- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Configure IPSEC between ASA5506 -> Branch IOS Router | Pinging issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configure IPSEC between ASA5506 -> Branch IOS Router | Pinging issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 02:51 PM - edited 02-21-2020 09:47 PM
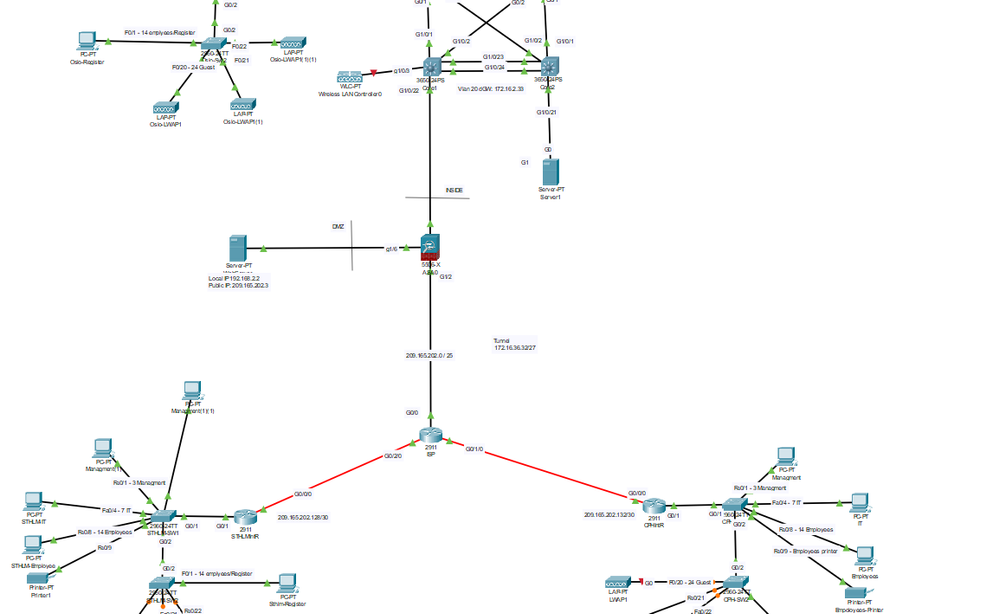
Hello, I'm trying to set up an IPsec tunnel between HQ and two branch offices. So far I've set up a connection from HQ's (ASA) to Stockholms (EdgeRouter). At least I thought that I had it going but it seems to be failing, I tried to ping from HQ Management to Sthlm MG(1)(1)
I'm using packet tracer; a requirement for the course I'm taking so ASDM is no available.
The idea is that Sthlm and Cph should be able to enter the inside as well as the DMZ.
!HQ ASA Version 9.6(1) ! hostname Firewall names ! interface GigabitEthernet1/1 nameif inside security-level 100 ip address 172.16.2.206 255.255.255.252 ! interface GigabitEthernet1/2 nameif outside security-level 0 ip address 209.165.202.1 255.255.255.128 ! interface GigabitEthernet1/6 nameif DMZWeb security-level 50 ip address 192.168.2.1 255.255.255.0 ! object network Inside-Subnet subnet 172.16.0.0 255.255.252.0 description OsloSubnet object network NET_LOCAL subnet 172.16.0.0 255.255.252.0 object network NET_STHLM subnet 172.16.8.0 255.255.252.0 object network Webserver-Outside host 192.168.2.2 description Webserver Real IP object network Webserver-Public host 209.165.202.3 description Webserver Mapped IP object network dmz_host host 192.168.2.2 ! route outside 0.0.0.0 0.0.0.0 209.165.202.2 1 route inside 172.16.0.0 255.255.252.0 172.16.2.205 1 route inside 172.16.4.0 255.255.252.0 172.16.2.205 1 route DMZWeb 192.168.2.0 255.255.255.0 192.168.2.2 1 route outside 209.165.202.0 255.255.255.128 192.168.2.2 1 ! access-list OUTSIDE-DMZ extended permit icmp any host 192.168.2.2 access-list OUTSIDE-DMZ extended permit tcp any host 192.168.2.2 eq www access-list VPN_ACL extended permit ip object NET_LOCAL object NET_STHLM ! ! access-group OUTSIDE-DMZ in interface outside object network Inside-Subnet nat (inside,outside) dynamic interface object network Webserver-Outside nat (DMZWeb,outside) static 209.165.202.3 ! ! ! ! class-map inspection_default match default-inspection-traffic ! policy-map global_policy class inspection_default inspect icmp ! service-policy global_policy global ! telnet timeout 5 ssh timeout 5 ! ! ! crypto ipsec ikev1 transform-set VPN_SET esp-3des esp-sha-hmac ! crypto map VPN_MAP 10 match address VPN_ACL crypto map VPN_MAP 10 set peer 209.165.202.129 crypto map VPN_MAP 10 set ikev1 transform-set VPN_SET crypto map VPN_MAP interface outside crypto ikev1 enable outside crypto ikev1 policy 10 encr aes authentication pre-share group 2 ! tunnel-group 209.165.202.129 type ipsec-l2l tunnel-group 209.165.202.129 ipsec-attributes ikev1 pre-shared-key cisco !
!STHLMRouter ! version 15.1 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname STHLMIntR ! enable secret 5 $1$mERr$hx5rVt7rPNoS4wqbXKX7m0 ! ! ip dhcp excluded-address 172.16.8.1 172.16.8.10 ip dhcp excluded-address 172.16.10.1 172.16.10.3 ip dhcp excluded-address 172.16.10.65 172.16.10.67 ip dhcp excluded-address 172.16.10.33 172.16.10.35 ! ip dhcp pool DHCP-POOL-STHLM network 172.16.8.0 255.255.252.0 default-router 172.168.8.1 domain-name IMT2007 ! ip cef no ipv6 cef ! license udi pid CISCO2911/K9 sn FTX1524314Q- license boot module c2900 technology-package securityk9 ! lldp run ! crypto isakmp policy 10 encr aes authentication pre-share group 2 ! crypto isakmp key cisco address 209.165.202.1 ! crypto ipsec transform-set VPN_OSLO_STHLM esp-3des esp-sha-hmac ! crypto map VPN_MAP 10 ipsec-isakmp set peer 209.165.202.1 set transform-set VPN_OSLO_STHLM match address VPN_ACL ! spanning-tree mode pvst ! interface GigabitEthernet0/1 no ip address duplex auto speed auto ! interface GigabitEthernet0/1.10 description Managment interface encapsulation dot1Q 10 ip address 172.16.10.1 255.255.255.224 ip nat inside ! interface GigabitEthernet0/1.20 description IT Interface encapsulation dot1Q 20 ip address 172.16.10.33 255.255.255.224 ip nat inside ! interface GigabitEthernet0/1.30 description Employee interface encapsulation dot1Q 30 ip address 172.16.10.65 255.255.255.224 ip nat inside ! interface GigabitEthernet0/1.40 description Guest interface encapsulation dot1Q 40 ip address 172.16.8.1 255.255.254.0 ip nat inside ! interface GigabitEthernet0/0/0 ip address 209.165.202.129 255.255.255.252 ip nat outside crypto map VPN_MAP ! interface Vlan1 no ip address shutdown ! router eigrp 10 network 172.16.8.0 0.0.3.255 ! ip nat pool NAT-POOL-STOCKHOLM 209.165.202.202 209.165.202.254 netmask 255.255.255.192 ip nat inside source list 1 pool NAT-POOL-STOCKHOLM overload ip classless ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0/0 ! ip flow-export version 9 ! ! access-list 1 permit 172.16.8.0 0.0.3.255 ip access-list extended VPN_ACL permit ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255 !
I have included the PT file: password for the equipment is 'cisco' (ASA is just entering still default)
- Labels:
-
IPSEC
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 03:01 PM
I don't have packet tracer to test, but I imagine the traffic is being natted on both sides.
Define a NAT exemption rule on the ASA, e.g - "nat (inside,outside) source static NET_LOCAL NET_LOCAL destination static NET_STHLM NET_STHLM"
On the router, modify ACL 1 to deny traffic from the local branch network to the HQ network, place that before your existing permit rule.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 06:44 PM
From CLI
network-object mode commands/options:
A.B.C.D Mapped IP address
Firewall(config-network-object)#nat (inside,outside) static
If i add a ip
<cr>
Firewall(config-network-object)#nat (inside,outside) static 172.16.0.0 !
Firewall#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 02:01 PM - edited 11-07-2019 02:05 PM
The NAT statement that RJI suggested for your ASA is called an Identity NAT, if I'm not mistaken, and needs to be configured in the global configuration, not as part of your network object.
Take a look at this document for further details on ASA NAT types.
Cheers!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: