- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco AnyConnect and RSA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco AnyConnect and RSA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2016 10:51 PM - edited 02-21-2020 08:37 PM
Hello everybody,
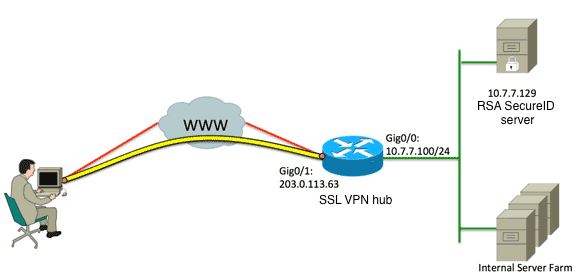
I need some advice, maybe someone will help me. I have such configuration as below,
when user works in LAN he has for example access to 2 resources: resource A and resource B.
What I want to achieve, when user connects to network through VPN I want to limit his access to one resource, ex. resource A.
In proces of authorization user is taken from LDAP (AD Windows 2012, I configured it on RSA).
I have RSA Authentication Manager 8.1 virtual appliance, Cisco ASA 5512,
Questions are, is it possible to limit this access? and if yes, where should I configure this access, on Cisco or on RSA?
best regards,
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2016 10:02 AM
Hi exsitezet1,
when I get you right, you have an ASA which is the VPN gateway for your VPN Clients (AnyConnect?).
If you want to restrict the access from the VPN clients to only special ressources in the internal network, you could do split-tunneling or permit/deny it via the normal firewall rules (when the VPN traffic is not bypassed the policy).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2016 11:43 PM
Hi kwolfgramm,
you are right, ASA is the VPN Gateway for AnyConnect clients. I'm not sure if I can restrict access in your way because user before access to the network first create VPN connection to Cisco, then is authorize in RSA with token, (on RSA user is taken from AD, it means that user is not local on RSA), when user is authorized through RSA, Cisco creates connection and user can log on to the internal network and has access to resources (A and B, first post) according to his domain permissions but I would like to restrict only to one resource, ex. resource A. Is it possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2016 09:14 AM
I can not definetely say if this is possible with this scenario (RSA/Token for VPN).
But when the traffic goes through the ASA you normally should be able to restrict it by the normal access-rules.
To test the split-tunneling you could check whether you can choose a split-tunneling list in the VPN group-policy options.
It is worth a try in my opinion (with a test user and test ruleset).
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide