- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Issue with Split-Tunnel and Local LAN Access via AnyConnect VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Issue with Split-Tunnel and Local LAN Access via AnyConnect VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2018 03:13 PM - edited 03-12-2019 05:32 AM
Hello All,
We are using Cisco AnyConnect, ASA5525X for VPN access. We have a Split-Tunnel setup to route 192.168.0.0/16 and 10.0.0.0/8 over the VPN tunnel.
The issue we're running into is that we still have one important file server using a 192.168.1.x address (*let's say 192.168.1.100), which is a subnet that some home Routers still use. And with Local LAN Access enabled users cannot reach this very important server. Also, some users need local LAN access enabled to access printers at home, etc... Changing the server address really isn't an option since SOO many things point to it right now.
I've tried adding routes in Windows with the route add command. For example, I enabled Local LAN Access in AnyConnect and then added a route to 192.168.1.100 and pointed it at the VPN gateway address. But, still couldn't reach the server. I'm guessing it's because the default/static routes on the PC have a Metric of 2 and when I add the route myself, the Metric is something in the 20s or 30s... I also tried this the other way, disable the "Allow Local LAN Access" in AnyConnect and added a route to a user's printer, but was unable to access the printer (*which makes sense since Local LAN Access was disabled).
Is there something I can do inside our network that would help fix this? Is there a way to create a 10.x.x.x address and have the ASA point it at 192.168.1.100..? Could this be done with NAT, and if so how would I achieve that?
Any help would be greatly appreciated!
Thanks in Advance,
Matt
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2018 03:24 PM
dont fully understand the complication, doesnt the 192.168.1.100/24 fall withing the 192.168.0.0/16 that your route ross your split tunnel (btw split tunnels are usually a bad idea from a security point of view, but anyway).
can you maybe draw a picture on where this important 192.168.1.100 in relation to the VPN user?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 09:11 AM
Basically, the 192.168.1.100 is a SMB server where everyone's different share drives live.
If a user's home network uses 192.168.1.0/24 for their local LAN, and they have "Local LAN Access" enabled, they cannot reach the server because it would look for it in the Local network at the employee's home since they are using the same subnet locally. If they were to disable Local LAN Access, then they can reach the server just fine since everything would get sent over the VPN tunnel, but they wouldn't be able to print to a printer located in their home.
So I'm wondering if there is a way on the ASA to make it so they can reach that server and still be able to use Local LAN Access? I tried adding a "permit 192.168.1.100 255.255.255.255" to the split tunnel's ACL, but that didn't seem to make a difference.
Does that make sense?
-Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 11:22 AM
If it is a common server that everyone needs access to, you can add a specific ACE just for that that server. This will install a /32 route on the client machine to send it over the tunnel. This should take precedence over the /24 subnet route that the Local LAN access feature installs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 11:29 AM
So on the Group Policy > "Employee-GP" > Split-Tunnel > Edit/Manage "Network List" > and add a Permit 192.168.1.100/32...?
If so, I believe I tried that already yesterday and it didn't seem to help. But, I can test it again to make sure. I'll post back with results.
Would that addition to the ACE need to be before the other entries?
-Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 11:43 AM
Yes, that is the correct setting. Order should not matter since the split tunnel ACL is essentially a list of networks added into the client routing table.
Collect the routing table information from the client machine after a connection and see what it looks like.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2018 12:21 PM
Ok, so I added 192.168.1.100/32 to the ACE that's assigned to the Split-Tunnel. Still couldn't ping that SMB server's address when "Allow Local LAN Access" is enabled through AnyConnect client.
Some IPs you'll see in output below:
10.40.111.18 - Client's VPN Address
192.168.1.100 - File server address inside corporate network
10.40.1.3 - Internal DNS Server
192.168.5.30 - Internal DNS Server 192.168.1.4 - Local LAN IP of Client 192.168.1.8 - Local Printer inside Client's LAN
Route From Client (*and pings):
C:\Users\Matt>route print
===========================================================================
Interface List
33...00 05 9a 3c 7a 00 ......Cisco AnyConnect Secure Mobility Client Virtual Miniport Adapter for Windows
13...1c 65 9d af 4f a0 ......Bluetooth Device (Personal Area Network)
11...58 94 6b ac e5 74 ......Intel(R) Centrino(R) Advanced-N 6200 AGN
10...5c 26 0a 33 b9 8a ......Intel(R) 82577LM Gigabit Network Connection
1...........................Software Loopback Interface 1
30...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter
15...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface
32...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #3
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.4 281
10.0.0.0 255.0.0.0 10.40.111.1 10.40.111.18 2
10.40.1.3 255.255.255.255 10.40.111.1 10.40.111.18 2
10.40.111.0 255.255.255.0 On-link 10.40.111.18 257
10.40.111.18 255.255.255.255 On-link 10.40.111.18 257
10.40.111.255 255.255.255.255 On-link 10.40.111.18 257
65.127.169.70 255.255.255.255 192.168.1.1 192.168.1.4 26
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.0.0 255.255.0.0 10.40.111.1 10.40.111.18 2
192.168.1.0 255.255.255.0 On-link 192.168.1.4 281
192.168.1.1 255.255.255.255 On-link 192.168.1.4 26
192.168.1.4 255.255.255.255 On-link 192.168.1.4 281
192.168.1.100 255.255.255.255 10.40.111.1 10.40.111.18 2
192.168.1.255 255.255.255.255 On-link 192.168.1.4 281
192.168.5.30 255.255.255.255 10.40.111.1 10.40.111.18 2
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.1.4 281
224.0.0.0 240.0.0.0 On-link 10.40.111.18 10000
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.1.4 281
255.255.255.255 255.255.255.255 On-link 10.40.111.18 10000
===========================================================================
Persistent Routes:
None
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
1 306 ::1/128 On-link
1 306 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
C:\Users\Matt> ping 192.168.1.100
Pinging 192.168.1.100 with 32 bytes of data:
General failure.
General failure.
General failure.
General failure.
Ping statistics for 192.168.1.100:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
C:\Users\Matt> ping 192.168.1.8
Pinging 192.168.1.8 with 32 bytes of data:
Reply from 192.168.1.8: bytes=32 time=19ms TTL=255
Reply from 192.168.1.8: bytes=32 time=15ms TTL=255
Reply from 192.168.1.8: bytes=32 time=9ms TTL=255
Reply from 192.168.1.8: bytes=32 time=7ms TTL=255
Ping statistics for 192.168.1.8:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 7ms, Maximum = 19ms, Average = 12ms
-Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2018 02:49 PM
Are you able to ping anything else on the LAN on the 192.168.1.0/24 subnet? I think that this maybe has something to do with the way you have set up Local Lan Access. The right way for LLA is to to have a split exclude ACL for a 0.0.0.0/32 network. This automatically adds to local LAN to split tunnel exclusion list. I think there may be a Windows Firewall rule that blocks traffic to 192.168.1.0/24 on the VPN adapter when local lan access is enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 02:49 PM
Hey Rahul,
I'll have to check if there is any other server on that subnet. But, I would assume I won't be able to ping them.
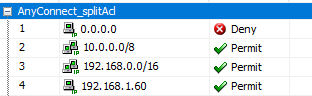
Does the Split exclude look like #1, in the screenshot below?
-Matt
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: