.0 0.0.0.255 any eq 80
permit tcp 192.168.20.0 0.0.0.255 any eq 443
deny ip any any log
no ip access-list extended VLAN30
ip access-list extended VLAN30
permit icmp any any
permit tcp any 192.168.30.0 0.0.0.255 eq 25 110
permit udp 192.168.30.0 0.0.0.255 any eq 53 123
deny ip any any log
Please tell us exactly what you want to prohibit because the ACLs may be modified though.
Regards.
Alain
Don't forget to rate helpful posts.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
