- Cisco Community
- Technology and Support
- Security
- VPN
- Static routes through site-to-site tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2012 11:49 AM
Hello,
I am using a Cisco ASA 5505
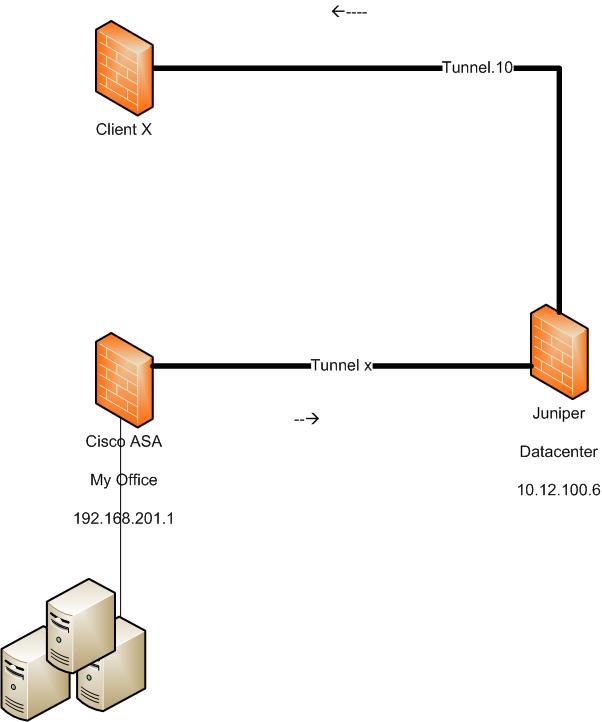
Here is a description of my topology.
Headquarters = 192.168.201.0
Client X = 172.16.0.0
Datacenter = 10.12.0.0
Site to Site Tunnels:
Headquarters ---> Datacenter
Datacenter ---> Client X
I want to ability for computers in the Headquarters subnet to access the Client X subnet.
I have tried setting up a static route to push all traffic destin for 172.16.0.0 to the datacenter, but was unsuccessful.
Does someone know a solution of how I can route all 172.16.0.0 through the tunnel.
I have tried ading a static route on my ASA but without success.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2012 11:14 PM
YOu can't just route the traffic from HQ through to client site.
You would need to include the HQ and Client subnet in the crypto ACL between the datacenter and client, as well as between the HQ and datacenter.
You would also need to configure NAT exemption on the client side.
IPSec tunnel typically is configured with specific subnet hence you would need to include the additional subnet to be able to route from HQ to client and vice versa.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2012 09:30 AM
Hi,
Assuming datacentre has two tunnels, one to Headquarter and one to Client, here is what needs to be configured for ACls.
Tunnel between HQ and Datacentre:
HQ Location
local - 192.168.201.0
remote - 10.12.200.0, 172.16.0.0
Datacenter:
local - 10.12.200.0, 172.16.0.0
remote - 192.168.201.0
Tunnel between Client and Datacentre:
Client
local - 172.16.0.0
remote - 10.12.200.0, 192.168.201.0
Datacenter:
local - 10.12.200.0, 192.168.201.0
remote - 172.16.0.0
Also proper translations will be required at all locations for traffic to pass.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2012 11:14 PM
YOu can't just route the traffic from HQ through to client site.
You would need to include the HQ and Client subnet in the crypto ACL between the datacenter and client, as well as between the HQ and datacenter.
You would also need to configure NAT exemption on the client side.
IPSec tunnel typically is configured with specific subnet hence you would need to include the additional subnet to be able to route from HQ to client and vice versa.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2012 08:11 AM
Hi Jennifer, thanks for the reply,
So is there a possibility if I add the 172.16.0.0 subnet to the tunnel on each end?
Right now the HQ tunnel to Datacenter has local of 192.168.201.0/24 and remote of 10.12.200.0/24
I would need to add the remote of 172.16.0.0/16 to the tunnel?
Also I would need to add the 192.168.201.0 to the datacenter --> client tunnel?
So here is the example of the tunnel networks:
HQ Location
local - 192.168.201.0
remote - 10.12.200.0, 172.16.0.0
Datacenter:
local - 10.12.200.0, 172.16.0.0
remote - 192.168.201.0
Client:
local - 172.16.0.0
remote - 10.12.200.0, 192.168.201.0
Think the above would work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2012 09:30 AM
Hi,
Assuming datacentre has two tunnels, one to Headquarter and one to Client, here is what needs to be configured for ACls.
Tunnel between HQ and Datacentre:
HQ Location
local - 192.168.201.0
remote - 10.12.200.0, 172.16.0.0
Datacenter:
local - 10.12.200.0, 172.16.0.0
remote - 192.168.201.0
Tunnel between Client and Datacentre:
Client
local - 172.16.0.0
remote - 10.12.200.0, 192.168.201.0
Datacenter:
local - 10.12.200.0, 192.168.201.0
remote - 172.16.0.0
Also proper translations will be required at all locations for traffic to pass.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

