- Cisco Community
- Technology and Support
- Security
- VPN
- Hi Philip, I did as you
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2016 07:33 PM
I have a Cisco 1921 VPN router. I have successfully created VPN Site-to-Site tunnel with AWS VPN Tunnel 1. AWS offers 2 tunnels, so I have created another Crypto Map and attached it to the existing Policy. But the 2nd tunnel will not come up. I am not sure what I am missing... is there a special configuration that needs to be done to allow multiple vpn IPsec tunnels over the same physical interface? I have attached a picture and included my router configuration if it helps.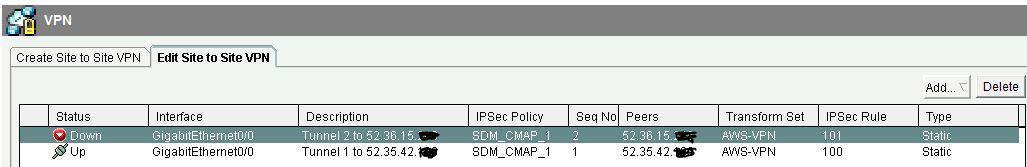
C1921#sh run
Building configuration...
Current configuration : 2720 bytes
!
! Last configuration change at 02:12:54 UTC Fri May 6 2016 by admin
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname C1921
!
boot-start-marker
boot-end-marker
!
!
logging buffered 52000
enable secret 5 $1$jc6L$uHH55qNhplouO/N5793oW.
!
no aaa new-model
ethernet lmi ce
!
!
!
!
!
!
!
!
!
!
!
!
ip domain lookup source-interface GigabitEthernet0/1
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
license udi pid CISCO1921/K9 sn FTX1845F03F
!
!
username admin privilege 15 password 7 121A0C041104
username paul privilege 0 password 7 14141B180F0B
!
redundancy
!
!
!
!
!
!
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
lifetime 28800
crypto isakmp key secret1 address 52.35.42.787
crypto isakmp key secret2 address 52.36.15.787
!
!
crypto ipsec transform-set AWS-VPN esp-aes esp-sha-hmac
mode tunnel
!
!
!
crypto map SDM_CMAP_1 1 ipsec-isakmp
description Tunnel 1 to 52.35.42.787
set peer 52.35.42.787
set transform-set AWS-VPN
set pfs group2
match address 100
crypto map SDM_CMAP_1 2 ipsec-isakmp
description Tunnel 2 to 52.36.15.787
set peer 52.36.15.787
set transform-set AWS-VPN
set pfs group2
match address 100
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description Connection to WAN$ETH-WAN$
ip address 192.168.1.252 255.255.255.0
duplex auto
speed auto
crypto map SDM_CMAP_1
!
interface GigabitEthernet0/1
description Connection to LAN
ip address 192.168.0.252 255.255.255.0
duplex auto
speed auto
!
ip forward-protocol nd
!
ip http server
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
ip route 0.0.0.0 0.0.0.0 192.168.1.254 permanent
!
logging trap debugging
logging host 192.168.0.3
logging host 192.168.0.47
!
!
access-list 100 remark Permit to AWS Tunnel 1
access-list 100 remark CCP_ACL Category=20
access-list 100 permit ip 192.168.0.0 0.0.0.255 any log
access-list 101 remark Permit to AWS Tunnel 2
access-list 101 remark CCP_ACL Category=4
access-list 101 permit ip 192.168.0.0 0.0.0.255 any logexit
!
control-plane
!
!
alias exec con conf t
alias exec sib show ip int brief
alias exec srb show run | b
alias exec sri show run int
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
privilege level 15
login local
transport input all
transport output all
!
scheduler allocate 20000 1000
!
end
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2016 10:39 PM
There should be no second tunnel.
I uses either one peer or the other, but not both at the same time.
To bring both up at the same time you need to use the Tunnel interfaces. Amazon would have emailed you pretty much the exact commands to copy and paste in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2016 08:10 PM
That is not really a configuration that Amazon AWS recommends.
When you create the VPN in Amazon they email you a suggested configuration for your device. In your case, it would use Tunnel interfaces. You really should use what they recommend.
I don't think you'll be able to configure this in the GUI.
And in short you can not use two crypto maps with the exact same encryption domains to two different destinations.
What you could do is specify the second VPN peer as a backup. Something like:
no crypto map SDM_CMAP_1 2 ipsec-isakmp
crypto map SDM_CMAP_1 1 ipsec-isakmp
description Tunnel 1 to 52.35.42.787
set peer 52.35.42.787
set peer 52.36.15.787
set transform-set AWS-VPN
set pfs group2
match address 100
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2016 08:59 PM
Hi Philip, I did as you recommended and added my second peer as a backup... but it will still not bring up my second tunnel on Amazon up simultaneously, I guess this is only possible with virtual Tunnel interfaces correct? if yes, would you have a quick instructions how I can set this up, I have not configured IPsec over virtual tunnels before.
Thanks and appreciate your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2016 10:39 PM
There should be no second tunnel.
I uses either one peer or the other, but not both at the same time.
To bring both up at the same time you need to use the Tunnel interfaces. Amazon would have emailed you pretty much the exact commands to copy and paste in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2016 10:37 PM
Hi Philip, I want to take you very much for pointing me to the right direction about the Amazon Tunnel interfaces. I have downloaded the VPN configuration for Cisco ISR routers, spent only 1 day messing with it, but finally got everything working as expected. I have my 2 tunnels up, all thanks to you and this great Cisco forum... I have included my configuration for anyone who might be setting this up in the future. Thanks again for your help, really appreciate that.
Current configuration : 4028 bytes
!
! Last configuration change at 05:25:59 UTC Sun May 8 2016 by admin
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname C1921
!
boot-start-marker
boot-end-marker
!
!
logging buffered 52000
enable secret 5 $1$jc6L$uHH55qNhplouO/N5793oW.
!
no aaa new-model
ethernet lmi ce
!
!
!
!
!
!
!
!
!
!
!
!
ip domain lookup source-interface GigabitEthernet0/1
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
license udi pid CISCO1921/K9 sn FTX184580WF
!
!
username admin privilege 15 password 7 121A0C041104
username paul privilege 0 password 7 14141B180F0B
!
redundancy
!
track 100 ip sla 100 reachability
!
track 200 ip sla 200 reachability
!
!
crypto keyring keyring-vpn-02cbd510-1
local-address GigabitEthernet0/0
pre-shared-key address 52.36.11.246 key youramazonsecretkey
crypto keyring keyring-vpn-02cbd510-0
local-address GigabitEthernet0/0
pre-shared-key address 52.55.42.169 key youramazonsecretkey
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
lifetime 28800
!
crypto isakmp policy 20
encr aes
authentication pre-share
group 2
lifetime 28800
crypto isakmp keepalive 10 10
crypto isakmp profile isakmp-vpn-02cbd510-0
keyring keyring-vpn-02cbd510-0
match identity address 52.55.42.169 255.255.255.255
local-address GigabitEthernet0/0
crypto isakmp profile isakmp-vpn-02cbd510-1
keyring keyring-vpn-02cbd510-1
match identity address 52.36.11.246 255.255.255.255
local-address GigabitEthernet0/0
!
crypto ipsec security-association replay window-size 128
!
crypto ipsec transform-set ipsec-prop-vpn-02cbd510-0 esp-aes esp-sha-hmac
mode tunnel
crypto ipsec transform-set ipsec-prop-vpn-02cbd510-1 esp-aes esp-sha-hmac
mode tunnel
crypto ipsec df-bit clear
!
!
crypto ipsec profile ipsec-vpn-02cbd510-0
set transform-set ipsec-prop-vpn-02cbd510-0
set pfs group2
!
crypto ipsec profile ipsec-vpn-02cbd510-1
set transform-set ipsec-prop-vpn-02cbd510-1
set pfs group2
interface Tunnel1
ip address 169.254.12.162 255.255.255.252
ip virtual-reassembly in
ip tcp adjust-mss 1387
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel destination 52.55.42.169
tunnel protection ipsec profile ipsec-vpn-02cbd510-0
!
interface Tunnel2
ip address 169.254.12.222 255.255.255.252
ip virtual-reassembly in
ip tcp adjust-mss 1387
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel destination 52.36.11.246
tunnel protection ipsec profile ipsec-vpn-02cbd510-1
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
description Connection to WAN$ETH-WAN$
ip address 192.168.1.252 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
description Connection to LAN
ip address 192.168.0.252 255.255.255.0
duplex auto
speed auto
!
ip forward-protocol nd
!
ip http server
ip http authentication local
no ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
!
ip route 172.31.0.0 255.255.0.0 Tunnel1 track 100
ip route 172.31.0.0 255.255.0.0 Tunnel2 track 200
ip route 0.0.0.0 0.0.0.0 192.168.1.254
ip route 192.168.0.0 255.255.255.0 GigabitEthernet0/1
ip sla 100
icmp-echo 169.254.12.161 source-interface Tunnel1
frequency 5
ip sla schedule 100 life forever start-time now
ip sla 200
icmp-echo 169.254.12.221 source-interface Tunnel2
frequency 5
ip sla schedule 200 life forever start-time now
logging trap debugging
logging host 192.168.0.47
!
!
!
control-plane
!
!
alias exec con conf t
alias exec sib show ip int brief
alias exec srb show run | b
alias exec sri show run int
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport output pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
privilege level 15
login local
transport input all
transport output all
!
scheduler allocate 20000 1000
!
end
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide