- Cisco Community
- Technology and Support
- Security
- VPN
- 1841 as VPN concentrator in DMZ. Dynamic to static L2L or Remote
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
1841 as VPN concentrator in DMZ. Dynamic to static L2L or Remote
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 09:01 AM
Hi there,
I've spent the day trying some configurations for a 1841 router as VPN concentrator (not Easy VPN) in DMZ. Without any success
It could be easier to have an integrated DSL modem to 1841 but it's a project that costs me much money and i cannot purchase any HWIC card for now...
The project network topology follows :
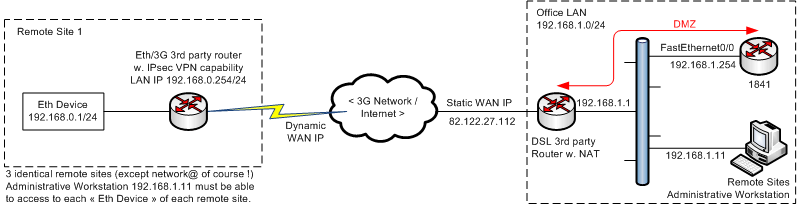
The 1841 is situated in a DMZ through an existing 3rd party DSL router with static WAN IP@.
I have 3 remote sites i would like to connect via VPN to my office network for administrative purpose. Each one gets a dynamic WAN IP@.
The 3G Routers in remote sites support IPsec VPN (see atteched screenshot for those routers'VPN settings GUI). They have NAT, Bridging and DMZ capability too.
At this time i don't know what is better according to this topology : L2L access or Remote access ?
[running-config sample]
[...]
!
no aaa new-model
!
[...]
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key testpresharedkey address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set TS esp-des esp-md5-hmac
!
crypto dynamic-map DYN-TS 10
! Incomplete
set transform-set TS
!
!
!
crypto map IPSEC 10 ipsec-isakmp dynamic DYN-TS
!
!
!
interface FastEthernet0/0
ip address 192.168.1.254 255.255.255.0
speed auto
half-duplex
no mop enabled
crypto map IPSEC
!
interface FastEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
ip default-gateway 192.168.1.1
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.1.1
[...]
[running-config sample ends]
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 09:19 AM
Hi Amaury,
Several things to check here, first on your 3G modem that hosts the VPN concentrator, are we sure we are forwarding all the needed ports and protocols to the router? Make sure ESP (portless protocol) is supported to be forwarded, UDP 500 and UDP 4500, second your remote end 3G modems, have the following enabled, IPSEC PFS and your router does not have this enabled, so make sure you add that to your dynamic map settup. As well these modems have the identity definition as the address defined, if you can disable this it would be better and also try using main mode rather than aggressive mode on these routers, see if that changes anything.
When all of these has been changed, go ahead and try to connect your tunnel and see on your VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 12:18 PM
Thanks for your answer Ivan,
I have corrected parameters in 3G router VPN GUI, you were right.
I cannot find any information about this DSL router but i think it doesn't support ESP, i cannot log any activity in debug crypto mode
Things are little bit more clear for me now even if still doesn't work. I will probably need to buy a HWIC-1ADSL card.
Thank you so much for your help and for the time you offered to me
Cheers,
Amaury
R1841#show crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1841#show crypto ipsec transform-set
Transform set DYN-TS: { esp-des esp-md5-hmac }
will negotiate = { Tunnel, },

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 12:32 PM
About the modem's identifier type I thought that could be removed but if it can't leave it as address rather than fqdn, for the phase 2 settings if you can't disable pfs then go ahead and add this line to your router on the dynamic crypto map:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 03:46 PM
When i turn debug crypto (engine, isakmp, ipsec, mib, routing) on, no activity is logged while 3G router is supposed to initiate VPN connection. That suggests to me that DSL router doesn't support ESP forward, and so that tunnel connection is not properly initiated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2011 03:53 PM
You need to try to pass any kind of traffic over this tunnel to get debugs, if you are not getting any debugs then probably UDP 500 is not reaching the router, UDP 500 is what is used to create the tunnel, ESP comes when passing traffic and will not be used unless the tunnel is negotiated. My advise go ahead and check the modem infront of the router, see if you can find any kind of logging that might show why traffic is not reaching the router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2011 01:15 PM
Hi Ivan !
I have explication now !
I tried a portscan from outside, and UDP 500 and 4500 appear to be closed !!
I have created allowing rules in FW of DSL router, both for IPsec, TCP 22, UDP 500 and 4500.
I'm able to open port 22 and connect ssh to router from outside but not 500 and 4500 while sockets appear to be open on router.
R1841#show ip sockets
Proto Remote Port Local Port In Out Stat TTY OutputIF
17 0.0.0.0 0 192.168.1.254 67 0 0 2211 0
17 --listen-- 192.168.1.254 500 0 0 11 0
17 --listen-- 192.168.1.254 4500 0 0 11 0
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: