- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco 4331 easy vpn configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 4331 easy vpn configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2019 01:01 PM
Hi, I need help. I have cisco 4331 with 3 interfaces.
GigabitEthernet0/0/0 goes to Internet via Dialer1.
GigabitEthernet0/0/1 goes to MPLS L3VPN.It is connected to CE router.
GigabitEthernet0/0/2 goes to LAN.
It works perfectly. Hosts have access to VPN and Internet from lan.
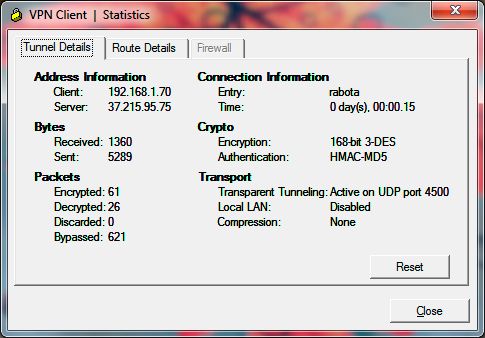
Now I need to connect several remote clients and give them access to lan and vpn 10.177.X.X.
I tried to configure easy vpn. A client connects to the easy vpn server successfully, but it can only ping hosts from lan. Cisco webui or ssh doesn't work. 10.177.x.x net is also unreachable for the remote client.
What I see myself is that I have a conflict in my access lists. They both point to the same subnet. Is there any way to wtite to the easyvpn's access list only ip 192.168.1.70-192.168.1.85? The second issue is "ip nat outside" on Dialer1 inerface. I don't know is it right for easy vpn.
!
! Last configuration change at 23:47:04 GMT Sat Mar 2 2019
!
version 16.6
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
!
hostname puhsbyt
!
boot-start-marker
boot system flash bootflash:isr4300-universalk9.16.06.05.SPA.bin
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
logging console emergencies
enable secret 5
!
!
transport-map type persistent ssh sshhandler
time-out 30
rsa keypair-name sshkeys
transport interface GigabitEthernet0
connection wait allow interruptible
!
transport-map type persistent telnet telnethandler
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication login USER-AUTH local
aaa authorization exec default local
aaa authorization network GROUP-AUTH local
!
!
!
!
!
!
aaa session-id common
no process cpu autoprofile hog
clock timezone GMT 3 0
!
!
!
!
!
!
ip nbar http-services
!
!
!
ip domain name test.com
!
ip dhcp pool Sbyt
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 194.158.196.137 194.158.196.141
!
!
!
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
ipv6 unicast-routing
!
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-1843133077
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1843133077
revocation-check none
rsakeypair TP-self-signed-1843133077
!
!
crypto pki certificate chain TP-self-signed-1843133077
certificate self-signed 01
quit
!
!
!
!
!
!
!
!
!
ivr prompt buffers 2
license udi pid ISR4331/K9 sn
license accept end user agreement
license boot level appxk9
license boot level uck9
license boot level securityk9
diagnostic bootup level minimal
spanning-tree extend system-id
!
!
!
username dima privilege 15
username admin privilege 15
username rud1 password 7
!
redundancy
mode none
!
!
!
!
!
vlan internal allocation policy ascending
!
no cdp run
!
!
!
!
!
!
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
group 2
!
crypto isakmp client configuration group RUD-GROUP
key RUD
dns 192.168.1.1
pool EZVPN-POOL
acl 110
crypto isakmp profile VPN-CLIENT
match identity group RUD-GROUP
client authentication list USER-AUTH
isakmp authorization list GROUP-AUTH
client configuration address respond
!
!
crypto ipsec transform-set 3DES-MD5 esp-3des esp-md5-hmac
mode tunnel
!
!
!
crypto dynamic-map DYNMAP 10
set transform-set 3DES-MD5
set isakmp-profile VPN-CLIENT
reverse-route
!
!
crypto map DMAP 1 ipsec-isakmp dynamic DYNMAP
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0/0
ip address dhcp
ip mtu 1452
ip nat outside
ip nbar protocol-discovery
ip tcp adjust-mss 1412
negotiation auto
pppoe enable group global
pppoe-client dial-pool-number 1
spanning-tree portfast trunk
!
interface GigabitEthernet0/0/1
ip address dhcp
ip nat outside
negotiation auto
!
interface GigabitEthernet0/0/2
ip address 192.168.1.1 255.255.255.0
ip nat inside
negotiation auto
spanning-tree portfast disable
!
interface GigabitEthernet0/1/0
shutdown
spanning-tree portfast disable
!
interface GigabitEthernet0/1/1
shutdown
spanning-tree portfast disable
!
interface GigabitEthernet0/1/2
switchport mode access
shutdown
spanning-tree portfast trunk
!
interface GigabitEthernet0/1/3
shutdown
spanning-tree portfast disable
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
no ip address
shutdown
negotiation auto
no cdp enable
!
interface Vlan1
no ip address
shutdown
!
interface Dialer1
ip address negotiated
ip mtu 1452
ip nat outside
encapsulation ppp
ip tcp adjust-mss 1412
dialer pool 1
dialer idle-timeout 0
dialer persistent
dialer-group 1
no cdp enable
ppp mtu adaptive
ppp authentication chap pap callin
ppp chap hostname
ppp chap password
ppp pap sent-username
ppp ipcp dns request
crypto map DMAP
!
ip local pool EZVPN-POOL 192.168.1.70 192.168.1.85
ip nat inside source route-map NAT_TO_ISP interface Dialer1 overload
ip nat inside source route-map NAT_TO_VPN interface GigabitEthernet0/0/1 overload
ip forward-protocol nd
ip ftp username 1
ip ftp password 7
ip http server
ip http authentication local
ip http secure-server
ip tftp source-interface GigabitEthernet0
ip route 0.0.0.0 0.0.0.0 Dialer1
ip route 10.177.0.0 255.255.0.0 10.177.106.1
!
ip ssh version 2
!
access-list 1 permit 192.168.1.0 0.0.0.255
access-list 110 permit ip 192.168.1.0 0.0.0.255 any
dialer-list 1 protocol ip permit
!
!
route-map NAT_TO_VPN permit 20
match ip address 1
match interface GigabitEthernet0/0/1
!
route-map NAT_TO_ISP permit 10
match ip address 1
match interface Dialer1 GigabitEthernet0/0/0
!
!
!
!
!
control-plane
!
!
mgcp behavior rsip-range tgcp-only
mgcp behavior comedia-role none
mgcp behavior comedia-check-media-src disable
mgcp behavior comedia-sdp-force disable
!
mgcp profile default
!
!
!
!
!
end
- Labels:
-
Other VPN Topics
-
Remote Access
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide