- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IPSEC Site-To-Site Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSEC Site-To-Site Tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 08:37 AM - edited 03-12-2019 05:25 AM
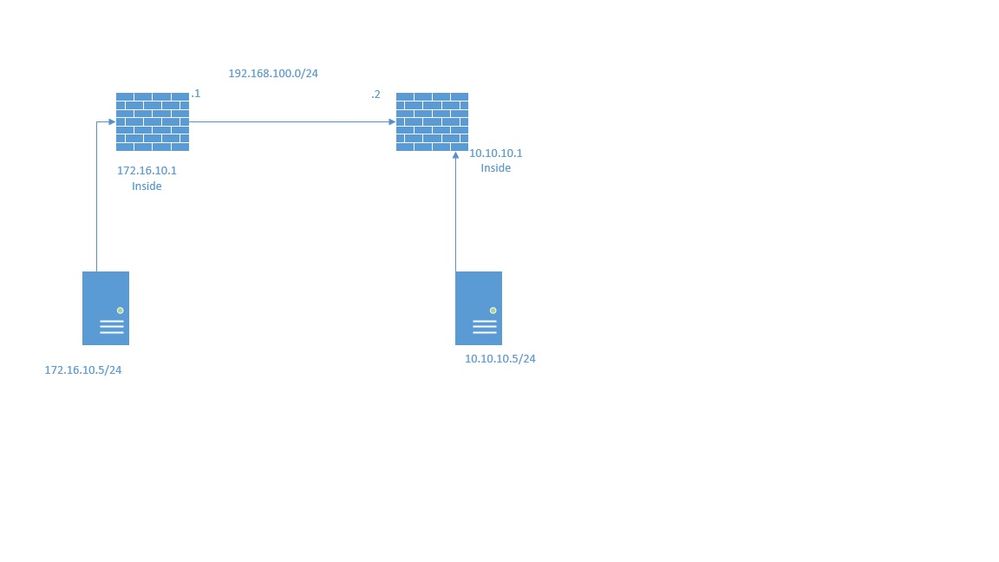
I have a site-to-site VPN using 2 Cisco ASAv. It looks like the IPSec tunnel is up but I can not reach the other side of the tunnel. It looks like my crypto map is correct but I cannot ping or telnet. Below is a basic topology and I attached some config files. Looking for some help with something I may have missed. Thanks for any help!
Will rate response posts!
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 09:20 AM
Hi,
Do you have any NAT defined anywhere?If yes, then you will need to define a no-nat rule between the lan subnets for both vpn peers.
Can you provide the full configuration of both ASA?
Have you run packet-tracer? Could you provide the output here please?
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 10:51 AM - edited 06-28-2018 10:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 10:56 AM
Perform filtering of traffic over the tunnel using vpn-filter.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 07:11 AM
Thanks for the response. I did create an new crypto map on both ASA and I was able to ping and telnet. The only way I am able to do that is by setting ip any any. If I set a source and destination IP it does not work. I did a packet capture and see the source host go out but never establishes a connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 07:30 AM
access-list outside_cryptomap extended permit ip object NETWORK_OBJ_172.16.10.0_24 object VPN-Remote-10.10.10.0_24
This will allow you to establish a VPN and then from there use the vpn filter to lock down the permitted traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 01:09 PM
Thanks for the response RJI.
Does the crypto map have to have permit ip? This will allow all types of service traffic correct? So if I wanted the tunnel to be limited just to telnet traffic, would I create another entry in the crypto map or create something new? Could you provide an example with the filtering?
Thanks for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 01:41 PM
No you don't need to have a permit ip, but you may struggle in establishing a VPN in the first instance and in the future if you need to permit further protocols/services, you'll need to amend the crypto map acl which would require resetting the tunnel to renegotiate. If there is an issue with that, that will require a lot of troubleshooting.
As explained previously, establish the tunnel by permit ip source subnet dest subnet, then lock down the allowed traffic over the VPN using VPN Filter feature. Any amendments in the future will not impact the VPN connectivity.
Example 2 here covers what you want to be doing. More examples here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 07:35 AM
I checked the config and found your crypto acl and vpn filter acl is same.
VPN filter are always work in reverse like if crypto acl is
access-list crypto_acl_1 per ip X.X.X.X24 Y.Y.Y.Y/24
THEN FILTER ACL SHOULD BE IN
access-list vpn-filter per ip Y.Y.Y.Y/24 X.X.X.X/24
VPN filters are primarily used to filter port specific traffic, so in your scenario you can remove the filter and use crypto acl only as you are using IP based ACL.
Regards,
Deepak Kumar
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide