- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Easy VPN Assistance
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 01:50 AM
Good Morning all.
I am trying to set up an Easy VPN connection between an 2811, and an 887 router. I am getting some errors which I cannot resolve. Your assistance in this would be greatly appreciated
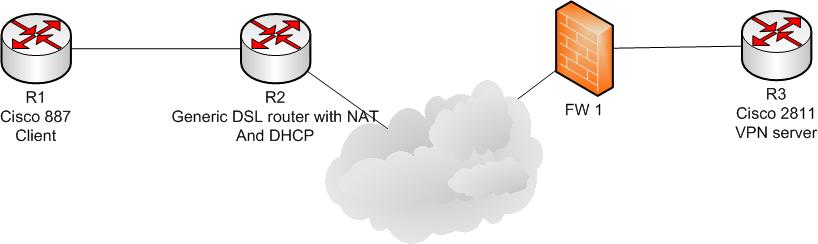
They are set up in the following manner, with the intention that the 887 can be put in a users home, and connected into their generic DSL router, and provide connectivity into the enteprise. In this set up, it is a 877, but the intention is that the config of this device should not be adjusted.
The Firewall NATs an external IP address to the 10.228.156.33 address present on R3
R1 attempts a connection to R3, but returns the error
Oct 11 08:48:42.905: %CRYPTO-4-EZVPN_FAILED_TO_CONNECT: EZVPN(Remote) Ezvpn is in state READY, previous state was CONNECT_REQUIRED and event is CONN_UP. Session is not up after 180 seconds of initiating session, resetting the connection
Oct 11 08:48:42.905: %CRYPTO-6-EZVPN_CONNECTION_DOWN: (Client) User= Group=groupname Client_public_addr=172.17.4.43 Server_public_addr=1.2.3.4
and a sh crypto isakmp sa, shows a connection to R3, however this times out after 180 seconds
R3 then shows a route to 10.153.100.0/24 via f0/1, but no SA fo R1
Usernames, passwords and keys are correct, but have been removed from the configs below
Thanks for your assistance
R1 config
hostname Router
!
boot-start-marker
boot-end-marker
!
!
enable secret xxxx
!
no aaa new-model
crypto pki token default removal timeout 0
!
!
ip source-route
ip cef
!
!
!
!
ip dhcp pool client
network 10.153.100.0 255.255.255.0
default-router 10.153.100.1
dns-server 10.203.2.10
!
!
no ipv6 cef
!
!
license udi pid C887VA-W-E-K9 sn xxxxx!
!
username xxxx privilege 15 password 0 xxxxx
!
!
!
!
controller VDSL 0
!
!
!
!
!
crypto ipsec client ezvpn Remote
connect auto
group groupname key xxxxxx
mode network-extension
peer 1.2.3.4 xauth userid mode interactive
!
!
!
!
!
interface ATM0
no ip address
shutdown
no atm ilmi-keepalive
!
interface Ethernet0
no ip address
shutdown
!
interface FastEthernet0
no ip address
!
interface FastEthernet1
switchport access vlan 2
no ip address
!
interface FastEthernet2
switchport access vlan 2
no ip address
!
interface FastEthernet3
switchport access vlan 2
no ip address
!
interface Vlan1
ip address dhcp
crypto ipsec client ezvpn Remote
!
interface Vlan2
ip address 10.153.100.1 255.255.255.0
crypto ipsec client ezvpn Remote inside
!
ip forward-protocol nd
ip http server
no ip http secure-server
!
ip pim bidir-enable
ip route xxxxx 255.255.255.255 Vlan1
!
no cdp run
!
!
!
!
!
line con 0
exec-timeout 0 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport input all
stopbits 1
line vty 0 4
login
transport input all
!
scheduler allocate 20000 1000
end
R3#
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
enable secret xxxxx
!
aaa new-model
!
!
aaa authentication login VPN_xauth local
aaa authorization network VPN_group local
!
aaa session-id common
!
!
ip cef
!
!
voice-card 0
no dspfarm
!
username xxxx privilege 15 password xxxx
archive
log config
hidekeys
!
!
!
!
crypto isakmp policy 1
encr aes 256
authentication pre-share
!
crypto isakmp policy 3
encr 3des
authentication pre-share
group 2
!
crypto isakmp client configuration group groupname
key xxxxx
!
!
crypto ipsec transform-set myset esp-3des esp-sha-hmac
!
crypto ipsec profile remote-access
!
!
crypto dynamic-map dynmap 10
set transform-set myset
!
!
crypto map clientmap client authentication list VPN_xauth
crypto map clientmap isakmp authorization list VPN_group
crypto map clientmap 10 ipsec-isakmp dynamic dynmap
!
!
!
!
interface FastEthernet0/0
ip address 10.203.4.33 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 10.228.156.33 255.255.255.0
duplex full
speed 100
crypto map clientmap
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 10.228.156.254
ip route 10.0.0.0 255.0.0.0 10.203.4.254
!
!
ip http server
no ip http secure-server
!
!
line con 0
line aux 0
line vty 0 4
exec-timeout 360 0
password xxxx
!
scheduler allocate 20000 1000
!
end
Solved! Go to Solution.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 06:58 AM
Hello Geoff,
I hope the routing has been taken care since the R2 is no more in the picture ?..just a stupid question .. are we able ping Server from the Client ?
regards
Harish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 07:02 AM
Routing is working correctly, with only a single default route on R1. R1 can contact R3 with no issues
The firewall is blocking ping, but all routing is correct.
Thank you for all your help
Geoff
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 07:05 AM
Hello geoff,
Found something..
on R1, the peer is configured as 193.128.190.33 but that IP is not configured in R3 is it natted on firewall ? if yes, did we allow udp port 4500 towards that ip ?
regards
Harish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 07:12 AM
The firewall is carrying out nat between 193.128.190.33 and 10.228.156.33
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 07:32 AM
UDP 4500 was not allowed, but now it is.
This then gave an error on R1 that save password was required, but not allowed.
I re-added the config save-password and 'crypto map clientmap client configuration address respond' which removed this error and now I am seeing the SA active on both ends.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 01:49 PM
Hello Geoff
Did that solve your issue?
Harish.
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 01:33 AM
Although the VPN is now up, there is currently no traffic being encrypted or decrypted.
r1#ping 10.203.4.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.203.4.1, timeout is 2 seconds:
..
Success rate is 0 percent (0/2)
r1#sh crypto ipsec sa
interface: Vlan1
Crypto map tag: Vlan1-head-0, local addr 172.17.4.43
protected vrf: (none)
local ident (addr/mask/prot/port): (10.153.100.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 193.128.190.33 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
Geoff
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 01:51 AM
Hello Geoff,
try to orginate the traffic from the inside interface
ping 10.203.4.1 source vlan2
and see the show crypto ipsec sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:11 AM
Would appear the traffic is correctly encrypted from R1 to R3, but the traffic is not returning from R3 to R1
r1#ping 10.203.4.33 source vl 2
#pkts encaps: 78, #pkts encrypt: 78, #pkts digest: 78
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
R3#sh crypto ipsec sa
interface: FastEthernet0/1
Crypto map tag: clientmap, local addr 10.228.156.33
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (10.153.100.0/255.255.255.0/0/0)
current_peer 86.129.102.235 port 4500
PERMIT, flags={}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 83, #pkts decrypt: 83, #pkts verify: 83
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:28 AM
Hello Geoff,
That looks to be arouting issue for me..
can you add a host route on R3 back to R1
ip route 10.153.100.1 255.255.255.255 < gwateway> i guess the gateway would be firewall ?
Harish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:32 AM
R3 is showing the 10.228.156.0 network as directly connected via f0/1
R3# sh ip rou
Gateway of last resort is 10.228.156.254 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
S 10.0.0.0/8 [1/0] via 10.203.4.254
C 10.228.156.0/24 is directly connected, FastEthernet0/1
C 10.203.4.0/24 is directly connected, FastEthernet0/0
S* 0.0.0.0/0 [1/0] via 10.228.156.254
R3#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:38 AM
Thats fine.. but when the traffic is being generated from vlan 2 of R1, R3 should reply back to 10.153.100.1..as per the current route R3 it takes 10.203.4.254 as the gateway because of the prefix match ( 10.0.0.0/8),,so create a routes on R3 as follows
ip route 10.153.100.0 255.255.255.0 10.228.156.254
this should solve your issue
regards
Harish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:41 AM
Harish, you are a genius.
Thank you very much for all your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2012 02:44 AM
Good to hear that the issue is sorted out
Thank you for the rating
Harish.
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: