- Cisco Community
- Technology and Support
- Security
- VPN
- Issue with VPN access in AnyConnect and Site to Site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 07:21 AM - edited 02-21-2020 09:48 PM
vpnAny suggestions. Just added a site to site IPSEC tunnel from Cisco ASA running ASDM to a SonicWALL. Successfully got the tunnel live. However cannot reach anything in the cisco network from the SonicWALL. Also there was an existing Cisco AnyConnect SSL-VPN that was working and still connects. However that VPN can also no longer access anything in the network. So seems like a NAT issue or maybe an issue with the ACL? Strange that all the VPNs connect but can get to anything in the inside network... See the running-config below
ASA Version 8.6(1)
!
hostname xxxxxx-ASA
domain-name xxxxxxx.local
enable password xxxxxx
passwd xxxxxx
names
!
interface GigabitEthernet0/0
description To Switch 1
channel-group 1 mode on
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/1
description To Switch 2
channel-group 1 mode on
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
description LAN Failover Interface
!
interface GigabitEthernet0/3
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
description To TWC
nameif Outside
security-level 0
ip address 47.23.x.x 255.255.255.248 standby 47.23.x.x
!
interface GigabitEthernet0/5
description To VZW
nameif Backup
security-level 0
ip address 10.1.1.2 255.255.255.248 standby 10.1.1.3
!
interface Management0/0
shutdown
no nameif
no security-level
no ip address
management-only
!
interface Port-channel1
description Inside
nameif Inside
security-level 100
ip address 172.20.250.2 255.255.255.248 standby 172.20.250.3
!
boot system disk0:/asa861-smp-k8.bin
ftp mode passive
clock timezone EST -5
clock summer-time EST recurring
dns server-group DefaultDNS
domain-name xxxx.local
object network NAT_OUTSIDE
subnet 172.20.0.0 255.255.0.0
object network NAT_BACKUP
subnet 172.20.0.0 255.255.0.0
object network RemoteVPNNetwork
subnet 172.20.100.0 255.255.255.0
object network OLD
subnet 192.168.1.0 255.255.255.0
object network OLD_BACKUP
subnet 192.168.1.0 255.255.255.0
object network dvr1
host 192.168.1.162
object network dvr2
host 192.168.1.163
object network dvr3
host 172.20.50.41
object network XXXX
subnet 10.10.10.0 255.255.255.0
description XXXX
object network Remote
subnet 172.20.0.0 255.255.0.0
object network RemoteAppSvr
host 172.20.20.23
object service HTTPS
service tcp source eq https destination eq https
access-list outside_access_in extended permit icmp any any time-exceeded
access-list outside_access_in extended permit tcp any object dvr1 eq 1600
access-list outside_access_in extended permit tcp any object dvr2 eq 6100
access-list outside_access_in extended permit tcp any object dvr3 eq 6200
access-list backup_access_in extended permit icmp any any time-exceeded
access-list SplitTunnelNetworks standard permit 172.20.0.0 255.255.0.0
access-list SplitTunnelNetworks standard permit 192.168.1.0 255.255.255.0
access-list Outside_cryptomap extended permit ip object Remote object xxxxx
pager lines 24
logging enable
logging monitor debugging
logging asdm informational
no logging message 106015
no logging message 305012
no logging message 305011
no logging message 302015
no logging message 302014
no logging message 302013
no logging message 304001
no logging message 609002
no logging message 609001
no logging message 302016
no logging message 302021
no logging message 302020
mtu Outside 1500
mtu Backup 1500
mtu Inside 1500
ip local pool RemoteVPNAddressPool 172.20.100.50-172.20.100.254 mask 255.255.255.0
failover
failover lan unit primary
failover lan interface folink GigabitEthernet0/2
failover interface ip folink 172.20.255.1 255.255.255.252 standby 172.20.255.2
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-742.bin
no asdm history enable
arp timeout 14400
!
object network NAT_OUTSIDE
nat (Inside,Outside) dynamic interface
object network NAT_BACKUP
nat (Inside,Backup) dynamic interface
object network OLD
nat (Inside,Outside) dynamic interface
object network OLD_BACKUP
nat (Inside,Backup) dynamic interface
object network dvr1
nat (Inside,Outside) static interface service tcp 1600 1600
object network dvr2
nat (Inside,Outside) static interface service tcp 6100 6100
object network dvr3
nat (Inside,Outside) static interface service tcp 6200 6200
access-group outside_access_in in interface Outside
access-group backup_access_in in interface Backup
route Outside 0.0.0.0 0.0.0.0 47.23.103.105 1 track 1
route Backup 0.0.0.0 0.0.0.0 10.1.1.1 2
route Inside 172.20.0.0 255.255.0.0 172.20.250.1 1
route Inside 192.168.1.0 255.255.255.0 172.20.250.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authentication serial console LOCAL
http server enable
http 172.20.0.0 255.255.0.0 Inside
http 192.168.1.0 255.255.255.0 Inside
snmp-server host Inside 172.20.10.254 poll community ***** version 2c
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt noproxyarp Inside
sla monitor 123
type echo protocol ipIcmpEcho 8.8.8.8 interface Outside
num-packets 3
frequency 10
sla monitor schedule 123 life forever start-time now
crypto ipsec ikev1 transform-set AES_SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto map Outside_map 1 match address Outside_cryptomap
crypto map Outside_map 1 set pfs group1
crypto map Outside_map 1 set peer 71.244.x.x
crypto map Outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map Outside_map 1 set ikev2 ipsec-proposal 3DES
crypto map Outside_map interface Outside
crypto ca trustpoint SSL-VPN
enrollment self
keypair SSL-VPN-SELF-SIGNED
crl configure
crypto ca certificate chain SSL-VPN
certificate a4fb6255
308202d0
quit
crypto ikev2 policy 30
encryption 3des
integrity sha
group 2
prf sha
lifetime seconds 28800
crypto ikev2 enable Outside
crypto ikev1 enable Outside
crypto ikev1 policy 50
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
!
track 1 rtr 123 reachability
telnet timeout 5
ssh 172.20.0.0 255.255.0.0 Inside
ssh timeout 5
console timeout 0
management-access Inside
threat-detection basic-threat
threat-detection statistics port number-of-rate 2
threat-detection statistics protocol number-of-rate 2
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 172.20.250.1
ssl encryption 3des-sha1 aes256-sha1
webvpn
enable Outside
enable Backup
anyconnect image disk0:/anyconnect-win-3.1.01065-k9.pkg 1
anyconnect image disk0:/anyconnect-macosx-i386-3.1.03103-k9.pkg 2
anyconnect enable
tunnel-group-list enable
group-policy SplitTunnelGP internal
group-policy SplitTunnelGP attributes
dns-server value 192.168.1.250
vpn-simultaneous-logins 15
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SplitTunnelNetworks
default-domain value xxxxx.local
webvpn
anyconnect ask none default anyconnect
group-policy GroupPolicy_71.244.x.x internal
group-policy GroupPolicy_71.244.x.x attributes
vpn-tunnel-protocol ikev1 ikev2
username encrypted privilege 1
username encrypted privilege 1
username attributes
service-type remote-access
username encrypted privilege 15
username encrypted privilege 15
username encrypted
username attributes
service-type remote-access
username encrypted privilege 1
tunnel-group SplitTunnelTG type remote-access
tunnel-group SplitTunnelTG general-attributes
address-pool RemoteVPNAddressPool
default-group-policy SplitTunnelGP
tunnel-group SplitTunnelTG webvpn-attributes
group-alias SplitTunnel enable
tunnel-group 71.244.x.x type ipsec-l2l
tunnel-group 71.244.x.x general-attributes
default-group-policy GroupPolicy_71.244.x.x
tunnel-group 71.244.x.x ipsec-attributes
ikev1 pre-shared-key *****
isakmp keepalive disable
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
inspect pptp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:767b8df215943f6c3341c6ed4af59010
: end
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:39 AM
nat (INSIDE,OUTSIDE) source static remote remote destination static RemoteVPNNetwork RemoteVPNNetwork no-proxy-arp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 08:22 AM
Yes, you would need a nat rule to exempt traffic being natted from your local network to the remote network over the VPN tunnel.
Example:-
"nat (inside,outside) source static LOCAL_NETWORK LOCAL_NETWORK destination static REMOTE_NETWORK REMOTE_NETWORK no-proxy-arp"
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 10:53 AM
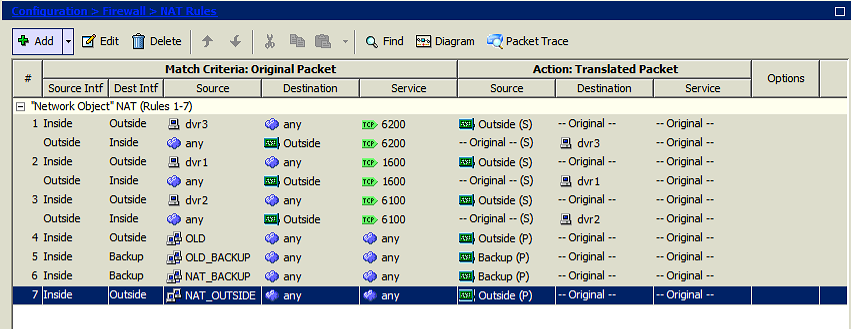
Here is the NAT table, isnt this covered in 7? NAT_OUTSIDE is the LAN subnet. If not can you explain which rule should be created.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 11:03 AM
Try this:-
nat (inside,outside) source static Remote Remote destination static xxxx xxxx no-proxy-arp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 11:16 AM - edited 11-16-2019 11:18 AM
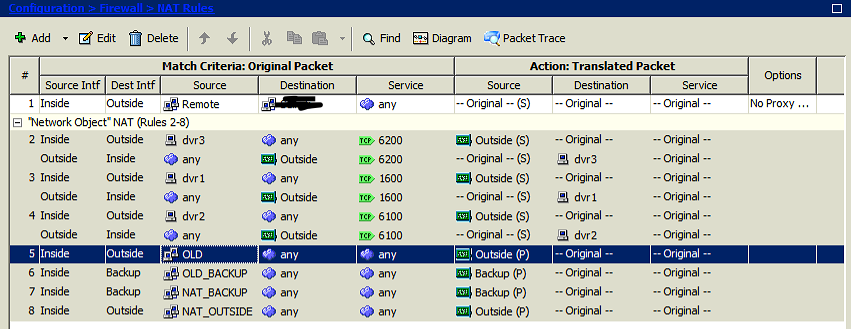
Added that rule, see visual below. Still no good to access the local network... So we cant access the xxxx to the remote and the SSLVPN was working and no longer can access the remote
Also in case it also may be an issue, the ACL:

Also the xxx is the end point of the site to site and the remote is an address object reference to the inside network
Thanks so much for the help so far!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2019 11:26 AM
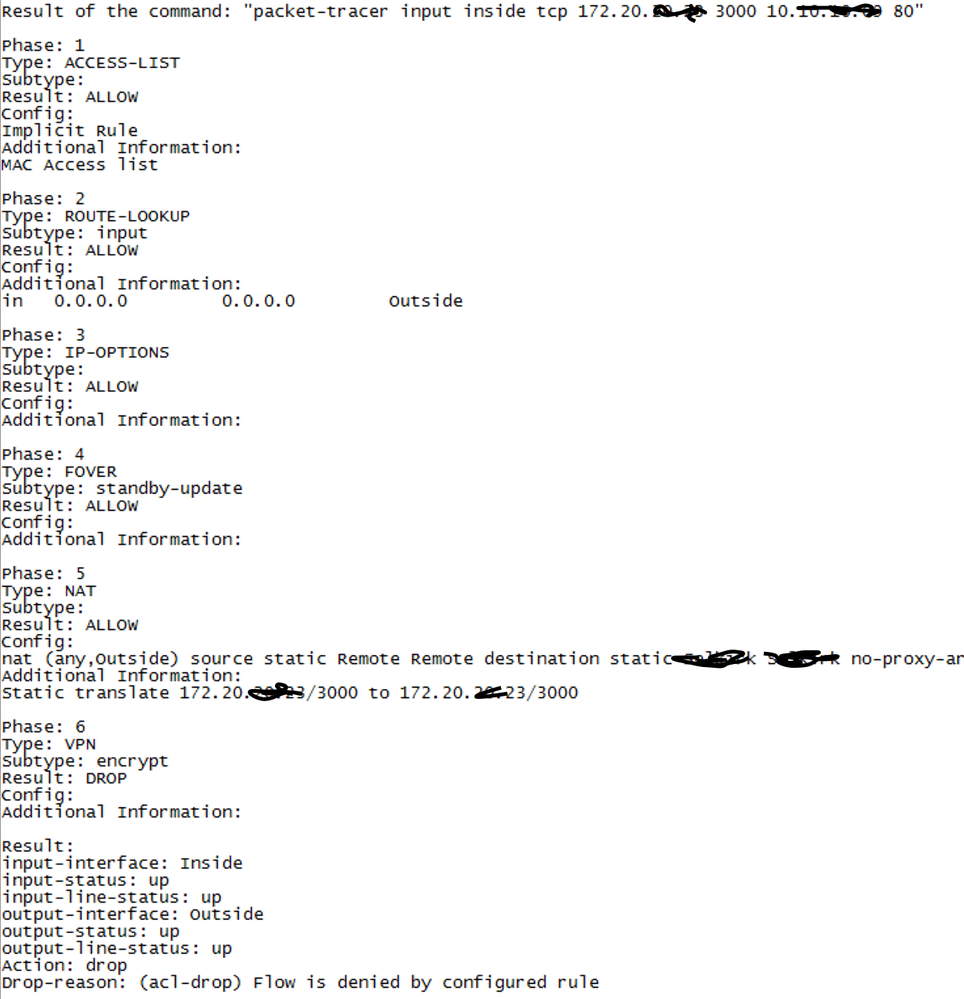
Test communication and then provide the output from the cli of the command "show nat" and "show crypto ipsec sa".
Also run packet-tracer from the cli and provide the output "packet-tracer input inside tcp 172.20.x.x 3000 x.x.x.x 80". Where x.x.x.x is an IP address on the remote network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 05:46 AM
I think that is some of the confusion... Remote is actually the local and xxxx is the remote network... Should I switch the source and destination?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:08 AM
Also export as requested:
Result of the command: "show nat"
Manual NAT Policies (Section 1)
1 (any) to (Outside) source static Remote Remote destination static xxxxx xxxxx no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (Inside) to (Outside) source static dvr3 interface service tcp 6200 6200
translate_hits = 7, untranslate_hits = 192
2 (Inside) to (Outside) source static dvr1 interface service tcp 1600 1600
translate_hits = 0, untranslate_hits = 80
3 (Inside) to (Outside) source static dvr2 interface service tcp 6100 6100
translate_hits = 16, untranslate_hits = 231
4 (Inside) to (Outside) source dynamic OLD interface
translate_hits = 17525333, untranslate_hits = 3914882
5 (Inside) to (Backup) source dynamic OLD_BACKUP interface
translate_hits = 65366, untranslate_hits = 5687
6 (Inside) to (Backup) source dynamic NAT_BACKUP interface
translate_hits = 591801, untranslate_hits = 477606
7 (Inside) to (Outside) source dynamic NAT_OUTSIDE interface
translate_hits = 138377224, untranslate_hits = 26657132
----------
Result of the command: "show crypto ipsec sa"
There are no ipsec sas
------------
So maybe the ACL is blocking?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:24 AM
In your crypto ACL and nat rules you need to specify the source as your internal network, with the destination as the remote network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:28 AM
Correct, both are defined that way. Still no flow. Def seems to be blocked by the ACL per these results. Thoughts?
Result of the command: "show nat"
Manual NAT Policies (Section 1)
1 (any) to (Outside) source static Remote Remote destination static xxxxx xxxxx no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
1 (Inside) to (Outside) source static dvr3 interface service tcp 6200 6200
translate_hits = 7, untranslate_hits = 192
2 (Inside) to (Outside) source static dvr1 interface service tcp 1600 1600
translate_hits = 0, untranslate_hits = 80
3 (Inside) to (Outside) source static dvr2 interface service tcp 6100 6100
translate_hits = 16, untranslate_hits = 231
4 (Inside) to (Outside) source dynamic OLD interface
translate_hits = 17525333, untranslate_hits = 3914882
5 (Inside) to (Backup) source dynamic OLD_BACKUP interface
translate_hits = 65366, untranslate_hits = 5687
6 (Inside) to (Backup) source dynamic NAT_BACKUP interface
translate_hits = 591801, untranslate_hits = 477606
7 (Inside) to (Outside) source dynamic NAT_OUTSIDE interface
translate_hits = 138377224, untranslate_hits = 26657132
----------
Result of the command: "show crypto ipsec sa"
There are no ipsec sas
------------
So maybe the ACL is blocking?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:35 AM
OK site - to - site is up!!!! Took making the any rule on the NAT.
However the SSL-VPN is still not allowing anyone to access the network.... Thoughts? It was working before we setup the site-to-site, what config change of the site to site could have blown out the SSL-VPN to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:39 AM
nat (INSIDE,OUTSIDE) source static remote remote destination static RemoteVPNNetwork RemoteVPNNetwork no-proxy-arp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 06:44 AM
YOU ARE MY HERO!!! FIXED!!!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: