- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: VRRP blocked on Catalyst 3650?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 06:21 AM
Hi, trying to configure failover on two OpenVPN Access Servers connected through a Catalyst 3650 on same VLAN, but failover isn't working. The OpenVPN guys say our switch is probably blocking VRRP traffic, but I dont know how to confirm if this is the case? From what little I know, VRRP uses a multicast address 224.0.0.18 and IP protocol number 112...it seems to me I may have to do something on the switch to enable this type of traffic to pass, but I'm not sure? Appreciate any insight anyone can give!
Solved! Go to Solution.
- Labels:
-
Catalyst 3000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 10:24 AM
No port-security or storm-control, here are the interface configs (same for both Hyper-V server switchport interfaces):
switchport trunk native vlan 2
switchport mode trunk
auto qos trust dscp
spanning-tree portfast
service-policy input AutoQos-4.0-Trust-Dscp-Input-Policy
service-policy output AutoQos-4.0-Output-Policy
There is nothing else special in the config...ip routing is enabled. Here is the sdm template info:
Showing SDM Template Info
This is the Advanced (low scale) template.
Number of VLANs: 4094
Unicast MAC addresses: 32768
Overflow Unicast MAC addresses: 512
IGMP and Multicast groups: 4096
Overflow IGMP and Multicast groups: 512
Directly connected routes: 32768
Indirect routes: 7680
Security Access Control Entries: 1536
QoS Access Control Entries: 3072
Policy Based Routing ACEs: 1024
Netflow ACEs: 1024
Input Microflow policer ACEs: 256
Output Microflow policer ACEs: 256
Flow SPAN ACEs: 256
Tunnels: 256
Control Plane Entries: 512
Input Netflow flows: 8192
Output Netflow flows: 16384
SGT/DGT entries: 4096
SGT/DGT Overflow entries: 512
These numbers are typical for L2 and IPv4 features.
Some features such as IPv6, use up double the entry size;
so only half as many entries can be created.
Like you said, its sounding like it's not an issue with the switch. I tried pinging 224.0.0.18 from the VPN server while listening on my machine with wireshark and I see the requests coming through, so clearly the switch is not blocking that traffic:
Appreciate the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 06:54 AM
Hello
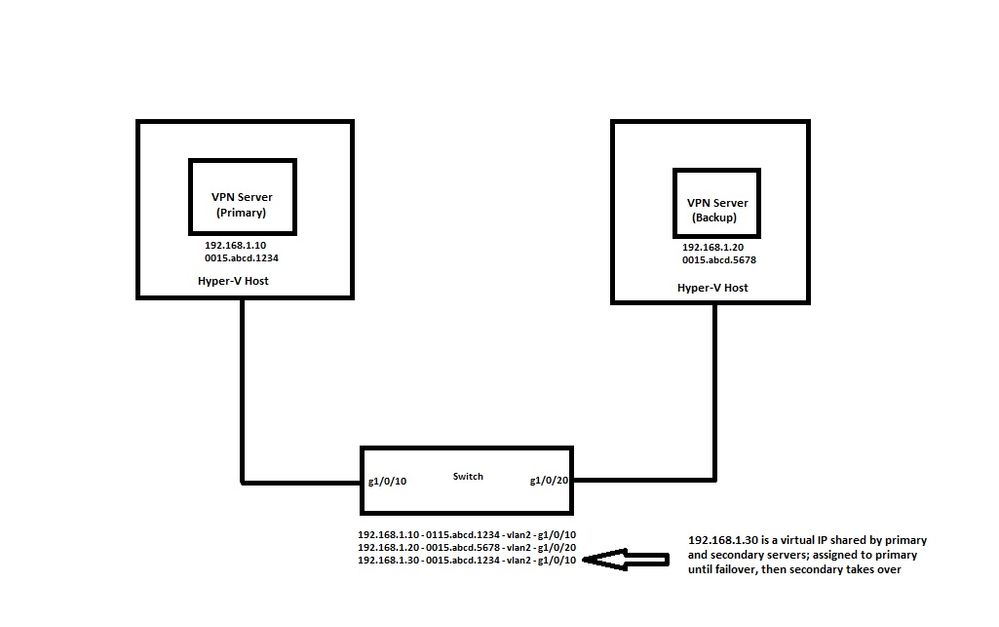
Do you have a topology diagram you can share in relation to this switch and the open vpn servers?
Maybe also share the output of the switch and the ip/ mac- address of the vpn servers
sh run
sh vlan brief
sh switch
sh mac-address table
sh arp
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 07:26 AM
Hi Paul, see below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 07:33 AM - edited 10-28-2020 07:34 AM
Hello
As the switch is acting a l2 interconnection between the vmhosts as long as ports gig1/0/10-20 are in the same acess vlan and that vlan is enabled on the switch then communication between the vmhost should be valid.
Can the vmhosts ping each other?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 07:44 AM
Yes, all regular traffic is passing between the two vmhosts, but I don't believe *multicast* traffic is being passed. I can't ping the VRRP multicast address (224.0.0.18) from either host, and running "tcpdump -eni any vrrp" command on either host shows no activity. The OpenVPN support tech says it's common for network equipment to not allow this kind of traffic so I'm wondering if I need to do any extra configuration on the switch to allow this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 08:50 AM
Hello
hence why i asked for you to post the outputs from those show commands
do you have any L2 port-security or storm-control applied to the switch ports if not then i would say it isn’t anything to do with the switch and more to do with the vms
Csn you ask confirm what sdm template you are using —
sh sdm prefer
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 10:24 AM
No port-security or storm-control, here are the interface configs (same for both Hyper-V server switchport interfaces):
switchport trunk native vlan 2
switchport mode trunk
auto qos trust dscp
spanning-tree portfast
service-policy input AutoQos-4.0-Trust-Dscp-Input-Policy
service-policy output AutoQos-4.0-Output-Policy
There is nothing else special in the config...ip routing is enabled. Here is the sdm template info:
Showing SDM Template Info
This is the Advanced (low scale) template.
Number of VLANs: 4094
Unicast MAC addresses: 32768
Overflow Unicast MAC addresses: 512
IGMP and Multicast groups: 4096
Overflow IGMP and Multicast groups: 512
Directly connected routes: 32768
Indirect routes: 7680
Security Access Control Entries: 1536
QoS Access Control Entries: 3072
Policy Based Routing ACEs: 1024
Netflow ACEs: 1024
Input Microflow policer ACEs: 256
Output Microflow policer ACEs: 256
Flow SPAN ACEs: 256
Tunnels: 256
Control Plane Entries: 512
Input Netflow flows: 8192
Output Netflow flows: 16384
SGT/DGT entries: 4096
SGT/DGT Overflow entries: 512
These numbers are typical for L2 and IPv4 features.
Some features such as IPv6, use up double the entry size;
so only half as many entries can be created.
Like you said, its sounding like it's not an issue with the switch. I tried pinging 224.0.0.18 from the VPN server while listening on my machine with wireshark and I see the requests coming through, so clearly the switch is not blocking that traffic:
Appreciate the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 12:52 PM
Hello
Why do you have ip routing enabled I thought this was just a host switch interconnecting the two vms? - So this switch has L3 SVI's correct , if so do you have any routed acls .
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: