- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Problem the TX automatically go to zero in vpn between 2 firewall cisco
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem the TX automatically go to zero in vpn between 2 firewall cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2019 10:45 PM - edited 03-12-2019 03:30 AM
Hello everyone,
I have 2 site and connected vpn by used firewall cisco, And have the problem every week repeated (TX go to zero), And I attached photo below:
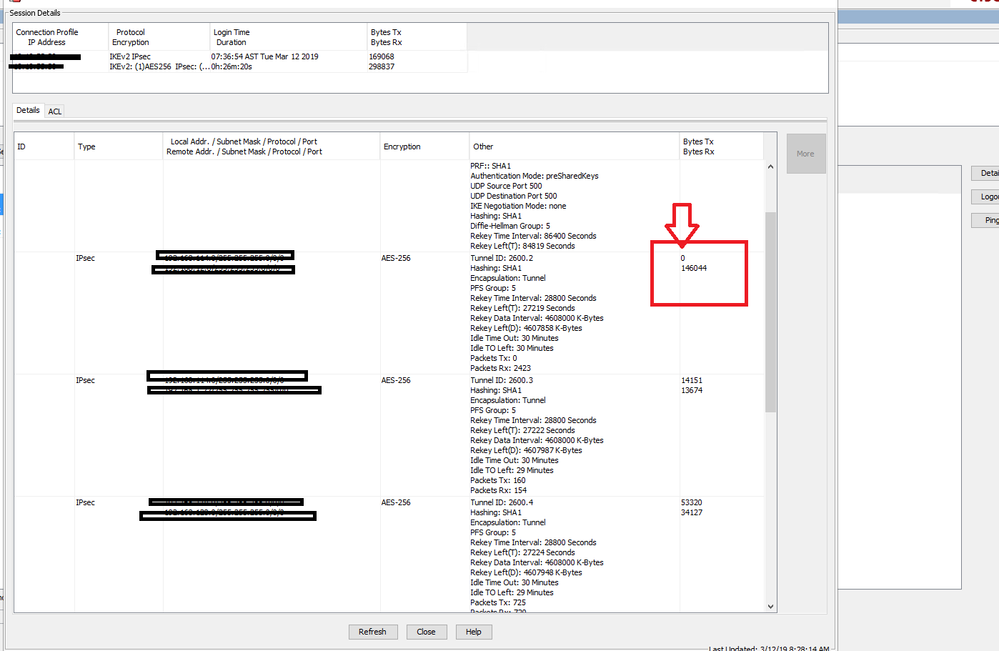
THANKS
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2019 01:16 AM - edited 03-28-2019 01:18 AM
Thank you for your replay,
I'm checked my asa version and capture photo below,
But after i changed when Mr. Deepak kumar told me to disable the keeplive on the remote site, In this time I'm waiting if the problem return back again or no, If you can checked the asa version if have with range versions problem or no?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2019 09:58 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 04:33 AM
Hi,
What is the final output after disabling the Keepalive? As discussed also share logs with us.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 10:58 PM
The device who was the problem in tx go to zero,The output is shown below,
10.10.53.12
Ha#show crypto isa sa detail
There are no IKEv1 SAs
IKEv2 SAs:
Session-id:51, Status:UP-ACTIVE, IKE count:1, CHILD count:6
Tunnel-id Local Remote Status Role
2770093475 10.10.53.12/500 10.10.53.30/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth v erify: PSK
Life/Active Time: 86400/465 sec
Session-id: 51
Status Description: Negotiation done
Local spi: 1131DF0401C7C222 Remote spi: F723B85CBC79C9F7
Local id: 10.10.53.12
Remote id: 10.10.53.30
Local req mess id: 3 Remote req mess id: 43
Local next mess id: 3 Remote next mess id: 43
Local req queued: 3 Remote req queued: 43
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.170/0 - 192.168.1.170/65535
ESP spi in/out: 0x219a261c/0x1eca3fd2
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.10.10/0 - 192.168.10.10/65535
ESP spi in/out: 0x1bdfc2e2/0x6470cbc0
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.22/0 - 192.168.1.22/65535
ESP spi in/out: 0x24993878/0xc7a4a4d
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.128.0/0 - 192.168.128.255/65535
ESP spi in/out: 0xcedc8912/0xe63716ad
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.12.0/0 - 192.168.12.255/65535
ESP spi in/out: 0x4553036e/0x5ce8405c
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.2/0 - 192.168.1.2/65535
ESP spi in/out: 0xaf22123/0xaaf16dd5
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
---------------------
Ha# show crypto ipsec sa
interface: ScopeSKY
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 192.168.12.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.12.0/255.255.255.0/0/0)
current_peer: 10.10.53.30
#pkts encaps: 74546, #pkts encrypt: 74546, #pkts digest: 74546
#pkts decaps: 59082, #pkts decrypt: 59082, #pkts verify: 59082
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 74546, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 5CE8405C
current inbound spi : 4553036E
inbound esp sas:
spi: 0x4553036E (1163068270)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4004844/28222)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFEFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x5CE8405C (1558724700)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4233379/28222)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.170
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.170/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 64, #pkts encrypt: 64, #pkts digest: 64
#pkts decaps: 64, #pkts decrypt: 64, #pkts verify: 64
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 64, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 1ECA3FD2
current inbound spi : 219A261C
inbound esp sas:
spi: 0x219A261C (563750428)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4331513/28275)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xBFFFFFFF
outbound esp sas:
spi: 0x1ECA3FD2 (516571090)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4101111/28275)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 192.168.128.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.128.0/255.255.255.0/0/0)
current_peer: 10.10.53.30
#pkts encaps: 143, #pkts encrypt: 143, #pkts digest: 143
#pkts decaps: 140, #pkts decrypt: 140, #pkts verify: 140
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 143, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: E63716AD
current inbound spi : CEDC8912
inbound esp sas:
spi: 0xCEDC8912 (3470559506)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (3916792/28233)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xE63716AD (3862369965)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4055032/28233)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.22
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.22/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 59, #pkts encrypt: 59, #pkts digest: 59
#pkts decaps: 54, #pkts decrypt: 54, #pkts verify: 54
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 59, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 0C7A4A4D
current inbound spi : 24993878
inbound esp sas:
spi: 0x24993878 (614021240)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4193275/28238)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00FFFFFF 0xFFF7FFFF
outbound esp sas:
spi: 0x0C7A4A4D (209341005)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (3962875/28238)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.10.10
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.10/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 47, #pkts encrypt: 47, #pkts digest: 47
#pkts decaps: 47, #pkts decrypt: 47, #pkts verify: 47
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 47, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 6470CBC0
current inbound spi : 1BDFC2E2
inbound esp sas:
spi: 0x1BDFC2E2 (467649250)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4008957/28237)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x0000FFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x6470CBC0 (1685113792)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4055037/28237)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.2
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 147, #pkts encrypt: 147, #pkts digest: 147
#pkts decaps: 171, #pkts decrypt: 171, #pkts verify: 171
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 147, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: AAF16DD5
current inbound spi : 0AF22123
inbound esp sas:
spi: 0x0AF22123 (183640355)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4101097/28219)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFEFFFF
outbound esp sas:
spi: 0xAAF16DD5 (2867949013)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 843776, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4147183/28219)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
----------------------
Ha# show vpn-sessiondb
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 2 : 52 : 2
IKEv2 IPsec : 2 : 52 : 2
---------------------------------------------------------------------------
Total Active and Inactive : 2 Total Cumulative : 52
Device Total VPN Capacity : 25
Device Load : 8%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv2 : 2 : 52 : 2
IPsec : 9 : 184 : 10
---------------------------------------------------------------------------
Totals : 11 : 236
---------------------------------------------------------------------------
Any help?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 12:11 AM
Hi,
I didn't find any issue on this device:
#pkts encaps: 74546, #pkts encrypt: 74546, #pkts digest: 74546 #pkts decaps: 59082, #pkts decrypt: 59082, #pkts verify: 59082
#pkts encaps: 64, #pkts encrypt: 64, #pkts digest: 64 #pkts decaps: 64, #pkts decrypt: 64, #pkts verify: 64
#pkts encaps: 143, #pkts encrypt: 143, #pkts digest: 143 #pkts decaps: 140, #pkts decrypt: 140, #pkts verify: 140
#pkts encaps: 147, #pkts encrypt: 147, #pkts digest: 147 #pkts decaps: 171, #pkts decrypt: 171, #pkts verify: 171
Can you explain bit more where did you find RX ZERO (0)?
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2019 10:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2019 11:54 PM
Any update after the last my reply discussion?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2019 01:28 AM - edited 04-14-2019 01:58 AM
..
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


