- Cisco Community
- Technology and Support
- Security
- VPN
- My ASA cant ping the lan address
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2013 06:01 AM
I use ASA built ezvpn . I can access in the ASA and ping the inside port address sucessfully . But in my window7 cant ping the interconnect address 10.100.255.2 . I dont know how to solve the problem . hopefully , can help me . thank you .,...
the configure
asa5520# sh run
: Saved
:
ASA Version 7.2(3)
!
hostname asa5520
domain-name sxng
enable password DOAXe2w/ilkXwCIz encrypted
names
dns-guard
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address x.x.x.x 255.255.255.248
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 10.100.255.254 255.255.255.0
!
interface GigabitEthernet0/2
nameif dmz
security-level 50
ip address x.x.x.x 255.255.255.0
!
interface GigabitEthernet0/3
nameif wireless
security-level 10
ip address x.x.x.x 255.255.255.0
!
interface Management0/0
shutdown
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
boot system disk0:/pix723.bin
ftp mode passive
dns server-group DefaultDNS
domain-name sxng
access-list dmz_access_in extended permit ip any any
access-list dmz_access_in extended permit icmp any any
access-list split-tunnel standard permit 10.0.0.0 255.0.0.0
access-list inside_nat0_outbound extended permit ip any 10.100.254.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip 10.0.0.0 255.0.0.0 10.100.254.0 255.255.255.0
access-list outside_cryptomap_dyn_20 extended permit ip any 10.100.254.0 255.255.255.0
access-list acl_out extended permit icmp any any
access-list acl_out extended permit tcp any host x.x.x.x eq www
access-list acl_out extended permit tcp any host x.x.x.x eq 9000
access-list acl_out extended permit udp any host x.x.x.x eq 9000
........
......
access-list acl_out extended permit ip any 10.1.1.0 255.255.255.0
access-list inside_access_in extended permit tcp 10.1.10.0 255.255.255.0 any eq 5000
access-list acl_inside extended permit ip any any
access-list acl_inside extended permit icmp any any
access-list wireless_access_in extended permit ip any any
access-list wireless_access_in extended permit icmp any any
pager lines 24
logging enable
logging timestamp
logging list vpn-event level emergencies
logging list vpn-event message 109001-109028
logging list vpn-event message 113001-113019
logging buffer-size 5000
logging console informational
logging buffered debugging
logging trap debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu dmz 1500
mtu wireless 1500
mtu management 1500
ip local pool vpnpool 10.100.254.1-10.100.254.250 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
asdm image disk0:/asdm-507.bin
no asdm history enable
arp timeout 14400
global (outside) 1 x.x.x.x
global (dmz) 1 10.100.253.101-10.100.253.200 netmask 255.255.255.0
global (wireless) 1 172.16.255.101-172.16.255.200 netmask 255.255.255.0
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 10.1.1.14 255.255.255.255
nat (inside) 1 10.1.13.100 255.255.255.255
nat (wireless) 1 172.16.0.0 255.255.0.0
static (dmz,outside) tcp x.x.x.x www 10.100.253.1 www netmask 255.255.255.255
.......
.........
static (inside,dmz) 10.1.1.11 10.1.1.11 netmask 255.255.255.255
static (inside,dmz) 10.1.1.16 10.1.1.16 netmask 255.255.255.255
static (dmz,outside) x.x.x.x 10.100.253.20 netmask 255.255.255.255
static (dmz,outside) x.x.x.x 10.100.253.32 netmask 255.255.255.255
access-group acl_out in interface outside
access-group acl_inside in interface inside
access-group acl_inside out interface inside
access-group dmz_access_in in interface dmz
route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
route inside 10.0.0.0 255.0.0.0 10.100.255.1 1
route inside 10.0.0.0 255.0.0.0 10.100.255.2 1
route wireless 172.16.0.0 255.255.0.0 172.16.255.1 1
!
router ospf 1
network 10.67.180.0 255.255.255.255 area 0
network 0.0.0.0 0.0.0.0 area 1
log-adj-changes
!
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http 10.0.0.0 255.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto dynamic-map outside-dyn-map 20 set reverse-route
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 20
telnet 0.0.0.0 0.0.0.0 outside
telnet 10.0.0.0 255.0.0.0 inside
telnet 10.100.0.0 255.255.0.0 inside
telnet 10.100.255.0 255.255.255.0 inside
telnet 0.0.0.0 0.0.0.0 wireless
telnet timeout 10
ssh 0.0.0.0 0.0.0.0 outside
ssh timeout 30
console timeout 0
dhcpd dns x.x.x.x
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
!
service-policy global_policy global
group-policy sxnggroup internal
group-policy sxnggroup attributes
dns-server value 202.99.192.68
ip-comp enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-tunnel
username sxtrq password Y6cwK1wOhbhJ6YI/ encrypted
username maboai password R6eu6P1iKIwFIFjS encrypted
username winet password FwZ0ghxvIpXOepvf encrypted
tunnel-group sxnggroup type ipsec-ra
tunnel-group sxnggroup general-attributes
address-pool vpnpool
default-group-policy sxnggroup
tunnel-group sxnggroup ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:119ae137eef5ed97d38b4e2f90ed46d7
: end
asa5520# sh route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 202.97.158.177 to network 0.0.0.0
C x.x.x.x 255.255.255.248 is directly connected, outside
C 172.16.255.0 255.255.255.0 is directly connected, wireless
S 172.16.0.0 255.255.0.0 [1/0] via 172.16.255.1, wireless
S 10.0.0.0 255.0.0.0 [1/0] via 10.100.255.1, inside
[1/0] via 10.100.255.2, inside
C 10.100.255.0 255.255.255.0 is directly connected, inside
S 10.100.254.2 255.255.255.255 [1/0] via x.x.x.x, outside
C 10.100.253.0 255.255.255.0 is directly connected, dmz
S* 0.0.0.0 0.0.0.0 [1/0] via x.x.x.x, outside
asa5520# sh arp
outside x.x.x.x 00d0.d0c6.9181
outside x.x.x.x 00d0.d0c6.9181
outside 224.0.0.5 0100.5e00.0005
inside 224.0.0.5 0100.5e00.0005
inside 10.100.255.1 0000.0c07.acff
inside 10.100.255.2 001c.b0cb.5ec0
dmz 10.100.253.20 60a4.4c23.3032
dmz 224.0.0.5 0100.5e00.0005
dmz 10.100.253.1 001a.6436.6df6
wireless 224.0.0.5 0100.5e00.0005
wireless 172.16.255.1 0026.98c6.41c8

Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2013 09:05 AM
Try using the "show crypto ipsec sa" command to watch the encaps and decaps packets, hopefully it is not incrementing too fast. You should be able to see both increase when you successfully and only one side increase when it fails. Check both sides of the vpn and this should give you an idea of where the issue is. So if the Encaps packets are increasing on the ASA local to your Win7 PC and Decaps are increasing on the Remote ASA and Encaps are not then the issue is with packets coming from the remote side. Hopefully this will help you determine the location of the problem and then you can focus your search there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:38 AM
That could be, you may need to look into reverse route injection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2013 09:05 AM
Try using the "show crypto ipsec sa" command to watch the encaps and decaps packets, hopefully it is not incrementing too fast. You should be able to see both increase when you successfully and only one side increase when it fails. Check both sides of the vpn and this should give you an idea of where the issue is. So if the Encaps packets are increasing on the ASA local to your Win7 PC and Decaps are increasing on the Remote ASA and Encaps are not then the issue is with packets coming from the remote side. Hopefully this will help you determine the location of the problem and then you can focus your search there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 12:24 AM
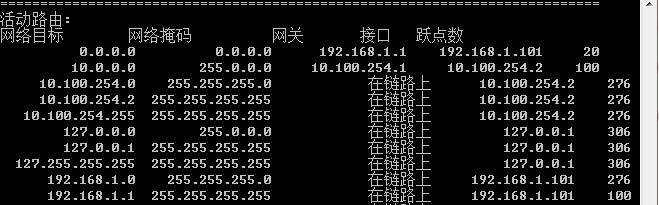
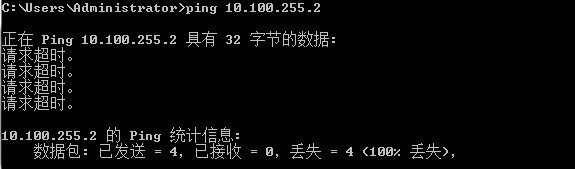
Tank you very much , I know what don you mean . but I tracert the 10.100.254.2 , one hop . but I tracert the 10.100.255.2 , missing , cant tracert it . someone say I have the route problem . I have a try .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 04:38 AM
That could be, you may need to look into reverse route injection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2013 08:44 PM
thank you very much . I solved it . it is the route problem , reverse route injection is ok . and I make the wrong route to the inside . summary route is not oK .
1\my win7 can connet the ASA by vpn client , so the policy is ok .
2\My win7 can tracert the ASA ,so can be sure the inverse route injection is ok ,
3\my win7 can not tracert the Access SW , so the route problem . my situation needs the route in detail . there is something wrong with summary route . so after changing the route , It work well .
hope this is benefit for you when trobleshooting . can you understand my words ? my english is so-so. thank you very much!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide