- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Internet stopped working when connected to Cisco VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 08:48 AM
Hi,
I have configured IPSec (Ikev1) Remote access VPN in ASA 5520, VPN is connecting properly and i am able to access all internal resources but Internet is not working when connected to VPN. I have investigated on this and found problem with the default gateway, i am getting ddefault gateway duringVPN connection. I am surprised in ASA there is no default gateway configured for remote VPN IP pool then how remote clients can get default gateway.
I am describing my problem in below given image Please help me to shootout it.
Thanks in advanve.
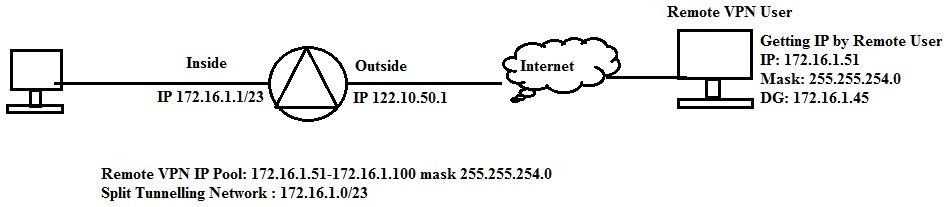
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 08:14 PM
Hi Mukesh ,
Until you specify below command under your group policy , you will get default gateway assigned by ASA to your vpn user . Please update your tunnel config & group policy
group-policy XYZ attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-tunnel
access-list split-tunnel standard permit 172.16.1.0 255.255.255.0
For anyconnect with split tunnel use below URL for help
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080975e83.shtml
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080702999.shtml
HTH
Regards
Santhosh Saravanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 01:26 AM
hi,
thats right. you must use the split tunneling. By default the ASA gets the vpn client a default route 0.0.0.0/0, that mean that all traffic will be forwarded through the vpn tunnel. you must configure it in the groupe policy via consol or ASDM.
Via asdm:



Regards
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 08:55 AM
Hi,
First of all I would suggest that you change the VPN Pool to something else than your internal network. They arent part of the same network anyway.
This might also be related to your problem.
In a normal Split Tunnel VPN setup you should be able to connect to the Internet just fine "past" the actual VPN connection.
So as I said, please first change the VPN Pool to something else than a network that is overlapping with the LAN network and configure NAT0 configurations for this new VPN Pool and then try again.
Have you set a DNS server into your VPN CLient configurations?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 01:33 PM
Thanks a lot for your reply.
As per your suggestion i have changed the remote VPN ip pool, previously it was 172.16.1.51 to 172.16.1.100 and now it is 172.16.10.1 to 172.16.1.254 mask 255.255.255.0 but the problem is still continuing. Remote vpn user is getting 172.16.10.1 and default gateway 172.16.10.2 and in this condition Internet is not working.
I have added 172.16.10.0/24 in nat0 before putting in Remote VPN IP Pool.
Yes DNS servers are set for VPN client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 07:46 PM
Hi Mukesh,
Please check the if the split tunnel is getting pushed correctly to the client. To check that you need to right on the yellow lock icon and click on statistic. In the statistic window check the route detail tab and make sure you see 172.16.1.0/24 there. if possible send me the following output:
show vpn-sessiondb remote
show run tunnel-group xyz (xyz should be replace with name of the tunnel-group)
sh run group-policy xyz (xyz should be replace with name of the group-policy)
If you have correct split tunneling access-list and you have the correct split tunnel pushed to the client then there is no reason that you will not be able to connect to the internet.
Thanks
Jeet Kumar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 08:14 PM
Hi Mukesh ,
Until you specify below command under your group policy , you will get default gateway assigned by ASA to your vpn user . Please update your tunnel config & group policy
group-policy XYZ attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-tunnel
access-list split-tunnel standard permit 172.16.1.0 255.255.255.0
For anyconnect with split tunnel use below URL for help
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080975e83.shtml
ASA/PIX: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080702999.shtml
HTH
Regards
Santhosh Saravanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 01:39 AM
Thanks a lot Jeet and Santhosh your replies helped me. Thanks to all repliers.
This is the previous group policy: with this configuration remote users were getting default gateway
ASA-VTV# sh run group-policy VTVREMOTEVPN
group-policy VTVREMOTEVPN internal
group-policy VTVREMOTEVPN attributes
dns-server value 172.16.1.10 172.16.1.11
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelall
split-tunnel-network-list value VTVREMOTEVPN_splitTunnelAcl
default-domain none
ASA-VTV#
This is modified group policy: with this configuration remote users are not getting default gateway
ASA-VTV# sh run group-policy VTVREMOTEVPN
group-policy VTVREMOTEVPN internal
group-policy VTVREMOTEVPN attributes
dns-server value 172.16.1.10 172.16.1.11
vpn-filter value VTVREMOTEVPN_splitTunnelAcl
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VTVREMOTEVPN_splitTunnelAcl
default-domain value abcl.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 01:56 AM
Hi,
The top configurations is specified to Tunnel All traffic as you can see from the "split-tunnel-policy tunneall". In this case the Split Tunnel ACL is ignored to my understanding.
The bottom configuration is specified to use Split Tunnel but I cant see the ACL specified there.
To my understanding you should be seeing routes on your actual computers routing table for the networks that are reached through the VPN.
On a Windows machine you can open the command prompt and issue the command "route print" to view the routes
Here is an example when I am connected to one Split Tunnel VPN (click to enlarge)


To my understanding there is no default gateway in the virtual VPN interface configurations as the host forward all the traffic that needs to be tunneled to the actual virtual interface and from there on in it heads through the VPN Connection.
Here is an example what the VPN Client Statistics/Route Details tells me

Both Internet and the remote network/host behind the VPN connection can be reached.
What does the above window show for you in your VPN Client when active?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 01:26 AM
hi,
thats right. you must use the split tunneling. By default the ASA gets the vpn client a default route 0.0.0.0/0, that mean that all traffic will be forwarded through the vpn tunnel. you must configure it in the groupe policy via consol or ASDM.
Via asdm:



Regards
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2018 11:04 PM
if you have full tunnel VPN, you need to add the virtual-template 1 interface as a ip nat inside, so that it provides internet to the device connected to it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 06:41 AM - edited 09-22-2020 06:42 AM
Reinstalling Cisco Anyconnect Client solved my issue
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




