- Cisco Community
- Technology and Support
- Security
- VPN
- Re: RA VPN: Asynchronous NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RA VPN: Asynchronous NAT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2011 02:45 AM
All,
I have a functioning RA VPN to a site. It is all very simple bar one issue. I cannot access the DMZ once I have connected to the RA VPN.
I am using an ASA 5505 with 8.3
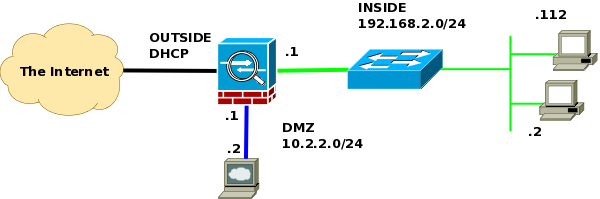
DMZ: 10.2.2.0/24
INSIDE: 192.168.2.0/24
OUTSIDE: DHCP
RA_SSL_ADDRESSES: 192.168.100.8/29
RA_IPSEC_ADDRESSES: 192.168.250.8/29
I can SSH/Ping everything in the 192.168.2.0/24 network, but I cannot access anything in the DMZ. I receive the following error in ASDM log.
10.2.2.2 Asymmetric NAT rules matched for forward and reverse flows; Connection for icmp src OUTSIDE:192.168.100.9 dst DMZ:10.2.2.2 (type 8, code 0) denied due to NAT reverse path failure
Here is what I perceive to be relevant config. Network diagram at end of config.
Any help much appreciated.
Cheers,
Conor
#### Start Config ####
interface Vlan1
nameif INSIDE
security-level 100
ip address 192.168.2.1 255.255.255.0
ipv6 address autoconfig
rip send version 2
rip receive version 2
!
interface Vlan10
nameif OUTSIDE
security-level 0
ip address dhcp setroute
!
interface Vlan20
nameif DMZ
security-level 50
ip address 10.2.2.1 255.255.255.0
!
interface Vlan90
description CONNECTION TO LAB
nameif LAB
security-level 50
ip address 10.9.9.1 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 10
speed 100
duplex full
!
interface Ethernet0/1
switchport access vlan 1
speed 100
duplex full
!
interface Ethernet0/2
switchport access vlan 20
speed 100
duplex full
!
object network DMZ_NETWORK
subnet 10.2.2.0 255.255.255.0
object network REMOTE_VPN_NETWORK
subnet 192.168.250.8 255.255.255.248
object network SSL_POOL_NET
subnet 192.168.100.8 255.255.255.248
!
ip local pool VPN_REMOTE_POOL 192.168.250.9-192.168.250.14 mask 255.255.255.248
ip local pool SSL_POOL 192.168.100.9-192.168.100.14 mask 255.255.255.248
!
nat (INSIDE,OUTSIDE) source static any any destination static REMOTE_VPN_NETWORK REMOTE_VPN_NETWORK
nat (INSIDE,OUTSIDE) source static any any destination static SSL_POOL_NET SSL_POOL_NET
nat (DMZ,OUTSIDE) source static any any destination static REMOTE_VPN_NETWORK REMOTE_VPN_NETWORK
nat (DMZ,OUTSIDE) source static any any destination static SSL_POOL_NET SSL_POOL_NET
!
nat (INSIDE,OUTSIDE) after-auto source dynamic any interface
nat (DMZ,OUTSIDE) after-auto source dynamic any interface
!
tunnel-group RA_HOME type remote-access
tunnel-group RA_HOME general-attributes
address-pool VPN_REMOTE_POOL
default-group-policy RA_HOME
tunnel-group RA_HOME ipsec-attributes
pre-shared-key *****
tunnel-group SSL_HOME type remote-access
tunnel-group SSL_HOME general-attributes
address-pool SSL_POOL
default-group-policy WEBVPN_POLICY
tunnel-group SSL_HOME webvpn-attributes
group-alias HOME enable
!
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol IPSec l2tp-ipsec svc webvpn
group-policy WEBVPN_POLICY internal
group-policy WEBVPN_POLICY attributes
vpn-tunnel-protocol svc webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value RemoteHome_splitTunnelAcl
group-policy RA_HOME internal
group-policy RA_HOME attributes
dns-server value x.x.75.75 x.x.75.193
vpn-tunnel-protocol IPSec webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value RemoteHome_splitTunnelAcl
default-domain value xxxxxxxxx.com
!
#### End Config ####
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2011 04:09 AM
Hi Conor,
Could you please paste the configuration of "sh run cry" here.
Regards,
Anisha
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2011 05:46 AM
Hi Anisha,
As requested: sh run crypto
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set transform-set
ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5
ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA
ESP-DES-MD5
crypto map OUTSIDE_map 1 match address OUTSIDE_cryptomap
crypto map OUTSIDE_map 1 set peer x.x.x.x
crypto map OUTSIDE_map 1 set transform-set ESP-AES-128-SHA
crypto map OUTSIDE_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map OUTSIDE_map interface OUTSIDE
crypto isakmp enable OUTSIDE
crypto isakmp policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto isakmp policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 10
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
On 22 February 2011 13:09, andamani <
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide