- Cisco Community
- Technology and Support
- Collaboration
- TelePresence and Video Infrastructure
- Re: connection to webbridge 3 failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2021 07:11 PM
I have cms 3.2 installed
I have successfully installed the certificate chain which has client and server authentication.The webbridge3 url is not displaying any web page.
error: c2w://cms.domain.com:9999 connection failed ..
i have not been able to see where to enter guest url in cms 3.2. can you help?
Solved! Go to Solution.
- Labels:
-
Conferencing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2021 09:23 AM
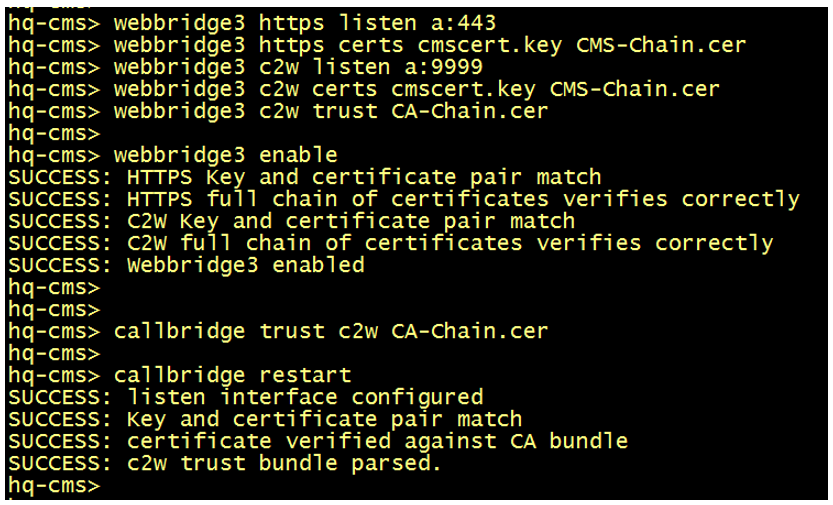
Configure the WebBridge3 with the following commands, you should all verifications are success once you enable the webbridge3 and restart the callbridge.
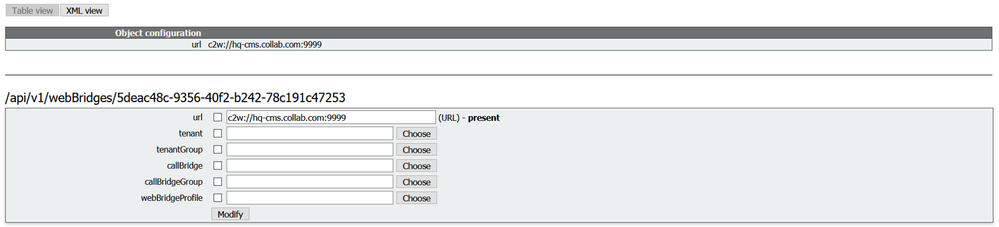
Then in the API, configure the link ("c2w://hq-cms.lab.local:9999") so that the Webbridge3 can connect to the CallBridge , the webbridge should resolve the IP address of the call bridge with DNS A record.
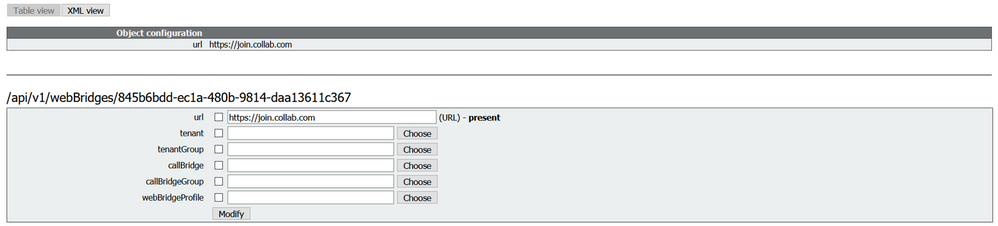
Configure the Guest URL in the same API.
For certificates requirements, you can check this article I wrote to see how to create these certificates safely.
https://ipdemystify.com/2020/10/31/cisco-meeting-server-certificate-requirement-demystified/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 06:03 AM
Hey,
have you already tried to resolve the error first?
Keep in mind, that the Call-Bridge also have to trust the webbridge cert (callbridge trust c2w <cert-chain-file>, then callbridge restart).
Have you also set the webbridge3 parameters for the normal WebRTC-page (webbridge3 https ...)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 01:55 PM
Yes,I have attempted to resolve it but still no success.
i do not understand this
"Have you also set the webbridge3 parameters for the normal WebRTC-page (webbridge3 https ...)?"
how do I set the above up?
i set up this using the API under the webbridge3
c2w://cms.fuotuoke.edu.ng:9999
NB:
I have set up the trusted certificate between call bridge and webbridge3 I will cross-check it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2021 11:11 PM
Hi,
Please see the screenshot attached.
For the connection to work, you have to configure 2 seperate connection settings for the webbridge3:
Line 1 in screenshot is for the WebRTC-Client to connect to the Webbridge:
webbridge3 https listen <interface>:<port> --> e.g. webbridge3 https listen a:443 webbridge3 https certs <key> <cert-chain-file> webbridge3 http-redirect enable --> enables redirect from port 80 to the https port you configured above.
Line 2 in screenshot is for the connection between Callbridge and Webbridge:
webbridge3 c2w listen <interface>:<port> --> e.g. webbridge3 c2w listen a:9999 webbridge3 c2w certs <key> <cert-chain-file> webbridge3 c2w trust <cert-chain-file> --> must contain the cert-chain, that signed the Callbridge cert webbridge3 enable
And then in the API, you have to configure the link ("c2w://cms.fuotuoke.edu.ng:9999") that you already have done.
I hope, that helps.
If not, we could also do a webex teams call.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 12:22 AM
shows all success.Webex call will be better.Let me know the time for your
availability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 03:51 AM
Wrote you a personal message with my email, so you can contact me via Webex.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 11:57 AM
I am using self signed certificates for Webbridge3.. could you please help me with configuration?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 12:19 PM
Read the response of bjoren to me on the necessary steps.
You need certificate chain for webbridge 3.You can make use of Mikrosoft windows server CA.Ensure you have server and client authentication keys.Generate certificate request and send to Microsoft CA.
To create certificate chain,you need the root certificate which trusts the server certificate.
Open a blank notepad,copy the contents of the root ca and paste in the blank notepad.Cope the contents of the server certificate and past in the notepad below -----end of ------- after that ,press enter to leave a space .then save the file as webbridge3chain.cer..
upload this certificate to the cms.follow the steps which I refered you to enabled webbridge3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 01:12 PM
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2021 11:40 PM - edited 08-11-2021 11:56 PM
Hi Muhammad,
As currently tested with my own CMS, I think you have to add the CN manually when generating the self-signed cert.
e.g. pki selfsigned <tag> CN:cms.test.com
This CN has to be in the API command, when you add the webbridge3:
POST to https://<ip-or-fqdn>:<port>/api/v1/webbridges Parameter: url --> c2w://<Webbrige 3 CN>:<Port>
The IP / FQDN of the above url has to be in the certificate (which you assign via CLI command "webbridge3 c2w certs <key> <cert-chain-file>")
But even if you have the CN in the cert, the connection won't establish with the following error:
C2W Peer 7FE8E88A2200 failed TLS handshake with error: self signed certificate
I hope, that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 08:35 AM
Apologies. I was away for a bit. I will check and update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2021 03:53 AM - edited 09-13-2021 04:24 AM
Hello
Can you post output CLI for command webbridge3 callbridge and webadmin?
UC-CMS-1> webadmin
Enabled : true
TLS listening interface : a
TLS listening port : 445
Key file : cmscert2yr.key
Certificate file : cmscert2y-chain.cer
HTTP redirect : Disabled
STATUS : webadmin running
UC-CMS-1>
UC-CMS-1> webbridge3
Enabled : true
HTTPS listening ports and interfaces : a:443
HTTPS Key file : cmscert2yr.key
HTTPS Full chain certificate file : cmscert2y-chain.cer
HTTPS Frame-Ancestors : none
HTTP redirect : Enabled, Port:80
C2W listening ports and interfaces : a:9999
C2W Key file : cmscert2yr.key
C2W Full chain certificate file : cmscert2y-chain.cer
C2W Trust bundle : ca-certificate-chain.cer
Beta options : none
UC-CMS-1>
UC-CMS-1> callbridge
Listening interfaces : a
Preferred interface : none
Key file : cmscert2yr.key
Certificate file : cmscert2y-chain.cer
Address : none
C2W trusted certs : ca-certificate-chain.cer
Callbridge cluster trusted certs : none
UC-CMS-1>
Well, for the sake of completeness
UC-CMS-1> scheduler
Enabled : true
Https interface : a
Https port : 8443
Https key file : cmscert2yr.key
Https certificate file : cmscert2y-chain.cer
C2W Key file : cmscert2yr.key
C2W Full chain certificate file : cmscert2y-chain.cer
C2W Trust bundle : ca-certificate-chain.cer
Email Server : mbx-1-msk.domain.ru
Email Port : 25
Email Username : no username
Email Protocol : smtp
Email Auth : disabled
Email StartTLS : disabled
Email Trust bundle : ca-certificate-chain.cer
UC-CMS-1>
cmscert2y-chain.cer it is a composite certificate consisting of the following cer files. Only Base 64 format!!!:
-----BEGIN CERTIFICATE-----
MIIFXDCCBESgAwIBAgIKQwRwJgACAADJbjANBgkqhkiG9w0BAQsFADBsMQswCQYD
VQQGEwJSVTESMBAGA1UEChMJTm92b3RyYW5zMRwwGgYDVQQLExNJbmZvcm1hdGlv
cer answer from Enterprise CA for performed earlier pki csr cmscert2yr CN:uc-cms-1.domain.ru OU:"IT Service" O:COMPANY L:MOSCOW ST:MOSCOW C:RU subjectAltName:xmpp.domain.ru,callbridge.domain.ru,join.domain.ru,webadmin.domain.ru,uc-cms-1.domain.ru,domain.ru
NgaehaEhaQNuojuKPH083aM1yYqSODVSWXVzWHRs8fyfPWPeUykJiS/I1fCNgI9L
RjX63TnDj74ajdhlSZ3NM+yvOf/e+tS+Iecz7yvaOFk=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIE1DCCA7ygAwIBAgIKYZz8yAABAAAABjANBgkqhkiG9w0BAQsFADBmMQswCQYD
VQQGEwJSVTESMBAGA1UEChMJTm92b3RyYW5zMRwwGgYDVQQLExNJbmZvcm1hdGlv
cer file Issue CA your Enterprise (export from Local Computer)
lfPdAtk6nUc3ptBN9P3XfpKrCPT4AN2Fz+OIsPfpXsq9bLCr5hkHIJeVHetmENaT
8j8s3q4dYlSRl8FQ8Swe95j7fKuYIeKDhYW6IevvpyKNPStIji8PHQ==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDzDCCArSgAwIBAgIQZmS+vKxEw4VPOGhH7HoaLTANBgkqhkiG9w0BAQsFADBm
MQswCQYDVQQGEwJSVTESMBAGA1UEChMJTm92b3RyYW5zMRwwGgYDVQQLExNJbmZv
cm1hdGlvbiBTeXN0ZW1zMSUwIwYDVQQDExxIQyBOb3ZvdHJhbnMgQ2xhc3MgMSBS
cer file Root CA your Enterprise (export from Local Computer)
9uDK8fKtvFc7oelelW3cWBG1/vXPKipgFyTjOPTUn7EU6jlY/U8eiDZcjw6KBkU0
Y9WmFbCjQyR0R3Lpi56oJw==
-----END CERTIFICATE-----
ca-certificate-chain.cer
-----BEGIN CERTIFICATE-----
cer file Issue CA your Enterprise (export from Local Computer)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
cer file Root CA your Enterprise (export from Local Computer)
-----END CERTIFICATE-----
Loaded chain from http://serverpki/certsrv wont' work! Only gluing in a notepad or copying with FAR Manager. The life of the certificate should not be more than two years
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2021 08:35 AM
Apologies. I will check. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2023 09:12 AM
C2W trusted certs : ca-certificate-chain.cer
That statement alone helped solve my issue. I did not see it as part of the commands when installing a new certificate. Thanks for the post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2021 09:23 AM
Configure the WebBridge3 with the following commands, you should all verifications are success once you enable the webbridge3 and restart the callbridge.
Then in the API, configure the link ("c2w://hq-cms.lab.local:9999") so that the Webbridge3 can connect to the CallBridge , the webbridge should resolve the IP address of the call bridge with DNS A record.
Configure the Guest URL in the same API.
For certificates requirements, you can check this article I wrote to see how to create these certificates safely.
https://ipdemystify.com/2020/10/31/cisco-meeting-server-certificate-requirement-demystified/
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide