- Cisco Community
- Technology and Support
- Security
- VPN
- Access to other sites from vpn client connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Access to other sites from vpn client connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2012 08:35 AM
Hello,
I have the following scenario:
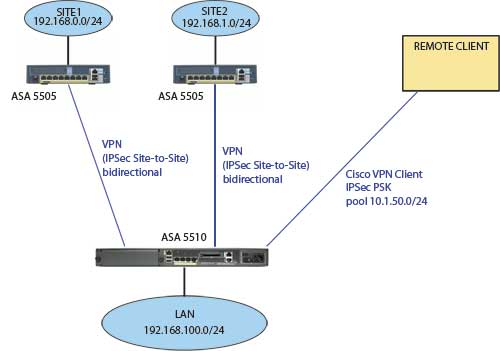
I have 30+ sites connected to 5510 betwenn bidirectional VPN. All computers from any site can acess 192.168.100.0/24 lan and vice-versa.
ASA 5510 offers external client connection (using cisco vpn client), and connecting to it, remote client can access 192.168.100.0/24 LAN.
But now I want that remote client access to the other sites throught his connection.
The connection assigns an ip of 10.1.50.0/24 to that remote clients, but they cannot reach, for example, 192.168.0.1.
I'm a bit lost with which NAT translation should I use, so if you could help me I would appreciate it.
(ASA 5505 are configured to accept remote VPN clients connections too, and assign them an IP from 10.1.50.0/24; I don't know if it could be a problem).
Thanks.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2012 11:10 AM
Hello Jordi,
To make this happen you need to configure some stuff:
same-security-traffic permit intra-interface
Are you running 8.4 (if yes)
object network VPN_clients
subnet 10.1.50.0 255.255.255.0
object network Site1
subnet 192.168.0.0 255.255.0
nat (outside,outside) source static VPN_clients VPN_clients destination static Site1 Site1
nat (outside,outside) source static Site1 Site1 destination static VPN_clients VPN_clients
Then if you have split-tunnel on your remote access client you will need to add those VPN sites there as well
Regards,
Any other question..Sure...Just remember to rate all of the helpful posts
Julio
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2012 08:14 AM
Hi Julio, thanks for your answer.
I'm running 8.2(5), so I think that command won't run, as are "past 8.3 version".
I supose I have to put nat rules in the 5510, don't I have to change anything from 5510 (192.168.0.0/24)?
I have split-tunnel, but I don't understand what you mean with "you will need to add those VPN sites there as well".
Thanks,
Jordi.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2012 09:19 AM
Hello Jordi.
So 8.2 speaking
access-list U-Turn permit ip 192.168.0.0 255.255.255.0 10.1.50.0 255.255.255.0
access-list U-Turn permit ip 10.1.50.0 255.255.255.0 192.168.0.0 255.255.255.0
Nat (outside) 1 .access-list U-Turn
global (outside) 1 interface
same-security-traffic permit intra-interface
Now on the Split tunnel for the remote access you should include the other VPN subnets IP
Lets say you have the following Setup
group-policy remote access attributes
split-tunnel-network-list value test
access-list test standard permit 192.168.100.0 255.255.255.0
access-list test standard permit 192.168.0.0 255.255.255.0
access-list test standard permit other_vpn_subnet
Regards,
Any other question..Sure...Just remember to rate all of the helpful posts
Senior Network Security and Core Specialist
CCIE #42930, 2xCCNP, JNCIP-SEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2012 01:11 AM
Hello Julio,
I run the config you told me, but I still cannot ping an inside host of a remote site from an vpn client.
I don't know if I need to do another configuration in ACLs, but I don't see any block.
Here is the config of my 5510, if you see any error please tell me:
names
name 192.168.10.0 site1
name 192.168.11.0 site2
name 192.168.12.0 site3
name 192.168.13.0 siten
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address o.o.o.o 255.255.240.0
!
interface Ethernet0/1
nameif Inside
security-level 100
ip address 192.168.254.1 255.255.255.0
!
interface Ethernet0/2
description LAN/STATE Failover Interface
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
ftp mode passive
clock timezone CEST 1
access-list Outside_1_cryptomap extended permit ip 192.168.254.0 255.255.255.0 site1 255.255.255.0
access-list Inside_nat0_outbound extended permit ip 192.168.254.0 255.255.255.0 site2 255.255.255.0
access-list Inside_nat0_outbound extended permit ip 192.168.254.0 255.255.255.0 site3 255.255.255.0
access-list Inside_nat0_outbound extended permit ip 192.168.254.0 255.255.255.0 siten 255.255.255.0
access-list Inside_nat0_outbound_1 extended permit ip 192.168.254.0 255.255.255.0 site1 255.255.255.0
access-list Inside_nat0_outbound_1 extended permit ip 192.168.254.0 255.255.255.0 site2 255.255.255.0
access-list Inside_nat0_outbound_1 extended permit ip 192.168.254.0 255.255.255.0 site3 255.255.255.0
access-list Inside_nat0_outbound_1 extended permit ip 192.168.254.0 255.255.255.0 siten 255.255.255.0
access-list Outside_2_cryptomap extended permit ip 192.168.254.0 255.255.255.0 site1 255.255.255.0
access-list Outside_3_cryptomap extended permit ip 192.168.254.0 255.255.255.0 site2 255.255.255.0
access-list Outside_4_cryptomap extended permit ip 192.168.254.0 255.255.255.0 site3 255.255.255.0
access-list Outside_5_cryptomap extended permit ip 192.168.254.0 255.255.255.0 siten 255.255.255.0
access-list Inside_access_in extended permit ip 192.168.254.0 255.255.255.0 any
access-list Inside_access_in extended permit tcp host 192.168.254.9 host o.o.o.o eq www
access-list Outside_access_in extended permit ip any any
access-list Outside_access_in extended permit tcp host 192.168.254.9 host o.o.o.o eq www
access-list Inside_nat_static extended permit tcp host 192.168.254.5 eq pop3 any
access-list Inside_nat_static_1 extended permit tcp host 192.168.254.5 eq imap4 any
access-list Inside_nat_static_2 extended permit tcp host 192.168.254.5 eq https any
access-list Inside standard permit 192.168.254.0 255.255.255.0
access-list Outside_cryptomap extended permit ip 192.168.254.0 255.255.255.0 Lloret 255.255.255.0
access-list Inside_nat_static_3 extended permit tcp host 192.168.254.5 eq smtp any
access-list Inside_nat_static_4 extended permit tcp host 192.168.254.5 eq domain any
access-list Inside_nat_static_5 extended permit tcp host 192.168.254.5 eq www any
access-list Inside_nat_static_6 extended permit tcp host 192.168.254.5 eq 135 any
access-list Inside_nat_static_7 extended permit tcp host 192.168.254.5 eq 587 any
access-list Inside_nat_static_8 extended permit tcp host 192.168.254.5 eq 995 any
access-list Inside_nat_static_9 extended permit udp host 192.168.254.5 eq domain any
access-list Inside_nat_static_10 extended permit tcp host 192.168.254.5 eq 993 any
access-list Inside_nat_static_11 remark LDAP GC
access-list Inside_nat_static_11 extended permit tcp host 192.168.254.5 eq 3268 any
access-list Inside_nat_static_12 extended permit tcp host 192.168.254.5 eq ldaps any
access-list Inside_nat_static_13 extended permit tcp host 192.168.254.5 eq 3269 any
pager lines 24
logging enable
logging asdm informational
mtu Outside 1500
mtu Inside 1500
mtu management 1500
ip local pool Pool 10.1.50.1-10.1.50.200 mask 255.255.255.0
failover
failover lan unit secondary
failover lan interface Failover Ethernet0/2
failover key *****
failover link Failover Ethernet0/2
failover interface ip Failover 10.10.10.1 255.255.255.252 standby 10.10.10.2
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (Outside) 1 interface
nat (Inside) 0 access-list Inside_nat0_outbound_1
nat (Inside) 1 192.168.254.0 255.255.255.0
static (Inside,Outside) tcp interface pop3 access-list Inside_nat_static
static (Inside,Outside) tcp interface imap4 access-list Inside_nat_static_1
static (Inside,Outside) tcp interface https access-list Inside_nat_static_2
static (Inside,Outside) tcp interface smtp access-list Inside_nat_static_3
static (Inside,Outside) tcp interface domain access-list Inside_nat_static_4
static (Inside,Outside) tcp interface www access-list Inside_nat_static_5
static (Inside,Outside) tcp interface 135 access-list Inside_nat_static_6
static (Inside,Outside) tcp interface 587 access-list Inside_nat_static_7
static (Inside,Outside) tcp interface 995 access-list Inside_nat_static_8
static (Inside,Outside) udp interface domain access-list Inside_nat_static_9
static (Inside,Outside) tcp interface 993 access-list Inside_nat_static_10
static (Inside,Outside) tcp interface 3268 access-list Inside_nat_static_11
static (Inside,Outside) tcp interface ldaps access-list Inside_nat_static_12
static (Inside,Outside) tcp interface 3269 access-list Inside_nat_static_13
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
route Outside 0.0.0.0 0.0.0.0 o.o.o.o 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication http console LOCAL
aaa authorization command LOCAL
aaa authorization exec authentication-server
http server enable 444
http 192.168.1.0 255.255.255.0 management
http 192.168.254.0 255.255.255.0 Inside
http x.x.x.x 255.255.255.255 Outside
http 10.1.50.0 255.255.255.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map Outsiap 19 match address Outside_19_cryptomap
crypto map Outside_map 1 match address Outside_1_cryptomap
crypto map Outside_map 1 set pfs
crypto map Outside_map 1 set peer ipsite1
crypto map Outside_map 1 set transform-set ESP-AES-128-SHA
crypto map Outside_map 2 match address Outside_2_cryptomap
crypto map Outside_map 2 set pfs
crypto map Outside_map 2 set peer ipsite2
crypto map Outside_map 2 set transform-set ESP-AES-128-SHA
crypto map Outside_map 3 match address Outside_3_cryptomap
crypto map Outside_map 3 set pfs
crypto map Outside_map 3 set peer ipsite3
crypto map Outside_map 3 set transform-set ESP-AES-128-SHA
crypto map Outside_map 4 match address Outside_4_cryptomap
crypto map Outside_map 4 set pfs
crypto map Outside_map 4 set peer ipsiten
crypto map Outside_map 4 set transform-set ESP-AES-128-SHA
crypto map Outside_map 5 match address Outside_5_cryptomap
crypto map Outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map Outside_map interface Outside
crypto isakmp enable Outside
crypto isakmp policy 10
authentication pre-share
encryption aes
hash sha
group 5
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime none
telnet l.l.l.l 255.255.255.255 Outside
telnet timeout 5
ssh x.x.x.x 255.255.255.255 Outside
ssh timeout 5
console timeout 0
management-access Inside
dhcpd address 192.168.254.100-192.168.254.200 Inside
dhcpd dns 192.168.254.5 interface Inside
dhcpd domain DOMAIN interface Inside
dhcpd enable Inside
!
dhcpd address 192.168.1.2-192.168.1.254 management
!
vpn load-balancing
priority 3
interface lbpublic Outside
interface lbprivate Inside
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy VPNGroup internal
group-policy VPNGroup attributes
dns-server value 192.168.254.5
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Inside
default-domain value domain.net
username vpnuser password ******* encrypted
username vpnuser attributes
service-type remote-access
username admin-user password **** encrypted privilege 15
tunnel-group ipsite1 type ipsec-l2l
tunnel-group ipsite1 ipsec-attributes
pre-shared-key *
tunnel-group ipsite2 type ipsec-l2l
tunnel-group ipsite2 ipsec-attributes
pre-shared-key *
tunnel-group ipsite3 type ipsec-l2l
tunnel-group ipsite3 ipsec-attributes
pre-shared-key *
tunnel-group ipsiten type ipsec-l2l
tunnel-group ipsiten ipsec-attributes
pre-shared-key *
tunnel-group VPNGroup type remote-access
tunnel-group VPNGroup general-attributes
address-pool Pool
default-group-policy VPNGroup
tunnel-group VPNGroup ipsec-attributes
pre-shared-key *
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Thank you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide