- Cisco Community
- Technology and Support
- Security
- VPN
- Certificate Auth not validating client has private key
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2019 03:22 PM
Hi All.
Our goal is to ensure the AnyConnect VPN is only able to be used by corporate devices.
Our expectation is that we can use Group Policy (or similar) to push a certificate to all computers that connect to the VPN, and this certificate is validated by the ASA.
We desire the certificate to be non-exportable so that it cant be used on another computer.
We create our internal certificates using XCA (Like OpenSSL) and have an internal CA and intermediate CA already configured.
Using XCA I have created a CA, an Intermediate CA, and a 'client' certificate.
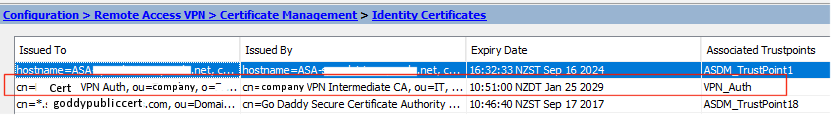
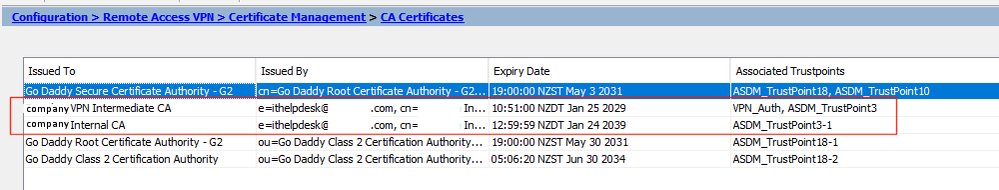
On the ASA I have installed the client cert and the CA's
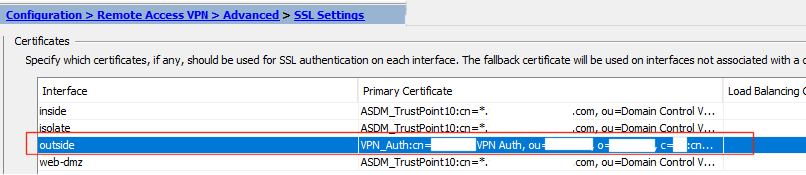
And on the SSL settings I have configured the outside interface to use this identity certificate
And I have installed the client certificate onto the test computer
Now when I connect using the new VPN Profile I have created, it prompts me for the certificate, and it connects succesfully.
If I select a random certificate, it does not connect. As expected
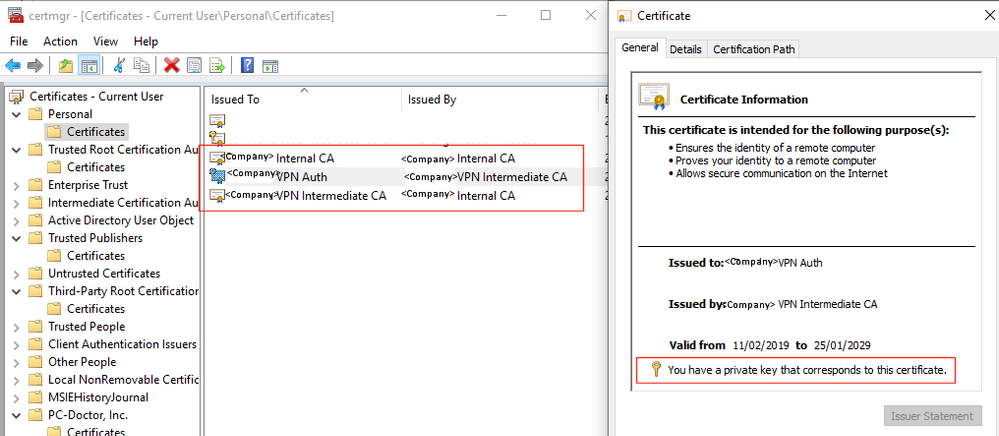
The problem is such: using windows certificate manager I can export the certificate off the computer without the private key. and this exported (keyless) certificate can then be installed on another computer and still connects
It seems the ASA is not validating that the private key is present in the client computer.
I suspect this is something to do with the Certificate Matching or Certificate Pinning or something in the AnyConnect Client Profile but I cant seem to get it to work.
This guide has been pretty helpful
But it even in this guide it shows screenshots of the client certificate without any private key.
Can someone point me in the right direction for validating the private key on the client? Cheers!
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2019 09:34 PM
The private key won't be validated by ASA and that is the concept of PKI.
In certificate authentication for VPN, the certificate it used for
authentication only. Technically, this means that the certificate will be
signed by the private key of the CA. When this certificate is sent to ASA
during key authentication phase, ASA will verify the signature of the
certificate by the CA using the CA Public key that is imported in ASA with
CA certificate. Once this is completed, the negotiation goes to next step.
Some implementations of certificate authentication have the client sign
message using its private key which should be validated by server (such as
ASA) using client's public key but this isn't the case in ASA AnyConnect
implementation.
The issue you are facing is a known problem hence they are external servers
used in authorization such as ISE to ensure that even if password or
certificate is stolen, you can still verify the connecting party.
certificate matching and pinning is something else used for auto tunnel
group selection and has nothing to do with exporting the certificate and
using it in different machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2019 09:34 PM
The private key won't be validated by ASA and that is the concept of PKI.
In certificate authentication for VPN, the certificate it used for
authentication only. Technically, this means that the certificate will be
signed by the private key of the CA. When this certificate is sent to ASA
during key authentication phase, ASA will verify the signature of the
certificate by the CA using the CA Public key that is imported in ASA with
CA certificate. Once this is completed, the negotiation goes to next step.
Some implementations of certificate authentication have the client sign
message using its private key which should be validated by server (such as
ASA) using client's public key but this isn't the case in ASA AnyConnect
implementation.
The issue you are facing is a known problem hence they are external servers
used in authorization such as ISE to ensure that even if password or
certificate is stolen, you can still verify the connecting party.
certificate matching and pinning is something else used for auto tunnel
group selection and has nothing to do with exporting the certificate and
using it in different machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2020 05:50 AM
Hi,
I think you were hitting bug CSCvg40155.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvg40155
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180418-asa1
If certificate authentication is used for VPN, the user needs to hold the private key, no excuses.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide