- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEv2 S2S between ISR 886VA and ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 02:46 AM - edited 03-12-2019 05:25 AM
Hello,
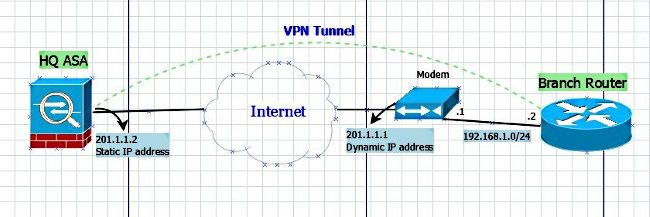
I try to configure the IKEv2 tunnel between ASA 5510 and ISR 886VA using this article, scenario one. I have configured it, but i have a few questions:
1) what is the address 10.10.10.1 ? there is no such IP address on the scheme:
2) how can i define which traffic to send through the tunnel? For example, there is a network behind the ASA 10.255.10.0/24, I would like to access it from ISR network 10.254.1.0/24, but I don't need to encrypt the traffic to network 10.255.30.0/24.
My scheme:
Thank you in advance!
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2018 07:20 AM
this article doesn't include any information about routing configuration moreover it has a wrong ACL. Here is a part my working config:
ISR 886 VA:
! crypto ikev2 proposal L2L-Prop encryption 3des integrity sha1 group 2 5 ! crypto ikev2 policy L2L-Pol proposal L2L-Prop ! crypto ikev2 keyring L2L-Keyring peer vpn address 187.XXX.XXX.XX1 pre-shared-key local ********* pre-shared-key remote ********* ! crypto ikev2 profile L2L-Prof match identity remote address 187.XXX.XXX.XX1 255.255.255.255 identity local key-id S2S-IKEv2 authentication remote pre-share authentication local pre-share keyring local L2L-Keyring ! crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac mode tunnel ! crypto map vpn 10 ipsec-isakmp set peer 187.XXX.XXX.XX1 set transform-set ESP-AES-SHA set ikev2-profile L2L-Prof match address vpn ! interface Dialer0 crypto map vpn ! ip route 10.255.10.0 255.255.255.0 187.XXX.XXX.XX1 ! ip access-list extended vpn permit ip 10.254.1.0 0.0.0.255 10.255.10.0 0.0.0.255 ! access-list 101 deny ip 10.254.1.0 0.0.0.255 10.255.10.0 0.0.0.255 access-list 101 permit ip 10.254.1.0 0.0.0.255 any
ASA 5510:
interface Ethernet0/0 duplex full nameif WAN security-level 0 ip address 187.XXX.XXX.XX1 255.255.255.248 ! interface Ethernet0/1 duplex full nameif LAN-MSP security-level 100 ip address 10.255.10.99 255.255.255.0 ! object network LAN-MSP subnet 10.255.10.0 255.255.255.0 object network OFFICE subnet 10.254.1.0 255.255.255.0 access-list vpn extended permit ip 10.255.10.0 255.255.255.0 10.254.1.0 255.255.255.0 nat (LAN-MSP,any) source static LAN-MSP LAN-MSP destination static OFFICE OFFICE ! crypto ipsec ikev2 ipsec-proposal ESP-AES-SHA protocol esp encryption aes protocol esp integrity sha-1 crypto ipsec security-association pmtu-aging infinite crypto dynamic-map dmap 1 match address vpn crypto dynamic-map dmap 1 set ikev2 ipsec-proposal ESP-AES-SHA crypto map vpn 1 ipsec-isakmp dynamic dmap crypto map vpn interface WAN crypto ca trustpool policy crypto ikev2 policy 1 encryption 3des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 enable WAN group-policy Site-to-Site internal group-policy Site-to-Site attributes vpn-tunnel-protocol ikev2 tunnel-group S2S-IKEv2 type ipsec-l2l tunnel-group S2S-IKEv2 general-attributes default-group-policy Site-to-Site tunnel-group S2S-IKEv2 ipsec-attributes ikev2 remote-authentication pre-shared-key ******* ikev2 local-authentication pre-shared-key *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 03:00 AM
Hi, 10.10.10.1 is the local IP address of the router, it's defined in the ACL called vpn this acl is referenced in the crypto map. Any traffic matching from source 10.10.10.1 to destination 201.1.1.2 will be encrypted.
ip access-list extended vpn
permit ip host 10.10.10.1 host 201.1.1.2
crypto map vpn 10 ipsec-isakmp
match address vpn
Any traffic you want to encrypt and send over the VPN tunnel needs to be defined in an ACL and this ACL must be referenced in the crypto map.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 03:13 AM
But if 10.10.10.1 is an internal address of the router then I allow all outgoing traffic to be encrypted even Internet traffic, don't I? because every traffic comes to that address...
For me it looks like that Cisco's will encrypt the traffic based on source address:
if traffic comes from 10.10.10.1 - encrypt it! Doesn't it?
Any traffic you want to encrypt and send over the VPN tunnel needs to be defined in an ACL and this ACL must be referenced in the crypto map.
HTH
So, I have to add:
permit ip 10.255.10.0 0.0.0.255 201.1.1.2 or what?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 03:30 AM
You'd define the source IP address/subnet and destination IP address/subnet, if it does not match the ACL (which has to be an extended ACL not standard) then the traffic will not be encrypted and not sent via the tunnel.
So if you don't define the destination as 0.0.0.0, then no the internet traffic will not be routed through the VPN tunnel.
Your example will encrypt and send all traffic from 10.255.10.0/24 to 201.1.1.2 via the VPN tunnel. All other traffic would not match the ACL and be routed via the default gateway.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 03:44 AM
Your example will encrypt and send all traffic from 10.255.10.0/24 to 201.1.1.2 via the VPN tunnel. All other traffic would not match the ACL and be routed via the default gateway.
HTH
but i don't send anything to 201.1.1.2, i (as a client of 10.254.1.0/24 network) send to 10.255.10.0/24
So, i have to add on the router:
IP ROUTE 10.254.10.0 255.255.255.0 201.1.1.2
Without that route any traffic to 10.254.10.0/24 will go through the default gateway. Right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 04:04 AM
201.1.1.2 was from the example, in your scenario the router cfg would be:-
ip access-list extended vpn
permit ip 10.255.10.0 0.0.0.255 10.254.10.0 0.0.0.255
permit ip 10.255.30.0 0.0.0.255 10.254.10.0 0.0.0.255
crypto map vpn 10 ipsec-isakmp
match address vpn
interface gig 0/1
desc YOUR EXTERNAL INTERFACE
crypto map vpn
You do not need to create a static route when using a crypto map, traffic will be routed to the external interface and if the crypto map is referenced it will lookup the ACL and match traffic and send over the tunnel accordingly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 06:42 AM
my config on the router:
! crypto ikev2 proposal L2L-Prop encryption 3des integrity sha1 group 2 5 ! crypto ikev2 policy L2L-Pol proposal L2L-Prop ! crypto ikev2 keyring L2L-Keyring peer vpn address XXX.XXX.XXX.XXX pre-shared-key local cisco321 pre-shared-key remote cisco123 ! ! ! crypto ikev2 profile L2L-Prof match identity remote address XXX.XXX.XXX.XXX 255.255.255.255 identity local key-id S2S-IKEv2 authentication remote pre-share authentication local pre-share keyring local L2L-Keyring ! controller VDSL 0 ! crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac mode tunnel ! crypto map vpn 10 ipsec-isakmp set peer XXX.XXX.XXX.XXX set transform-set ESP-AES-SHA set ikev2-profile L2L-Prof match address vpn ! interface ATM0 no ip address shutdown no atm ilmi-keepalive ! interface Ethernet0 description WAN no ip address ip nbar protocol-discovery ipv4 service-policy input Hosts ! interface Ethernet0.7 description VDSL VLAN 7 tagged encapsulation dot1Q 7 pppoe enable group global pppoe-client dial-pool-number 1 ! interface FastEthernet0 description Trunk switchport mode trunk no ip address ! interface FastEthernet1 no ip address ! interface FastEthernet2 description DMZ switchport access vlan 3 no ip address ! interface FastEthernet3 description LAN no ip address duplex full ! interface Vlan1 description LAN ip address 10.254.1.1 255.255.255.0 ip nbar protocol-discovery ipv4 ip flow ingress ip nat inside ip virtual-reassembly in ! ! interface Dialer0 description VDSL TELEKOM ip ddns update hostname XXXXXX.DOMIAN.LOCAL ip ddns update dyndns ip address negotiated no ip redirects no ip unreachables no ip proxy-arp ip mtu 1492 ip nbar protocol-discovery ipv4 ip nat outside ip virtual-reassembly in encapsulation ppp ip tcp adjust-mss 1452 load-interval 30 dialer pool 1 dialer-group 1 no keepalive ppp authentication pap callin ppp pap sent-username ------------------- password 7 ------------------------ ppp ipcp dns request ppp ipcp mask request ppp ipcp route default no cdp enable crypto map vpn ! ip forward-protocol nd no ip http server no ip http secure-server ! ip flow-export source Vlan1 ip flow-export version 9 ip flow-export destination 10.254.1.7 2055 ip flow-top-talkers top 10 sort-by bytes ! ip nat inside source list 101 interface Dialer0 overload ! ip access-list extended vpn permit ip 10.255.10.0 0.0.0.255 10.254.1.0 0.0.0.255 ! logging source-interface Vlan1 logging host 10.254.1.7 !
My config on the ASA:
! interface Ethernet0/0 duplex full nameif WAN security-level 0 ip address XXX.XXX.XXX.XXX 255.255.255.248 ! interface Ethernet0/1 duplex full nameif LAN-MSP security-level 100 ip address 10.255.10.1 255.255.255.0 ! crypto ipsec ikev2 ipsec-proposal ESP-AES-SHA protocol esp encryption aes protocol esp integrity sha-1 crypto ipsec security-association pmtu-aging infinite crypto dynamic-map dmap 1 set ikev2 ipsec-proposal ESP-AES-SHA crypto map vpn 1 ipsec-isakmp dynamic dmap crypto map vpn interface WAN crypto ikev2 policy 1 encryption 3des integrity sha group 5 2 prf sha lifetime seconds 86400 crypto ikev2 enable WAN tunnel-group S2S-IKEv2 type ipsec-l2l tunnel-group S2S-IKEv2 general-attributes default-group-policy Site-to-Site tunnel-group S2S-IKEv2 ipsec-attributes ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key *****
but it doesn't go through the tunnel:
>tracert 10.255.10.160
Tracing route to 10.255.10.160 over a maximum of 30 hops
1 1 ms 1 ms 1 ms 10.254.1.1
2 19 ms 19 ms 21 ms 62.XXX.XXX.XXX
3 62.XXX.XXX.XXX reports: Destination host unreachable.
How can i check that the tunnel is established?
sorry, i'm not so experienced in Cisco...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 06:48 AM
Use the commands "show crypto ikev2 sa".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 06:53 AM
I ping from 10.254.1.133 even direct from router 10.254.1.1
"show crypto ikev2 sa" shows nothing on the router and "There are no IKEv2 SAs" on the ASA (((
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 07:27 AM
ip access-list extended vpn
permit ip 10.254.1.0 0.0.0.255 10.255.10.0 0.0.0.255
no permit ip 10.255.10.0 0.0.0.255 10.254.1.0 0.0.0.255
Run "debug crypto ikev2" on the router and try again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 07:32 AM
unfortunately nothing has been changed....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 07:39 AM
Anything in the debugs?
Can you post the latest fulls config for both devices as attachments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 08:09 AM
i'll send it a bit later. maybe tomorrow.
Thank you very much for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 12:38 AM
@Rob Ingram wrote:
I have gotten this configuration working in my lab, so it works.
Anything in the debugs?
Can you post the latest fulls config for both devices as attachments.
Here you are.
I think I know why it doesn't work.
Meanwhile the ISR router makes portforwarding of ports for L2TP VPN to a Windows Server: 1701, 4500, 500. But IKEv2 uses 4500 and 500 too. I could try to disable this portforwarding for a while and test it again. Actually, if I have a success then I don't need this portforwarding any more.
Also, the ASA makes the SSL VPN, but we don't use it now. I hope it doesn't affect to IKEv2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2018 01:12 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide