- Cisco Community
- Technology and Support
- Data Center and Cloud
- Unified Computing System (UCS)
- Unified Computing System Discussions
- Re: Configure switchport in access mode in Cisco Fabric Interconnect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configure switchport in access mode in Cisco Fabric Interconnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 02:30 PM - edited 06-18-2019 02:31 PM
Hi,
I'm very newbie to the Cisco Fabric Interconnect system and I've been searching how to configure a FI port with a VLAN in access mode so that it can be used as a second uplink to a Nexus 5K. I already configured the Nexus port, but I still can't find an appropiate way to configure an uplink port in access mode, and as the FI is in production and in fact it has already a port-channel uplink configured, I don't wanna mess up anything nor end by restarting the FI by mistake.
The FI model is 6248UP with system version 2.2(8g), so I'm using UCS Manager through Java.
Any ideas for the best way to proceed?
Thanks!
- Labels:
-
UCS Manager
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 03:27 PM
Hi @supportgns ,
I still can't find an appropiate way to configure an uplink port in access mode,
You don't need to, and in fact definitely don't WANT to.
Firstly, you need to understand that an FI is a special kind of switch, and acts more like a VMware vSwitch than a regular 802.1D switch. This is because it has Server ports, where it learns MAC addresses like a normal switch, and Uplink ports, where MAC addresses are not learned. Uplink ports are always trunk ports. When frames arrive from a server on a server port, they are sent up one of the uplink ports based on the source MAC address (ie the MAC of the server) so that frames from the one MAC are always sent on the port.
Typically an FI has only ONE uplink port, and that uplink port is a port-channel. Yes, it may have two or four cables, but it is the port-channelling algorithm that then sorts out which traffic is sent on which cable. As far as the FI is concerned in your case (because you say "in fact it has already a port-channel uplink configured") there is ONE uplink.
Now this is what worries me.
You say "I've been searching how to configure a FI port with a VLAN in access mode so that it can be used as a second uplink"
WHY?
And WHY would it be an ACCESS port?
If the port is going to the SAME Nexus 5K as the existing Port Channel, then you need to include this port in the port-channel, but remember the rules of port channelling (2, 4 or 8 uplinks per port-channel, and best practice would be the same number on each FI - if the upstream switches are configured as VPCs (best practice) then you MUST have the same number on each FI). And in this case it would be a TRUNK.
I've run out of ideas now, can't say more until I know more about what you are trying to achieve.
Q1. WHY do you want to do this?
Q2. WHY do you want to configure a port as an Access Port
[Notes/caveats:
- There is a third kind of port called a server port, but please don't do that unless you answer the above questions.
- The FIs CAN be turned into regular switches, but I really hope yours is not configured that way, if so everything I said above is wrong
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 04:13 PM
Hi @RedNectar
I was thinking about a second uplink in order to configure a dedicated link for a routed network (with a mask of e.g. /29), so that some of the VLANs that reside in a NSX world can be routed via this network (the "second uplink") by using OSPF.
So I was thinking about the idea of a separated, dedicated physical link that can carry all the OSPF traffic from these NSX networks. Separated in the meaning of being physically apart of the standard traffic (uplink in TRUNK mode) that goes out through the current port-channel uplink. Then the Nexus 5K takes care of any other OSPF routing.
Now, what you explained makes me understand it's perfectly possible to send this OSPF traffic through the current uplink by adding the routed network as a VLAN to the trunk, and adding another physical wire to the port-channel.
Please correct me if I'm wrong in something.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 05:13 PM
I see your point. And your suggestion:
it's perfectly possible to send this OSPF traffic through the current uplink by adding the routed network as a VLAN to the trunk, and adding another physical wire to the port-channel.
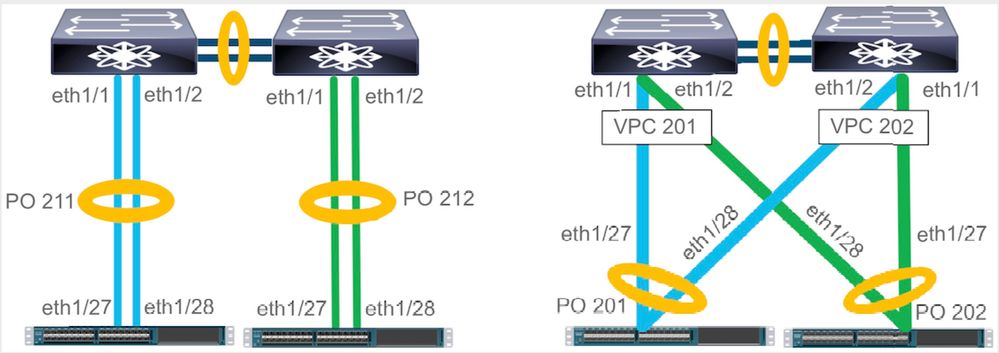
is a great idea. Exactly what I would reommend, just remember that if you alrady have two ports in your port-channel on each FI, you'll want to keep the same number of ports on each FI. In other words (looking at the diagram below), if your design is like the one on the left, and you add another link to PO211, I'd advise you add another to PO212 in case of fail-over. If your design is like the one on the right, it is a bit more complicated. You can't really add ONE link to PO201, you'd want to add two, one to each upstream Nexus switch. And then, you should also add two more links to PO202 as well for balance, so what starts out looking like adding one cable may turn out to be adding four!
I hope this helps
Don't forget to mark answers as correct if it solves your problem. This helps others find the correct answer if they search for the same problem
Forum Tips: 1. Paste images inline - don't attach. 2. Always mark helpful and correct answers, it helps others find what they need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2019 03:36 PM
As long as the VLAN you are attempting to add to the new uplink is not on the existing production port-channel, you add pin that single VLAN to the new uplink using LAN Uplinks manager:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: