- Cisco Community
- Technology and Support
- Collaboration
- TelePresence and Video Infrastructure
- Expressway-E SSL Cert Trial Work?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2014 08:07 PM - edited 03-18-2019 02:39 AM
Hi,
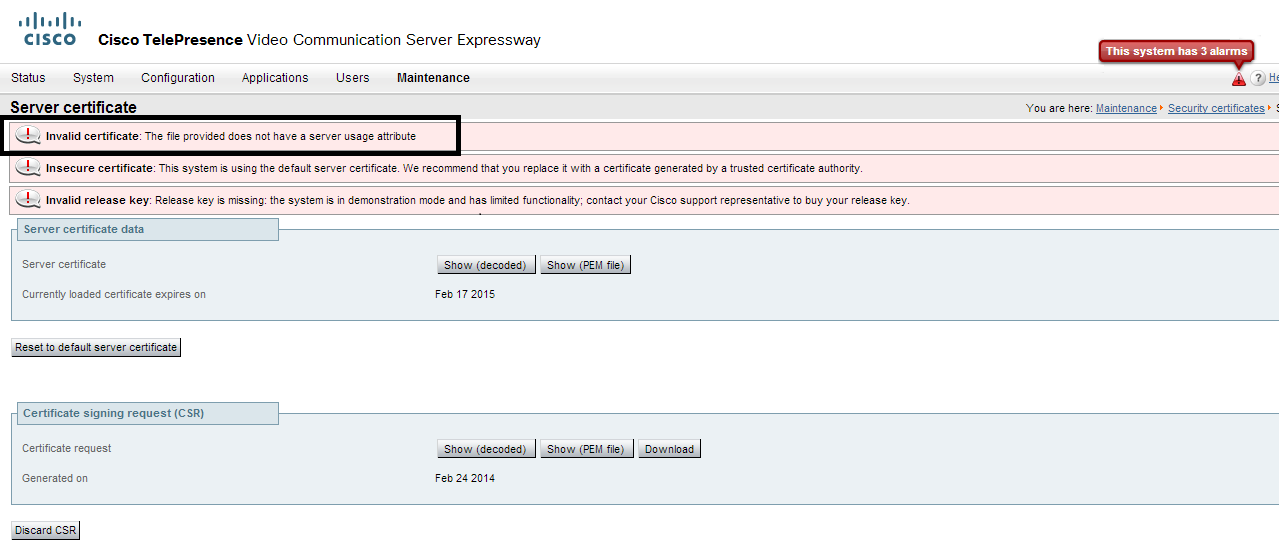
I just deployed the VCS 8.1 ova for the Expressway-C and Expressway-E about the demo of VPN-less Jabber. It is successful for me to configure the Expressway-C and the Expressway-E, but I cannot make the commnication between the "Traversal Server" (E) and the "Traversal Client" (C) with the Mobile Remote Access through the TLS, because it need the cert. as the validation. I want to use the the trial public CA to generate the certs, but I suffered on the cert. error; "The file provided does not have a server usage attribute".
PS: I am using the symantec trial cert. (https://trustcenter.websecurity.symantec.com/process/retail/trial_product_selector?uid=abf536a4864459d743f0fe26063fcac9&locale=VRSN_US&language=en)
Actually, it is successful to upload the Root CA provided by the symantec, but it is fail to upload the server cert.
How can I solve it out?
Solved! Go to Solution.
- Labels:
-
Room Endpoints
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2014 09:03 PM
Sign your own certificate using OpenSSL
If you want to use OpenSSL to create your own CA cert and sign your CSR, it is actually easier than you’d think.
Start at the bottom of p.12 of this document –
you can generate the CSR "certificate signing request" from the VCS and copy this file to your PC where you are running openssl.
You’ll need to follow the procedure twice. Once for Expressway-E and once for Expressway-C. Take the CA root cert that you generated and import it into the trusted list on both boxes, and then import your signed server cert on the appropriate box.
regards
Alok
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2014 08:31 PM
Hi,
to setup the TLS connection between Expressway-E and Expressway-C, its important that the certificate installed on the traversal server and traversal client should have two attributes i.e. client and server, and then only TLS will work.
you can use openssl to generate the certificates.
Regards
Alok
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2014 08:44 PM
Thanks for your reply!
You mean I can generate the self-signed from the openssl? Would u mind how can I do it from the Expressway-E? Really Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2014 09:03 PM
Sign your own certificate using OpenSSL
If you want to use OpenSSL to create your own CA cert and sign your CSR, it is actually easier than you’d think.
Start at the bottom of p.12 of this document –
you can generate the CSR "certificate signing request" from the VCS and copy this file to your PC where you are running openssl.
You’ll need to follow the procedure twice. Once for Expressway-E and once for Expressway-C. Take the CA root cert that you generated and import it into the trusted list on both boxes, and then import your signed server cert on the appropriate box.
regards
Alok
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 01:37 AM
Hi,
I can generate the certs. into the Expressway-C and th Expressway-E, but it still fail to trunk the zone from the "Traversal Server" (E) and the "Traversal Client" (C) with the Mobile Remote Access through the TLS.
Any idea? Atcually, I don't know wht can I import about the "TLS verify subject name"? That should be the Expressway-C Cert. "Subject Common Name"?
Expressway-C error: SIP: Failed to connect to
Expressway-E
| State | Failed |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 02:34 AM
yes, that's right. the CN in the certificate is what you define on the expressway-E.
can you tell me on the expressway-c under the traversal zone it is pointing to ip-address of expressway-e or its fqdn ? it should be fqdn of expressway-e defined under its certificate.
also what attributes are assigned to your certificate on expressway -E & C ??
regards
Alok
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 04:48 AM
Thanks for yr Hits! After I changed the FQDN as the Subject CN of the certs., then the TLS can be formed.
Now, the "Traversal Zone", UC to CUCM and Presence server are working right now.
Actually, the Jabber still cannot reg. without the VPN. I still have some confused matters as below:
1. How to identify the internal and the external domains
My Expressway-C, CUCM, Presence server domain is: company.local
My Expressway-E with dual networks domain is: company.com
As the outside Jabber, then I should type the
Actually: I just want to the jabber reg. to the CUCM, because that is the free.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2014 10:33 AM
Hi Edwin!
I've been experiencing the same issue, could you tell me how you resolve that issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2014 06:00 AM
For cucm and IMP server and expressway certs you need to do the following:
Generate CSR (tomcat)>generate CSR>send to CA to sign on all IMP and CUCM servers
Upload CA root cert as tomcat-trust
Upload signed cucm and IMP certs on all servers
Upload root CA cert to expressway e and c
Generate CSR for expwe and c, send to CA to sign and use web and client server template
Upload cert as server certs.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: