- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Problem: AnyConnect VPN (3.1.00495 SSL Client mode) ASA 5585
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem: AnyConnect VPN (3.1.00495 SSL Client mode) ASA 5585X-SSP20 (8.4.3 failover cluster)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2012 01:46 PM - edited 02-21-2020 06:26 PM
Hi everyone,
I'm quite stuck at the moment, and would very much appreciate some help.
I'm setting up a proof of concept for a client, so at first i set up a lab with an ASA5510 and the following config:
webvpn
svc image disk0:/anyconnect-win-3.1.00495-k9.pkg
enable INTERNET
svc enable
ip local pool SSLClientPool 172.40.0.1-172.40.31.254 mask 255.255.224.0
group-policy SSLClientPolicy internal
group-policy SSLClientPolicy attributes
dns-server value 172.19.16.20
vpn-tunnel-protocol svc
default-domain value vpn.test.com
address-pools value SSLClientPool
sysopt connection permit-vpn
tunnel-group SSLClientProfile type remote-access
tunnel-group SSLClientProfile general-attributes
default-group-policy SSLCLientPolicy
tunnel-group SSLClientProfile webvpn-attributes
group-alias SSLVPNClient enable
webvpn
tunnel-group-list enable
username testvpnuser password testvpnuser
username testvpnuser attributes
service-type remote-access
This config worked as a charm, i set up a tp cable between my test pc and the asa outside interface, no problems.
So naturally i thought "hey, lets transfer this to the production firewall".
so i configured the exact same config as above in the 5585, with i think the only exception is "svc" is now named "anyconnect".
I try to connect to the outside interface of my client firewall, and i get "connection timeout" from the anyconnect client.
My next step is of course to double check the config, everything is fine.
step after that is opening the real time log viewer and see whats going on, and when i filter the ip in the log for my test pc, i get the following five lines:
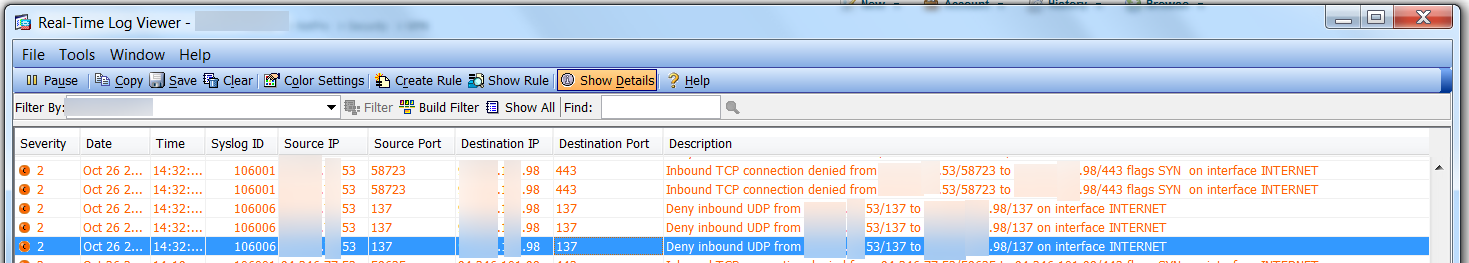
In clear text from today:
Oct 28 2012 20:19:42: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:43: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:45: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:48: %ASA-2-106001: Inbound TCP connection denied from X.X.X.53/60005 to Y.Y.Y.98/443 flags SYN on interface INTERNET
Oct 28 2012 20:19:51: %ASA-2-106001: Inbound TCP connection denied from X.X.X.53/60005 to Y.Y.Y.98/443 flags SYN on interface INTERNET
Oct 28 2012 20:19:42: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:43: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:45: %ASA-2-106006: Deny inbound UDP from X.X.X.53/137 to Y.Y.Y.98/137 on interface INTERNET
Oct 28 2012 20:19:48: %ASA-2-106001: Inbound TCP connection denied from X.X.X.53/60005 to Y.Y.Y.98/443 flags SYN on interface INTERNET
Oct 28 2012 20:19:51: %ASA-2-106001: Inbound TCP connection denied from X.X.X.53/60005 to Y.Y.Y.98/443 flags SYN on interface INTERNET
i have tried:
- to remove the anyconnect configuration, reapply it
- added access lists from any to outside interface for tcp/udp 443 ( i know, shouldnt need to because i have webvpn > anyconnect enable configured)
- rebooted the firewall
- ran the anyconnect guide
- cleared xlate
Hardware:
2 x ASA5585X-SSP20 (failover)
Test PC Anyconnect Client:
anyconnect-win-3.1.00495-k9
Does anyone know whats is up here? I just wish i could get past this problem (at least it seems pretty basic?)
i appreciate all the help i can get.
Best Regards,
Tommy
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2012 06:45 PM
Tommy,
What if you try through the Web browser? Does it work?
Thanks.
Portu.
Please rate any helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2012 12:10 PM
Hi Portu,
Thank you for your reply, appreciate it.
Unfortunately web browser doesnt work either.
Any other ideas?
Best Regards, Tommy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2012 12:15 PM
Could you please do the following?
no http server enable
!
webvpn
no enable INTERNET
!
http server enable
!
webvpn
enable INTERNET
Let me know.
Thanks.
Please rate any helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2012 12:49 PM
Hi again,
I tried the commands in the order above, but still the same problem.
Thanks for your suggestion though,
Best Regards, Tommy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 01:35 AM
Ok its seems as i have found the problem, it had to do with NAT, and in particular this line below:
ciscoasa(config-network-object)# nat (any,INTERNET) after-auto source static any interface
WARNING: All traffic destined to the IP address of the INTERNET interface is being redirected.
WARNING: Users may not be able to access any service enabled on the INTERNET interface.
so i'm still a bit confused what this line is for, and why it is blocking my outside interface from anyconnect.
if anyone can give me a good explenation, i would be glad.
Thank you,
Tommy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 06:14 AM
I think i found it.
ciscoasa(config-network-object)# nat (any,INTERNET) after-auto source static any interface unidirectional
now users from inside can reach outside, and i can connect with anyconnect vpn client to INTERNET interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 07:52 AM
Hi Tommy,
Check these links, maybe it will help you
http://networking-forum.com/viewtopic.php?f=35&t=24593
http://www.cisco.com/en/US/docs/security/asa/asa83/configuration/guide/nat_rules.html
Regards,
MKD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2012 03:37 PM
Hi Mohammed, thanks for your reply.
I managed to solve the actual problem, i can now:
- connect with anyconnect vpn client
- authenticate via certificate
- reach the inside network, servers and everything.
But i cannot reach the web as of now.
The funny thing is, that i can actually make nslookups from my client pc, because i can reach the inside interface and thereby the DNS server on that network.
but i cannot reach for example via ping 8.8.8.8 (google dns server)
My guess is that this is NAT related
anyone got a good idea?
This is my NAT configuration right now
FW01(config)# sh run | inc nat
nat (DMZ,INSIDE) source dynamic NET-VPN-DMZ-PORTWISE-NATED-BOTK HOST-172.18.254.69 destination static NET-VPN-CLIENT NET-VPN-CLIENT
nat (DMZ,INSIDE) source static NET-DMZ NET-DMZ destination static NET-ALL-INSIDE NET-ALL-INSIDE no-proxy-arp route-lookup
nat (DMZ,INSIDE) source static NET-DMZ NET-DMZ destination static NET-DRIFT-GROUPALL NET-DRIFT-GROUPALL no-proxy-arp route-lookup
nat (INSIDE,INTERNET) source static NET-NYNAS-ADMIN NET-NYNAS-ADMIN destination static NET-VPN-CLIENT NET-VPN-CLIENT no-proxy-arp route-lookup inactive
nat (DRIFT_MGMT,DMZ) source static NET-DRIFT-193.182.20.0 NET-DRIFT-193.182.20.0 destination static NET-DMZ NET-DMZ no-proxy-arp route-lookup
nat (DMZ,INSIDE) source dynamic NET-VPN-DMZ-DIRECTACCESS-CLIENT HOST-172.18.254.72 destination static NET-VPN-CLIENT NET-VPN-CLIENT
nat (INSIDE,INTERNET) source static any any destination static NETWORK_OBJ_172.40.0.0_19 NETWORK_OBJ_172.40.0.0_19 no-proxy-arp route-lookup
nat (DMZ,any) static X.X.X.100
nat (DMZ,any) static X.X.X.102
nat (DMZ,any) static X.X.X.101
nat (DMZ,any) static X.X.X.109
nat (DMZ,any) static X.X.X.116
nat (DMZ,any) static X.X.X.121
nat (DMZ,any) static X.X.X.108
nat (DMZ,any) static X.X.X.114
nat (DMZ,any) static X.X.X.119
nat (INSIDE,INTERNET) static X.X.X.117
nat (INSIDE,INTERNET) static X.X.X.112
nat (DMZ,any) static X.X.X.123
nat (DMZ,any) static X.X.X.124
nat (DMZ,any) static X.X.X.103
nat (DMZ,any) static X.X.X.120
nat (DMZ,any) static HOST-X.X.X.118
nat (DMZ,INSIDE) static 192.168.138.0
nat (any,DMZ) after-auto source static any any destination static HOST-X.X.X.107 HOST-192.168.138.53
nat (any,INTERNET) after-auto source static any interface unidirectional
i tried to add:
nat (INTERNET,INTERNET) source dynamic NETWORK_OBJ_172.40.0.0_19 interface
but that did not help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2012 02:52 AM
I solved it by adding a tunneled default route back to my Cat6500 (behind INSIDE interface).
now i can reach the office network, surf the internet and at the same time i get the WCCP that is configured on the firewall in order to filter the internet traffic, just as i wanted.
however, i cannot reach the servers on my DMZ, which is another interface on the Firewall
anyone with a clue? i will continue looking..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2012 01:56 AM
Some more info, this is how my setup looks at the moment.
So, there is a default route in ASA5585 to CAT6500 (172.19.16.1):
route INSIDE 0.0.0.0 0.0.0.0 172.19.16.1 tunneled
And as said before, i can reach INSIDE servers, for example 172.18.254.37 web server.
but i cannot reach DMZ servers, for example 192.168.138.36.
I ran a packet tracer and i get dropped on phase 7
FW01# packet-tracer input INTERNET tcp 172.40.0.10 61168 192.168.138.36 80 detailed
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd8ef47fa0, priority=1, domain=permit, deny=false
hits=1150613961, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=INTERNET, output_ifc=any
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 192.168.138.0 255.255.255.0 DMZ
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ACL-INTERNET-V1 in interface INTERNET
access-list ACL-INTERNET-V1 extended permit tcp any object-group GRP-DMZ-WEBSERV-PUB eq www
object-group network GRP-DMZ-WEBSERV-PUB
network-object object HOST-192.168.138.26
network-object object HOST-192.168.138.27
network-object object HOST-192.168.138.30
network-object object HOST-192.168.138.36
network-object object HOST-192.168.138.4
network-object object HOST-192.168.138.5
network-object object HOST-192.168.138.17
network-object object HOST-192.168.138.37
network-object object HOST-192.168.138.38
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd8ef6dce0, priority=13, domain=permit, deny=false
hits=573243, user_data=0x7ffd80c79040, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0
dst ip/id=192.168.138.36, mask=255.255.255.255, port=80, dscp=0x0
input_ifc=INTERNET, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd8f2dc420, priority=0, domain=inspect-ip-options, deny=true
hits=91123047, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
input_ifc=INTERNET, output_ifc=any
Phase: 5
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd93af9720, priority=79, domain=punt, deny=true
hits=1239, user_data=0x7ffd8d9526b0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=172.40.0.10, mask=255.255.255.255, port=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
input_ifc=INTERNET, output_ifc=any
Phase: 6
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map global-class
match default-inspection-traffic
policy-map global-policy
class global-class
inspect http
service-policy global-policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd8e0ae040, priority=70, domain=inspect-http, deny=false
hits=335695, user_data=0x7ffd905cccc0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=80, dscp=0x0
input_ifc=INTERNET, output_ifc=any
Phase: 7
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7ffd913c18b0, priority=70, domain=svc-ib-tunnel-flow, deny=false
hits=1263, user_data=0x1c000, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=172.40.0.10, mask=255.255.255.255, port=0
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
input_ifc=INTERNET, output_ifc=any
Result:
input-interface: INTERNET
input-status: up
input-line-status: up
output-interface: DMZ
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
Best regards,
Tommy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 02:59 AM
i got it working now, by spending many hours on google.
This line:
nat (INSIDE,INTERNET) source static any any destination static NETWORK_OBJ_172.40.0.0_19 NETWORK_OBJ_172.40.0.0_19 no-proxy-arp route-lookup
Changed it to:
nat (any,INTERNET) source static any any destination static NETWORK_OBJ_172.40.0.0_19 NETWORK_OBJ_172.40.0.0_19 no-proxy-arp
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: