- Cisco Community
- Technology and Support
- Security
- VPN
- Configure OKTA MFA for Cisco Anyconnect VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Configure OKTA MFA for Cisco Anyconnect VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2019 02:36 PM
Hi, we want to use OKTA as MFA authentication and I below what I did:
- Create an Authentication, Authorization, and Accounting (AAA) Server Group on the Cisco ASA using the ADSM management software.
- Create one AAA Server Profiles within the AAA group.
- Configure the Cisco ASA to use the AAA group for VPN access.
I'm putting my username and password and prompt showing up to put the authentication cod received the it show me login filed.
The error is (authentication challenged no error)
Please advice if you configured OKTA to authenticate with Anyconnect or if you know the solution.
aaa-server OktaRadiusGroup protocol radius
max-failed-attempts 5
aaa-server OktaRadiusGroup (inside) host 10.x.x.x
timeout 20
key *****
authentication-port 1812
no mschapv2-capable
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 06:16 AM
Are you following this guide?
https://help.okta.com/en/prod/Content/Topics/integrations/cisco-radius-intg.htm
You might want to run "debug radius all" on the ASA when you test so that you can see what is happening. Also, run a packet capture on the ASA as below:
capture capi interface <lan-interface-name> match ip host <asa-lan-interface-ip> host <okta-server>
then "show capture capi" after the test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 08:44 AM
Yes, I followed the same guide.
When I try to test the server from ASDM getting below error:
Authentication Challenged: No error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 09:02 AM
Below is the packet capture when I try to connect from AnyConnect:
6 packets captured
1: 08:49:04.249498 asa-lan-interface.51617 > okta-server.1812: udp 657
2: 08:49:05.584228 okta-server.1812 > asa-lan-interface.51617: udp 220
3: 08:49:06.160056 asa-lan-interface.51617 > okta-server.1812: udp 747
4: 08:49:06.755743 okta-server.1812 > asa-lan-interface.51617: udp 172
5: 08:49:16.361751 asa-lan-interface.51617 > okta-server.1812: udp 747
6: 08:49:16.880813 okta-server.1812 > asa-lan-interface.51617: udp 39
6 packets shown
Below is the packet capture when I try to test from ASDM:
8 packets captured
1: 08:49:04.249498 asa-lan-interface.51617 > okta-server.1812: udp 657
2: 08:49:05.584228 okta-server.1812 > asa-lan-interface.51617: udp 220
3: 08:49:06.160056 asa-lan-interface.51617 > okta-server.1812: udp 747
4: 08:49:06.755743 okta-server.1812 > asa-lan-interface.51617: udp 172
5: 08:49:16.361751 asa-lan-interface.51617 > okta-server.1812: udp 747
6: 08:49:16.880813 okta-server.1812 > asa-lan-interface.51617: udp 39
7: 08:50:32.104074 asa-lan-interface.51617 > okta-server.1812: udp 87
8: 08:50:33.321470 okta-server.1812 > asa-lan-interface.51617: udp 220
8 packets shown
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2020 08:36 AM
Was anyone able to resolve this? We'd like to use SAML and not RADIUS. 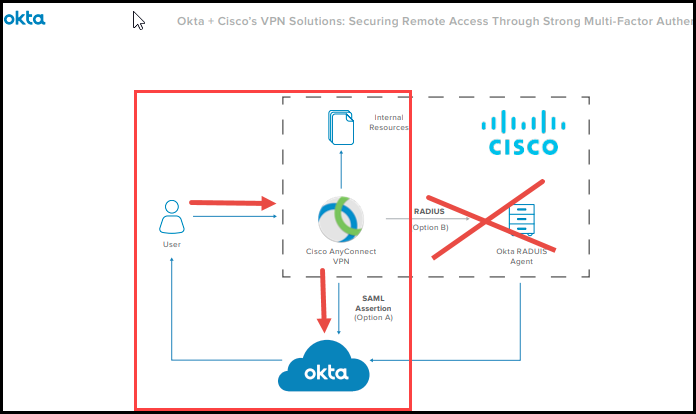
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: