- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect VPN can't access local LAN on Outside interface of ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 01:13 PM - edited 02-21-2020 09:37 PM
I have the following setup.
Fiber -> (Outside Interface) ISR Router (Inside Interface) -> Switch -> (Outside Interface) ASA5506
The 3800 ISR Router has a one to one NAT configured to 192.168.10.2 which is the address assigned to the outside interface of the ASA5506.
I have created an internal network on the ASA of 192.168.15.0/24 and have connected a laptop to an interface port on the ASA. The laptop gets an IP address from DHCP, lets call it 192.168.15.100. I can browse the internet with this laptop as well as access the 192.168.10.0/24 subnet without any issues.
Here's where things get complicated and I'll admit I may be in way over my head here because I've never configured an ASA before.
I used the Wizard in ADSM to configure AnyConnect VPN. I was successfully able to connect from a Windows computer to the VPN but is was not able to connect to the internet or any of the internal networks. I enabled split tunneling and added the 192.168.10.0/24 subnet which then allowed the internet to work but I still can't connect to any PC's on the 192.168.10.0/24 subnet. However, I am able to ping the 192.168.10.2 address which is the outside interface of the ASA.
I'm pretty confused and feel extremely defeated at this point. Any help would be much appreciated.
Thanks
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 06:12 AM
Looks like your ASA config was redirecting you to the outside without any NAT. This means that the router was seeing the packet, but had no route to send a response back to the ASA. The routers default route probably sent it outbound and was dropped after that. You can fix this the way you did, or have the ASA NAT traffic going to the outside interface with a dynamic NAT rule. Either way works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 05:03 AM
Few things you would need to do:
1) Enable "same-security-permit intra-interface". Allows VPN traffic to u-turn on the outside interface
2) Add both 192.168.10.0 and 15.0 into the split tunnel.
3) Configure NAT exemption rules, if you have dynamic NAT on the ASA. The NAT should look something like this:
nat (outside, outside) source static VPN-pool VPN-pool destination static obj-192.168.10.0 obj-192.68.10.0 no-proxy-arp route-lookup
nat (outside, inside) source static VPN-pool VPN-pool destination static obj-192.168.15.0 obj-192.68.15.0 no-proxy-arp route-lookup
4) Make sure that the router has route back to the ASA for 192.168.15.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 11:31 AM
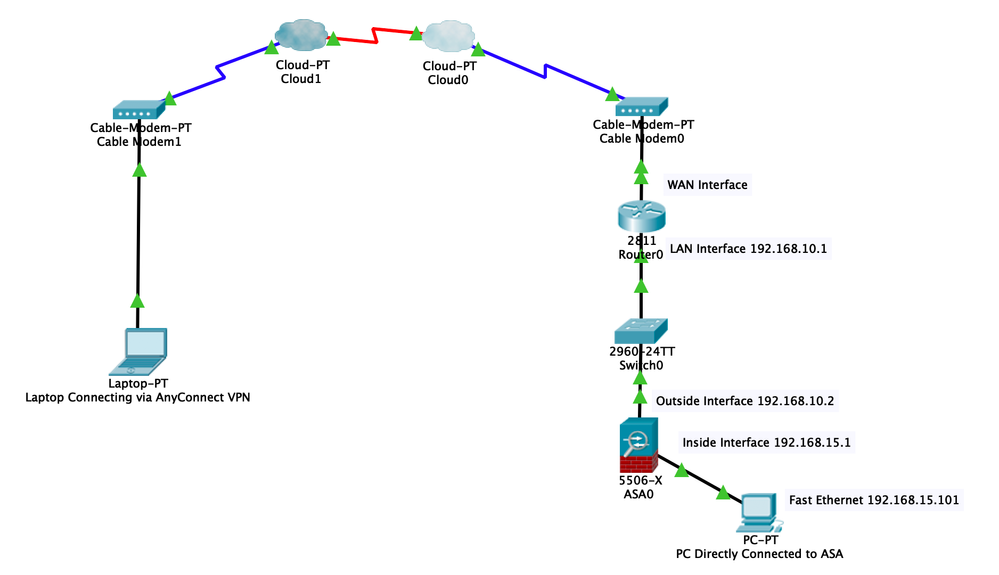
Hey thanks for the reply. I've tried that, still not working. My config is below, I've also included a diagram to show how things are connected.
Laptop Connecting via AnyConnect VPN:
Connects to VPN
Split tunnel is working because all traffic that is not 192.168.10.0 or 192.168.15.0 is being routed over local LAN
From that laptop I can ping 192.168.10.2 which is the outside interface of the ASA but it doesn't seem to get past that.
PC Directly Connected to ASA:
Can get to the internet
Can ping the client connected via AnyConnect (Laptop-PT)
Can ping everything except 192.168.10.2 (Outside interface of ASA)
CP-ASA-01# sh run
: Saved
:
: Serial Number: JAD22250LDX
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
:
ASA Version 9.8(2)
!
hostname CP-ASA-01
domain-name corp.somedomain.com
enable password $sha512$5000$+6pLheEdKMxEA8Ch7B7VFQ==$oqr6K+ECsigfoLkmtNOX1Q== pbkdf2
names
ip local pool AnyConnectVPN-Pool 192.168.15.50-192.168.15.99 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 192.168.10.2 255.255.255.0
!
interface GigabitEthernet1/2
bridge-group 1
nameif inside_1
security-level 100
!
interface GigabitEthernet1/3
bridge-group 1
nameif inside_2
security-level 100
!
interface GigabitEthernet1/4
bridge-group 1
nameif inside_3
security-level 100
!
interface GigabitEthernet1/5
bridge-group 1
nameif inside_4
security-level 100
!
interface GigabitEthernet1/6
bridge-group 1
nameif inside_5
security-level 100
!
interface GigabitEthernet1/7
bridge-group 1
nameif inside_6
security-level 100
!
interface GigabitEthernet1/8
bridge-group 1
nameif inside_7
security-level 100
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.15.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name corp.somedomain.com
same-security-traffic permit inter-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network obj-192.168.15.0
subnet 192.168.15.0 255.255.255.0
object network obj-192.168.10.0
subnet 192.168.10.0 255.255.255.0
access-list SplitTunnel standard permit 192.168.10.0 255.255.255.0
access-list SplitTunnel standard permit 192.168.15.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside_1 1500
mtu inside_2 1500
mtu inside_3 1500
mtu inside_4 1500
mtu inside_5 1500
mtu inside_6 1500
mtu inside_7 1500
no failover
no monitor-interface inside
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (any,outside) source dynamic any interface
nat (any,outside) source static any any destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
nat (any,outside) source static any any destination static obj-192.168.15.0 obj-192.168.15.0 no-proxy-arp route-lookup
!
object network obj_any1
nat (inside_1,outside) dynamic interface
object network obj_any2
nat (inside_2,outside) dynamic interface
object network obj_any3
nat (inside_3,outside) dynamic interface
object network obj_any4
nat (inside_4,outside) dynamic interface
object network obj_any5
nat (inside_5,outside) dynamic interface
object network obj_any6
nat (inside_6,outside) dynamic interface
object network obj_any7
nat (inside_7,outside) dynamic interface
route outside 0.0.0.0 0.0.0.0 192.168.10.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
aaa-server ActiveDirectory protocol ldap
aaa-server ActiveDirectory (outside) host 192.168.10.40
timeout 5
ldap-base-dn dc=corp,dc=somedomain,dc=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn administrator@corp.somedomain.com
server-type microsoft
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 192.168.15.0 255.255.255.0 inside_1
http 192.168.15.0 255.255.255.0 inside_2
http 192.168.15.0 255.255.255.0 inside_3
http 192.168.15.0 255.255.255.0 inside_4
http 192.168.15.0 255.255.255.0 inside_5
http 192.168.15.0 255.255.255.0 inside_6
http 192.168.15.0 255.255.255.0 inside_7
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
crl configure
crypto ca trustpoint SSL-Trustpoint
enrollment terminal
fqdn vpn.somedomain.com
subject-name CN=vpn.somedomain.com,OU=IT,O=Some Company Inc.,C=US,St=FL,L=Some City,EA=its@somedomain.com
keypair SSL-Keypair
crl configure
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.15.0 255.255.255.0 inside_7
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.15.100-192.168.15.254 inside
dhcpd dns 192.168.10.40 192.168.10.41 interface inside
dhcpd domain corp.somedomain.com interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point SSL-Trustpoint outside
ssl trust-point SSL-Trustpoint inside_1
ssl trust-point SSL-Trustpoint inside_2
ssl trust-point SSL-Trustpoint inside_3
ssl trust-point SSL-Trustpoint inside_4
ssl trust-point SSL-Trustpoint inside_5
ssl trust-point SSL-Trustpoint inside_6
ssl trust-point SSL-Trustpoint inside_7
ssl trust-point SSL-Trustpoint inside
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.6.00362-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_AnyConnectVPN internal
group-policy GroupPolicy_AnyConnectVPN attributes
wins-server none
dns-server value 192.168.10.40 192.168.10.41
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SplitTunnel
default-domain value corp.somedomain.com
dynamic-access-policy-record DfltAccessPolicy
tunnel-group AnyConnectVPN type remote-access
tunnel-group AnyConnectVPN general-attributes
address-pool AnyConnectVPN-Pool
authentication-server-group ActiveDirectory LOCAL
default-group-policy GroupPolicy_AnyConnectVPN
tunnel-group AnyConnectVPN webvpn-attributes
group-alias AnyConnectVPN enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
service call-home
call-home reporting anonymous
call-home
profile CiscoTAC-1
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:6b0a54428b0a7e87f47fb832a9309b4a
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 05:54 AM
Why do you have this statement?
nat (any,outside) source dynamic any interface
This may be redirecting your inside traffic to the outside. If you are doing split tunneling, this rule is not required. If you really need this rule for some other purpose, try moving the dynamic NAT below the 2 static rules below:
nat (any,outside) source static any any destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup nat (any,outside) source static any any destination static obj-192.168.15.0 obj-192.168.15.0 no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 06:29 AM
In either case moving the NAT rule or removing it completely had no effect on the VPN user having access to the 192.168.10.0 network.
Any other ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 07:32 AM
Thanks for testing. I noticed that you have the static NAT rule source and destination reversed. So the re-ordering did not help since the VPN traffic never hot these rules. Try changing the rule to the below:
nat (any,outside) source static obj-192.168.10.0 obj-192.168.10.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup nat (any,outside) source static static obj-192.168.15.0 obj-192.168.15.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
Using obj-192.168.10.0 instead of any to keep it more specific.
Also, Can you use a different subnet other than 192.168.10.0 for your VPN pool? This way there are no conflicts between the rules for the outside subnet and the VPN pool.
Also, run a packet tracer as seen below to simulate the packet :
packet-tracer input outside icmp <vpn-client-ip> 8 0 <ip-in-inside-subnet> decrypted detailed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 07:55 AM
Thank you so much for working with me on this.
When I entered this statement
nat (any,outside) source static obj-192.168.10.0 obj-192.168.10.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
I received the following message:
Warning: Pool (192.168.10.0-192.168.10.255) overlap with existing pool.
It still added the NAT rule, not sure if that’s a problem though
After adding this NAT rule I tested from the laptop directly connected to the ASA and was still able to get access to the outside.
When I entered this statement
nat (any,outside) source static obj-192.168.15.0 obj-192.168.15.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
I was no longer able to access the outside
Also, my VPN Pool is using 192.168.15.50 – 192.168.15.99
Below is the packet tracer output
CP-ASA-01(config)# packet-tracer input outside icmp 192.168.15.50 8 0 192.168.10.1 detailed
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 192.168.10.1 using egress ifc outside
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (any,outside) source static obj-192.168.15.0 obj-192.168.15.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface outside
Untranslate 192.168.10.1/0 to 192.168.10.1/0
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (any,outside) source static obj-192.168.15.0 obj-192.168.15.0 destination static obj-192.168.10.0 obj-192.168.10.0 no-proxy-arp route-lookup
Additional Information:
Static translate 192.168.15.50/0 to 192.168.15.50/0
Forward Flow based lookup yields rule:
in id=0x7f49eae3e5d0, priority=6, domain=nat, deny=false
hits=553, user_data=0x7f49eadc9200, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.15.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=192.168.10.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=outside
Phase: 4
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f49e8db8770, priority=3, domain=permit, deny=false
hits=536, user_data=0x0, cs_id=0x0, flags=0x4000, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=outside
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f49e7edbd00, priority=0, domain=nat-per-session, deny=true
hits=8447, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f49e8b73410, priority=0, domain=inspect-ip-options, deny=true
hits=6607, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 7
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f49eadf9430, priority=79, domain=punt, deny=true
hits=60, user_data=0x7f49e7ad5430, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.15.50, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 8
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f49eade3e10, priority=71, domain=svc-ib-tunnel-flow, deny=false
hits=62, user_data=0x22f1000, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=192.168.15.50, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 09:09 AM
@cfletcher32 wrote:
Also, my VPN Pool is using 192.168.15.50 – 192.168.15.99
Sorry, I misread this earlier. Your NAT rule should be:
nat (any,outside) source static obj-192.168.10.0 obj-192.168.10.0 destination static obj-192.168.15.0 obj-192.168.15.0 no-proxy-arp route-lookup
nat (any,outside) source static obj-192.168.15.0 obj-192.168.15.0 destination static obj-192.168.15.0 obj-192.168.15.0 no-proxy-arp route-lookup
Your destination ip address should be your VPN pool/subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 09:45 AM
Those are now the only 2 NAT rules.
Here’s what’s happening..
The laptop directly connected to the ASA:
IP Address: 192.168.15.101 (assigned from DHCP)
Can ping everything, except for the outside interface on the ASA 192.168.10.2 which seems to be fine.
Can ping the Anyconnect user with IP Address 192.168.15.50
The laptop using Anyconnect to remotely connect
IP Address: 192.168.15.50 (assigned by DHCP from the VPN Pool)
Can ping 192.168.10.2 (the outside interface of the ASA)
Can ping the laptop that is directly connected to the ASA with IP address 192.168.15.101
Cannot ping any other hosts on the 192.168.10.0 network. This is what I really need the remote users to have access to.
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 01:05 PM
Ok, so I got it working, I'm not sure why so maybe someone can help explain this to me.
I made a modification to the routers config.
I had a default route 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx being my ISP gateway)
I added a static route 192.168.15.0 255.255.255.0 192.168.10.2
Again 192.168.10.2 is the outside interface of the ASA
15.0 is the internal network of the ASA
15.50 is the ip assigned to the AnyConnect user
I'm trying to ping 192.168.10.45 which is a host connected to a switch that is connected to the inside interface of the router 192.168.10.1
Why would adding this particular static route allow the AnyConnect user to ping 192.168.10.45? I mean I'm glad its working but I would like to understand why.
Thanks for all the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 06:12 AM
Looks like your ASA config was redirecting you to the outside without any NAT. This means that the router was seeing the packet, but had no route to send a response back to the ASA. The routers default route probably sent it outbound and was dropped after that. You can fix this the way you did, or have the ASA NAT traffic going to the outside interface with a dynamic NAT rule. Either way works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 06:14 AM
That makes total sense.
Thank you so much for all of your help.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide