- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Tunnel connect and disconnect again
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Tunnel connect and disconnect again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2018 01:56 PM - edited 03-12-2019 05:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 02:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 08:32 AM
Hi RJI,
Please review this configuration for IPSec:
crypto ipsec ikev1 transform-set azure-ipsec-proposal-set esp-aes-256 esp-sha-hmac
crypto ipsec security-association lifetime seconds 3600
crypto ipsec security-association lifetime kilobytes 102400000
tunnel-group 104.x.x.x type ipsec-l2l
tunnel-group 104.x.x.x ipsec-attribute
ikev1 pre-shared-key <Pre-Shared-Key>
Thanks,
Omid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 08:37 AM
I assume you control both ends of the tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 08:48 AM
By the way, the other end is Microsoft Azure(Policy base VPN connection) it is not ASA.
Here you are:show access:
access-list azure-vpn-acl extended permit ip object-group On-Prem-Net object-group Azure-Network
crypto map Cust-OutSell_map 4 match address azure-vpn-acl
crypto map Cust-OutSell_map 4 set peer x.x.x.x(Azure Gateway IP)
crypto map Cust-OutSell_map 4 set ikev1 transform-set azure-ipsec-proposal-set(esp-aes-256 esp-sha-hmac)
crypto ikev1 policy 5
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 28800
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 08:53 AM
On-Prem-Net
Azure-Network
Do you have access to the other Azure FW?
Can you confirm the settings are correct?....in regard to the subnets defined in the crypto map and the Phase 2 config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 09:09 AM
those are my on-prem(private) network range and Azure network, in this case, I use 20.20.10.0/24.
I used this steps to configure both:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 09:16 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 09:42 AM
Oh, you are right my object-group network IP range was 20.20.10.0 instead of 20.20.0.0/16.
Realy appreciate your guidance and time.
Omid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2018 02:04 PM
Now the VPN is connected but there is no traffic ESP on the connection.So the problem right now is in Phase 2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
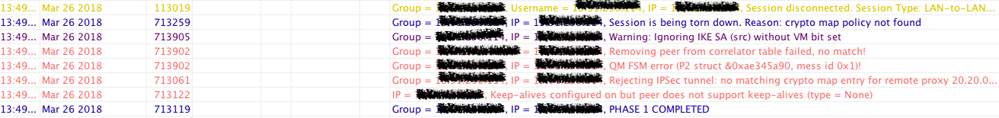
04-12-2018 09:19 AM
Please look at this error, That packet dropped!
Phase: 5
Type: VPN
Subtype: ipsec-tunnel-flow
Result: DROP
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xae2cbd68, priority=70, domain=ipsec-tunnel-flow, deny=false
hits=13, user_data=0x0, cs_id=0xadf3d260, reverse, flags=0x0, protocol=0
src ip/id=10.10.8.0, mask=255.255.252.0, port=0, tag=0
dst ip/id=10.20.0.0, mask=255.255.0.0, port=0, tag=0, dscp=0x0
input_ifc=Cust-OutSell, output_ifc=any
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: