- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Static to dynamic Site-to-Site VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2016 09:29 PM
I an having trouble setting up a Static to Dynamic IPSEC site-to-site tunnel
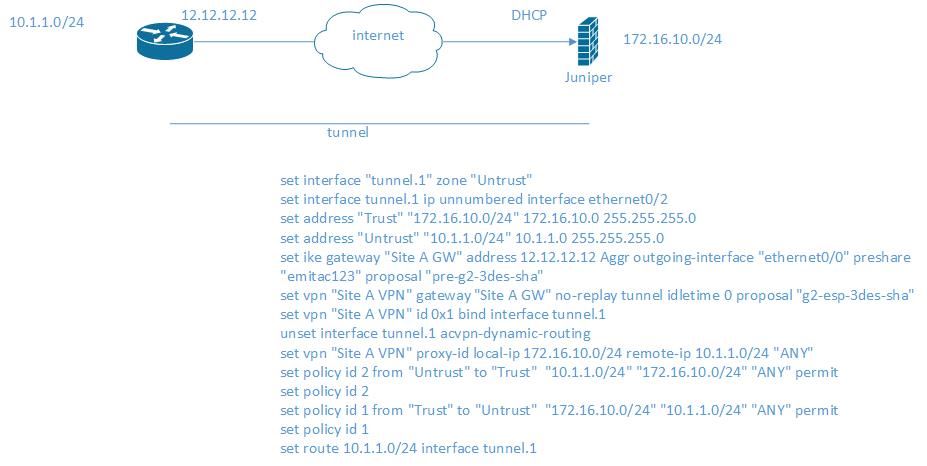
I have a juniper device on the remote end with dynamic IP. Mentioned below juniper SSG config, which i believe is true.
configuration is based on route-based VPN.
I need to know how to set up the cisco router for this. I dont know what to give for the remote IP.
is below config correct ?
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
crypto isakmp key emitac123 address 0.0.0.0 0.0.0.0
ip access-list extended VPN1-TRAFFIC
permit ip 10.1.1.0 0.0.0.255 172.16.10.0 0.0.0.255
crypto ipsec transform-set TS esp-3des esp-md5-hmac
crypto map VPN 1 ipsec-isakmp dynamic hq-vpn
crypto dynamic-map hq-vpn 10
set security-association lifetime seconds 86400
set transform-set TS
match address VPN1-TRAFFIC
interface Tunnel111
ip address x.x.x.x 255.255.255.0
tunnel source 12.12.12.12
tunnel destination X.X.X.X
tunnel mode ipsec ipv4
tunnel crypto-map hq-vpn
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2016 09:44 PM
I doubt you'll be using a tunnel interface for this. You'll just need to apply this on your outside interface.
Hopefully you don't need to configure any other VPNs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2016 12:06 AM
Hi, Thanks for the replies.
Will the below do for the cisco router?
crypto isakmp policy 10
encr aes 256
authentication pre-share
group 2
lifetime 28800
crypto isakmp key emitac123 address 0.0.0.0 0.0.0.0
crypto ipsec transform-set TS esp-des esp-md5-hmac
crypto dynamic-map D_MAP 20
set transform-set TS
match address 115
crypto map MAP_INT 20 ipsec-isakmp dynamic D_MAP
interface GigabitEthernet0/1
ip address 12.12.12.12 255.255.255.252
crypto map MAP_INT
ip nat inside source route-map NONAT interface GigabitEthernet0/1 overload
access-list 115 permit ip 10.1.1.0 0.0.0.255 172.16.10.0 0.0.0.255
access-list 115 deny ip 10.1.1.0 0.0.0.255 any
access-list 120 deny ip 10.1.1.0 0.0.0.255 172.16.10.0 0.0.0.255
access-list 120 permit ip ip 10.1.1.0 0.0.0.255 any
route-map NONAT permit 10
match ip address 120
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2016 12:13 AM
Looks good to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2016 07:26 AM
Hi
The configs seems to be ok like Philip said
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2016 09:50 PM
Hi
You are trying to do ipsec bpn site to site. You don't need a tunnel interface in cisco router. However your crypto map should be applied in outside/wan interface.
Thanks
PS: if this answering your issue Please don't forget to rate and select add correct answer
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide