- Cisco Community
- Technology and Support
- Security
- VPN
- Unable to access Safenet Licensing Server through Anyconnect VPN client session
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to access Safenet Licensing Server through Anyconnect VPN client session
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2015 09:54 AM - edited 02-21-2020 08:19 PM
The devs have stood up a Sentinel Licensing Server for LANSA programming licensing. My understanding of the server is that the LANSA software will check about every 15 minutes to validate the license over udp 5093. This works from within any subnet within the LAN without any problems. Since our devs like to work remotely as well across the VPN, this is where we have the issue. When connected to the Anyconnect VPN client, they are unable to validate with the server. They are able to RDP to a server, ping a server and reach it in any other way.
I put a support call in with Cisco and we have been working on that with a VPN specialist for days now. We have run wireshark on the licensing server in conjunction with packet tracing on the ASA5510 and found that the packet is received at the ASA and then dropped. The cisco engineer says it's not the ASA, although from my point of view that's all it can be. The switches do not have ACLs on them, the iPrism would not be touching that traffic since it's client based. Today, he wants to bring a switch specialist on the line to do a spanning port and packet sniff from there, although I do not see how that will diagnose anything.
Does anyone here have any experience or suggestions on the Sentinel Licensing Server and running over AnyConnect VPN? This is a VMWare 5.5 virtual server, Windows 2008R2.
Cisco ASA 8.4(3)
AnyConnect 3.1.06073
Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in Chicago 255.255.255.0 corpnet
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (corpnet,Cogent100Mbps) source static ODC-Corp ODC-Corp destination static A nyConnectVPN AnyConnectVPN no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface corpnet
Untranslate 192.168.5.88/5093 to 192.168.5.88/5093
Phase: 3
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in AnyConnectVPN 255.255.255.0 corpnet
Result:
input-interface: Cogent100Mbps
input-status: up
input-line-status: up
output-interface: corpnet
output-status: up
output-line-status: up
Action: drop
Drop-reason: (rpf-violated) Reverse-path verify failed
=~=~=~=~=~=~=~=~=~=~=~= PuTTY log 2015.06.17 08:43:09 =~=~=~=~=~=~=~=~=~=~=~=
show run
: Saved
:
ASA Version 8.4(3)
!
hostname chiasa02
domain-name xxxxxxx.com
enable password XXXXXXXXXXXXXXX encrypted
passwd XXXXXXXXXXXXXX encrypted
names
name 192.168.32.0 MacKey
name 192.168.5.0 Chicago
name 192.168.15.0 Alpharetta
name 192.168.55.0 BlueMountain
name 192.168.85.0 Laval
name 192.168.25.0 Mounds
name 192.168.65.0 Ripley
name 192.168.95.0 Taft
name 192.168.35.0 VernonHills
name 192.168.145.0 Bentonville
name 10.0.250.0 AnyConnectVPN
name 10.0.0.0 ODUK
name 10.0.38.0 AnyConnectDHCP
name 10.1.24.0 Ochlocknee
name 172.16.0.0 ChiClient
dns-guard
<--- More --->
!
interface Ethernet0/0
description Cogent 100Mbps (Circuit ID)
speed 100
duplex full
nameif Cogent100Mbps
security-level 0
ip address XXXXXXXXXXX 255.255.255.240 standby XXXXXXXXXXXXX
!
interface Ethernet0/1
description Chicago Corporate Network (VLAN10)
nameif corpnet
security-level 100
ip address 192.168.5.60 255.255.255.0 standby 192.168.5.61
!
interface Ethernet0/1.110
description VPN
vlan 110
nameif VPN
security-level 100
ip address 10.0.38.60 255.255.255.0
!
interface Ethernet0/2
description Guest Wireless Network
<--- More --->
shutdown
nameif GuestWireless
security-level 50
ip address 10.0.28.60 255.255.255.0
!
interface Ethernet0/3
description LAN/STATE Failover Interface
!
interface Management0/0
description Management
shutdown
nameif management
security-level 100
no ip address
management-only
!
boot system disk0:/asa843-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns domain-lookup corpnet
dns server-group DefaultDNS
name-server 192.168.5.19
name-server 192.168.5.20
<--- More --->
domain-name xxxxxx.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network MacKey
subnet 192.168.32.0 255.255.255.0
object network AnyConnectVPN
subnet 10.0.250.0 255.255.255.0
object network Chicago
subnet 192.168.5.0 255.255.255.0
object network Alpharetta
subnet 192.168.15.0 255.255.255.0
object network BlueMountain
subnet 192.168.55.0 255.255.255.0
object network Laval
subnet 192.168.85.0 255.255.255.0
object network Mounds
subnet 192.168.25.0 255.255.255.0
object network Ochlocknee
subnet 10.1.0.0 255.255.0.0
object network Ripley
subnet 192.168.65.0 255.255.255.0
object network Taft
subnet 192.168.95.0 255.255.255.0
object network VernonHills
<--- More --->
subnet 192.168.35.0 255.255.255.0
object network Bentonville
subnet 192.168.145.0 255.255.255.0
object network OchlockneeIDA
host 65.207.162.177
object network Chicago_AS400
host 192.168.5.5
object network CHIMAIL01-Primary
host 192.168.5.11
object network CHIMAIL01-NLB
host 192.168.5.21
object network CHIMAIL02-Primary
host 192.168.5.13
object network CHIMAIL02-NLB
host 192.168.5.22
object network CASARRAY-NLB
host 192.168.5.23
object network CHICAGODC7
host 192.168.5.51
object network CHICAGO-UMP
host 192.168.5.10
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network BentonvilleIDA
<--- More --->
host xxx.xxx.xxx.xxx
object network ODUK
subnet 10.0.0.0 255.255.255.0
object network Alpharetta_Voice
subnet 10.2.30.0 255.255.254.0
object network Bentonville_Voice
subnet 10.9.30.0 255.255.254.0
object network BlueMountain_Voice
subnet 10.3.30.0 255.255.254.0
object network Chicago_Voice
subnet 10.0.30.0 255.255.254.0
object network Laval_Voice
subnet 10.8.30.0 255.255.254.0
object network MacKey_Voice
subnet 10.10.30.0 255.255.254.0
object network Mounds_Voice
subnet 10.5.30.0 255.255.254.0
object network Ochlocknee_Voice
subnet 10.1.30.0 255.255.254.0
object network Ripley_Voice
subnet 10.4.30.0 255.255.254.0
object network Taft_Voice
subnet 10.7.30.0 255.255.254.0
object network VernonHills_Voice
<--- More --->
subnet 10.6.30.0 255.255.254.0
object network Chicago_ShoreTel_Server
host 10.0.30.11
object network SolarWinds
host 192.168.5.55
object network Canada_AS400
host 192.168.5.7
object network CHICAGODC8
host 192.168.5.20
object network CHICAGODC9
host 192.168.5.19
object network CHIFILE02
host 192.168.5.42
object network Laval_Silo01
host 192.168.85.60
object network Taft_Robot01
host 192.168.95.81
object network Taft_Robot02
host 192.168.95.82
object network Taft_Robot03
host 192.168.95.83
object network xxx.xxx.xxx.xxx
fqdn v4 xxx.xxx.xxx.xxx
object network AnyConnectDHCP
<--- More --->
subnet 10.0.38.0 255.255.255.0
object network Chicago_AS400_DEV
host 192.168.5.8
object network Chicago_HMC
host 192.168.5.64
object network ChicagoNetworkManagement
subnet 10.0.24.0 255.255.254.0
object network ChiClient
subnet 172.16.0.0 255.255.254.0
object network OckVPN
subnet 10.99.99.0 255.255.255.0
description Ochlocknee VPN
object network BMDAQ01
host 192.168.55.8
description Blue Mountain DAQ01
object network OCDAQ01
host 10.1.20.10
description Ochlocknee DAQ01
object network RPDAQ01
host 192.168.65.21
description Ripley DAQ01
<--- More --->
object network TFTDAQ01
host 192.168.95.11
description Taft DAQ01
object network VH_Security_Camera
host 192.168.35.65
description Axis Security Camera VH Office
object network CiscoRV320PLC
host 192.168.5.222
description PLC VPN Gateway device
object network CHIDEVLIC01
host 192.168.5.88
description Lansa Licensing
object network Taft_Mine
subnet 172.16.95.0 255.255.255.0
description Taft Mine Subnet
object network obj_192.168.5.88
host 192.168.5.88
object network obj_10.0.250.217
host 10.0.250.217
object-group network Voice_Subnets
network-object object Alpharetta_Voice
<--- More --->
network-object object Bentonville_Voice
network-object object BlueMountain_Voice
network-object object Chicago_Voice
network-object object Laval_Voice
network-object object MacKey_Voice
network-object object Mounds_Voice
network-object object Ochlocknee_Voice
network-object object Ripley_Voice
network-object object Taft_Voice
network-object object VernonHills_Voice
object-group network ODC-Corp
network-object object Alpharetta
network-object object AnyConnectVPN
network-object object BlueMountain
network-object object Chicago
network-object object Laval
network-object object Mounds
network-object object Ripley
network-object object Taft
network-object object VernonHills
group-object Voice_Subnets
network-object object Bentonville
network-object object AnyConnectDHCP
network-object object Ochlocknee
<--- More --->
network-object object ChiClient
object-group network Mail_Servers
network-object object CHIMAIL01-NLB
network-object object CHIMAIL02-NLB
network-object object CHIMAIL01-Primary
network-object object CHIMAIL02-Primary
network-object object CASARRAY-NLB
object-group network EDI-Amazon
object-group network corp_vpn_internal_access
network-object object Alpharetta
network-object object Bentonville
network-object object BlueMountain
network-object object Chicago
network-object object Laval
network-object object MacKey
network-object object Mounds
network-object object ODUK
network-object object Ripley
network-object object Taft
network-object object VernonHills
group-object Voice_Subnets
network-object object Ochlocknee
network-object object ChiClient
object-group network Corp_Bentonville
network-object object Alpharetta
network-object object AnyConnectVPN
network-object object BlueMountain
network-object object Chicago
network-object object Laval
network-object object MacKey
network-object object Mounds
<--- More --->
network-object object Ripley
network-object object Taft
network-object object VernonHills
network-object object AnyConnectDHCP
network-object object Chicago_Voice
network-object object Ochlocknee
network-object object ChiClient
object-group network Corp_UK
network-object object Chicago
network-object object Laval
network-object object Alpharetta
network-object object BlueMountain
network-object object Mounds
network-object object Ripley
network-object object Taft
network-object object VernonHills
network-object object AnyConnectVPN
network-object object AnyConnectDHCP
network-object object Ochlocknee
network-object object ChiClient
object-group network NetworkManagement
network-object object ChicagoNetworkManagement
object-group protocol TCPUDP
<--- More --->
protocol-object udp
protocol-object tcp
object-group network DAQVPN
description DAQ Access Group
network-object object BMDAQ01
network-object object OCDAQ01
network-object object RPDAQ01
network-object object TFTDAQ01
object-group service DevLicensing tcp-udp
port-object eq 5093
access-list corpnet_access_out extended permit tcp object-group Mail_Servers any eq smtp log alerts
access-list corpnet_access_out extended permit tcp object-group Mail_Servers any eq 587 log alerts
access-list corpnet_access_out extended deny tcp any any eq smtp log
access-list corpnet_access_out extended deny tcp any any eq 587 log
access-list corpnet_access_out extended permit tcp any any eq www log disable
access-list corpnet_access_out extended permit tcp any any eq https log disable
access-list corpnet_access_out extended permit tcp any any eq ftp log disable
access-list corpnet_access_out extended permit tcp any any eq ftp-data log disable
access-list corpnet_access_out extended permit udp any any eq domain log disable
access-list corpnet_access_out extended permit tcp any any eq domain log disable
access-list corpnet_access_out extended permit ip object Chicago_AS400 any log
access-list corpnet_access_out extended permit tcp any any log
access-list corpnet_access_out extended permit icmp any any log disable
access-list corpnet_access_out extended permit udp any any log
<--- More --->
access-list corpnet_access_out extended deny ip host 1.1.1.1 any inactive
access-list Inet2Inside extended permit object-group TCPUDP object AnyConnectVPN any eq 5093
access-list Inet2Inside remark [EDI] - All Connections
access-list Inet2Inside extended permit tcp object-group EDI object Chicago_AS400 log
access-list Inet2Inside remark [EMAIL] - SMTP to Mail Servers
access-list Inet2Inside extended permit tcp object-group MX_Logic object-group Mail_Servers eq smtp log
access-list Inet2Inside remark [EMAIL] - HTTPS for OWA
access-list Inet2Inside extended permit tcp any object-group Mail_Servers eq https log
access-list Inet2Inside remark [EMAIL] - HTTP for OWA
access-list Inet2Inside extended permit tcp any object-group Mail_Servers eq www log
access-list Inet2Inside remark [ICMP] - Allow ICMP to Firewall
access-list Inet2Inside extended permit icmp any any log
access-list Inet2Inside remark [ADSYNC] - AD Synchronization with MX Logic
access-list Inet2Inside extended permit tcp object-group MX_Logic object CHICAGODC7 eq ldaps log
access-list is_full_access extended permit ip any object-group ODC-Corp
access-list is_full_access extended permit icmp any object-group ODC-Corp
access-list is_full_access extended permit ip any object-group Voice_Subnets
access-list is_full_access extended permit icmp any object-group Voice_Subnets
access-list is_full_access extended permit ip any object-group NetworkManagement
access-list is_full_access extended permit icmp any object-group NetworkManagement
access-list taft_robots extended permit ip any object-group TAFT_Robots
access-list taft_robots extended permit icmp any object-group TAFT_Robots
access-list redistribute standard permit 192.168.145.0 255.255.255.0
access-list redistribute standard permit 192.168.32.0 255.255.255.0
<--- More --->
access-list redistribute standard permit 10.0.250.0 255.255.255.0
access-list redistribute standard permit 10.0.28.0 255.255.255.0
access-list Cogent100Mbps_cryptomap_2 extended permit ip object-group Corp_Bentonville object Bentonville
access-list corp_vpn_internal_access extended permit ip any object-group corp_vpn_internal_access
access-list corp_vpn_internal_access extended permit icmp any object-group corp_vpn_internal_access
access-list corp_vpn_internal_access extended permit object-group TCPUDP any object CHIDEVLIC01
access-list oduk_cryptomap extended permit ip object-group Corp_UK object ODUK
access-list mobile_devices extended permit udp any object CHICAGODC9 eq domain
access-list mobile_devices extended permit udp any object CHICAGODC8 eq domain
access-list mobile_devices extended permit tcp any object Chicago_AS400
access-list mobile_devices extended permit icmp any object Chicago_AS400
access-list mobile_devices extended permit tcp any object Canada_AS400
access-list mobile_devices extended permit icmp any object Canada_AS400
access-list mobile_devices extended permit tcp any object CHIMAIL01-Primary
access-list mobile_devices extended permit icmp any object CHIMAIL01-Primary
access-list mobile_devices extended permit tcp any object CHIMAIL02-Primary
access-list mobile_devices extended permit icmp any object CHIMAIL02-Primary
access-list mobile_devices extended permit tcp any object CASARRAY-NLB
access-list mobile_devices extended permit icmp any object CASARRAY-NLB
access-list mobile_devices extended permit tcp any object CHIFILE02
access-list mobile_devices extended permit icmp any object CHIFILE02
access-list mobile_devices extended permit ip any object Chicago_ShoreTel_Server
access-list mobile_devices extended permit icmp any object Chicago_ShoreTel_Server
access-list mobile_devices extended permit object-group TCPUDP object AnyConnectVPN object CHIDEVLIC01 object-group DevLicensing
<--- More --->
access-list split_tunnel_corp standard permit 192.168.5.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.15.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.25.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.35.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.55.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.65.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.85.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.95.0 255.255.255.0
access-list split_tunnel_corp standard permit 192.168.145.0 255.255.255.0
access-list split_tunnel_corp standard permit 10.0.250.0 255.255.255.0
access-list split_tunnel_corp standard permit 10.0.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.2.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.3.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.4.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.5.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.6.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.7.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.8.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.9.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.10.30.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.0.24.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.1.0.0 255.255.0.0
access-list split_tunnel_corp standard permit 172.16.0.0 255.255.254.0
access-list split_tunnel_corp standard permit 10.99.99.0 255.255.255.0
<--- More --->
access-list systemix_acl extended permit udp any object CHICAGODC9 eq domain
access-list systemix_acl extended permit udp any object CHICAGODC8 eq domain
access-list systemix_acl extended permit tcp any object Canada_AS400
access-list systemix_acl extended permit icmp any object Canada_AS400
access-list systemix_acl extended permit ip any object Laval
access-list systemix_acl extended permit icmp any object Laval
access-list atisupport extended permit udp any object CHICAGODC9 eq domain
access-list atisupport extended permit udp any object CHICAGODC8 eq domain
access-list atisupport extended permit ip any object-group Voice_Subnets
access-list atisupport extended permit ip any object VernonHills
access-list qos_remove_marking extended permit tcp any any
access-list qos_remove_marking extended permit udp any any
access-list laval_silo extended permit ip any object Laval_Silo01
access-list laval_silo extended permit icmp any object Laval_Silo01
access-list Methos extended permit ip any object Chicago_AS400
access-list Methos extended permit ip any object Chicago_AS400_DEV
access-list Methos extended permit ip any object Chicago_HMC
access-list daq_vpn extended permit udp any object CHICAGODC9 eq domain
access-list daq_vpn extended permit udp any object CHICAGODC8 eq domain
access-list daq_vpn remark DAQ Access for Programmers
access-list daq_vpn extended permit ip any object-group DAQVPN
access-list Cogent100Mbps_cryptomap_4 extended permit ip object-group Corp_Bentonville object Bentonville
access-list Cogent100Mbps_cryptomap_3 extended permit ip object-group Corp_Bentonville object Bentonville
access-list Cogent100Mbps_cryptomap_1 extended permit ip object Chicago object Taft_Mine
<--- More --->
access-list Cogent100Mbps_cryptomap extended permit ip object Chicago object Taft_Mine
!
tcp-map mss-map
!
pager lines 24
logging enable
logging timestamp
logging buffer-size 16384
logging monitor debugging
logging buffered informational
logging trap informational
logging asdm informational
logging facility 18
logging host corpnet 192.168.5.55
logging permit-hostdown
no logging message 106015
no logging message 313001
no logging message 313008
no logging message 106023
no logging message 710003
no logging message 106100
no logging message 302015
no logging message 302014
no logging message 302013
<--- More --->
no logging message 302018
no logging message 302017
no logging message 302016
no logging message 302021
no logging message 302020
logging message 106023 level informational
flow-export destination corpnet 192.168.5.10 9996
flow-export destination corpnet 192.168.5.55 2055
flow-export template timeout-rate 1
flow-export delay flow-create 15
mtu Cogent100Mbps 1500
mtu corpnet 1500
mtu VPN 1500
mtu GuestWireless 1500
mtu management 1500
ip local pool AnyConnectClients 10.0.250.100-10.0.250.254 mask 255.255.255.0
ip verify reverse-path interface Cogent100Mbps
ip audit name cogent_attack attack action alarm drop
ip audit name cogent_info info action alarm
ip audit name corpnet_attack attack action alarm drop
ip audit name corpnet_info info action alarm
ip audit interface Cogent100Mbps cogent_info
ip audit interface Cogent100Mbps cogent_attack
ip audit interface corpnet corpnet_info
<--- More --->
ip audit interface corpnet corpnet_attack
ip audit signature 1002 disable
ip audit signature 2000 disable
ip audit signature 2001 disable
ip audit signature 2004 disable
ip audit signature 2005 disable
ip audit signature 6051 disable
failover
failover lan unit secondary
failover lan interface Failover Ethernet0/3
failover key *****
failover link Failover Ethernet0/3
failover interface ip Failover 10.254.254.1 255.255.255.252 standby 10.254.254.2
no monitor-interface GuestWireless
no monitor-interface management
icmp unreachable rate-limit 1 burst-size 1
icmp permit any corpnet
icmp permit any echo-reply corpnet
icmp permit any echo corpnet
asdm image disk0:/asdm-732.bin
asdm history enable
arp timeout 60
nat (corpnet,Cogent100Mbps) source static ODC-Corp ODC-Corp destination static AnyConnectVPN AnyConnectVPN no-proxy-arp route-lookup
nat (corpnet,Cogent100Mbps) source static Corp_UK Corp_UK destination static ODUK ODUK
<--- More --->
nat (corpnet,Cogent100Mbps) source static Corp_Bentonville Corp_Bentonville destination static Bentonville Bentonville no-proxy-arp route-lookup
nat (corpnet,Cogent100Mbps) source static Taft_Mine Taft_Mine destination static Corp_Bentonville Corp_Bentonville no-proxy-arp route-lookup
!
object network Chicago_AS400
nat (corpnet,Cogent100Mbps) static xxx.xxx.xxx.xxx
object network CHIMAIL01-Primary
nat (corpnet,Cogent100Mbps) static xxx.xxx.xxx.xxx
object network CHIMAIL02-Primary
nat (corpnet,Cogent100Mbps) static xxx.xxx.xxx.xxx
object network CASARRAY-NLB
nat (corpnet,Cogent100Mbps) static xxx.xxx.xxx.xxx
object network CHICAGODC7
nat (corpnet,Cogent100Mbps) static xxx.xxx.xxx.xxx
object network obj_any
nat (corpnet,Cogent100Mbps) dynamic xxx.xxx.xxx.xxx
access-group Inet2Inside in interface Cogent100Mbps
access-group corpnet_access_out in interface corpnet
!
route-map redistribute permit 10
match ip address redistribute
!
!
router eigrp 5
no auto-summary
<--- More --->
network 10.0.28.0 255.255.255.0
network AnyConnectDHCP 255.255.255.0
network AnyConnectVPN 255.255.255.0
network ChiClient 255.255.254.0
network Chicago 255.255.255.0
network MacKey 255.255.255.0
network Bentonville 255.255.255.0
passive-interface default
no passive-interface corpnet
no passive-interface GuestWireless
no passive-interface management
redistribute static route-map redistribute
!
route Cogent100Mbps 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx 1
route corpnet Ochlocknee 255.255.255.0 192.168.5.4 1
route corpnet ChiClient 255.255.254.0 192.168.5.4 1
route corpnet Alpharetta 255.255.255.0 192.168.5.4 1
route corpnet Mounds 255.255.255.0 192.168.5.4 1
route corpnet VernonHills 255.255.255.0 192.168.5.4 1
route corpnet 192.168.45.0 255.255.255.0 192.168.5.4 1
route corpnet BlueMountain 255.255.255.0 192.168.5.4 1
route corpnet Ripley 255.255.255.0 192.168.5.4 1
route corpnet Laval 255.255.255.0 192.168.5.4 1
route corpnet Taft 255.255.255.0 192.168.5.4 1
<--- More --->
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record Mobile_Devices
description "iOS, Android, Windows Mobile, WebOS"
network-acl mobile_devices
webvpn
svc ask none default svc
dynamic-access-policy-record "Samir @ Meridian"
description "Samir @ Meridian"
network-acl is_full_access
priority 75
dynamic-access-policy-record DfltAccessPolicy
dynamic-access-policy-record Taft_Robots
description "Trinity Automation - Ryan Winters"
network-acl taft_robots
priority 75
dynamic-access-policy-record ATI_Support
description "ATI/ShoreTel Support"
<--- More --->
network-acl atisupport
priority 75
dynamic-access-policy-record ISTeam
description "IS Team Full Access Policy"
network-acl is_full_access
priority 100
dynamic-access-policy-record Systemix
description "Systemix Support"
network-acl systemix_acl
priority 75
webvpn
url-list none
svc ask none default svc
dynamic-access-policy-record "Endress and Hauser"
description "Endress & Hauser Silo Management"
network-acl laval_silo
priority 75
dynamic-access-policy-record RippeKingston
description "Gerald Combs @ RippeKingston"
network-acl Methos
priority 75
dynamic-access-policy-record "xxxxxx VPN Policy"
description "VPN Policy for xxxx & xxx"
network-acl is_full_access
<--- More --->
priority 100
dynamic-access-policy-record "Corporate Devices"
description "Corporate Provided Devices"
network-acl corp_vpn_internal_access
dynamic-access-policy-record OSX_Minimal
description "OSX Computers"
network-acl mobile_devices
dynamic-access-policy-record "Laval Devices"
description "Laval Laptops"
network-acl corp_vpn_internal_access
dynamic-access-policy-record External_Vendors
description "CRST, M&M, Kleen Products, Rotondo"
network-acl mobile_devices
priority 50
aaa-server ODC-Chicago protocol radius
aaa-server ODC-Chicago (corpnet) host 192.168.5.19
timeout 5
key *****
radius-common-pw *****
aaa-server ODC-Chicago (corpnet) host 192.168.5.20
key *****
radius-common-pw *****
aaa-server ODC-DCs protocol ldap
aaa-server ODC-DCs (corpnet) host 192.168.5.19
<--- More --->
ldap-base-dn dc=xxxxxx, dc=com
ldap-group-base-dn dc=xxxxxx,dc=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn cn=ASA LDAP, OU=Service Accounts, dc=xxxxxx, dc=com
server-type microsoft
aaa-server ODC-DCs (corpnet) host 192.168.5.20
ldap-base-dn dc=xxxxxx, dc=com
ldap-group-base-dn dc=xxxxxx, dc=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn cn=ASA LDAP, OU=Service Accounts, dc=xxxxxx, dc=com
server-type microsoft
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http Chicago 255.255.255.0 corpnet
http ChiClient 255.255.254.0 corpnet
http redirect Cogent100Mbps 80
snmp-server host corpnet 192.168.5.10 poll community *****
snmp-server host corpnet 192.168.5.55 poll community *****
snmp-server location Chicago
<--- More --->
snmp-server contact IS Request
snmp-server community *****
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
snmp-server enable traps syslog
snmp-server enable traps entity config-change
sysopt noproxyarp corpnet
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
<--- More --->
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
<--- More --->
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto engine large-mod-accel
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map Cogent100Mbps_map 1 match address Cogent100Mbps_cryptomap_4
crypto map Cogent100Mbps_map 1 set pfs group5
crypto map Cogent100Mbps_map 1 set peer xxx.xxx.xxx.xxx
crypto map Cogent100Mbps_map 1 set ikev1 transform-set ESP-AES-256-SHA
crypto map Cogent100Mbps_map 1 set ikev2 pre-shared-key *****
crypto map Cogent100Mbps_map 1 set reverse-route
crypto map Cogent100Mbps_map 3 match address oduk_cryptomap
crypto map Cogent100Mbps_map 3 set pfs group5
crypto map Cogent100Mbps_map 3 set peer xxx.xxx.xxx.xxx
crypto map Cogent100Mbps_map 3 set ikev1 transform-set ESP-AES-256-SHA
crypto map Cogent100Mbps_map 3 set reverse-route
crypto map Cogent100Mbps_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map Cogent100Mbps_map interface Cogent100Mbps
crypto map corpnet_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map corpnet_map interface corpnet
crypto map VPN_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map VPN_map interface VPN
crypto ca trustpoint ASDM_AnyConnect_
crl configure
<--- More --->
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
subject-name CN=192.168.5.60,CN=xxxxxx
crl configure
crypto ca trustpoint AnyConnectVPNSSL
enrollment terminal
subject-name CN=xxxxxx
keypair xxxxxxxxxx
crl configure
crypto ca trustpoint ASDM_TrustPoint0
revocation-check crl none
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
subject-name CN=xxx.xxx.xxx.xxx
keypair xxxxxxxx
crl configure
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_1
enrollment self
subject-name CN=192.168.5.60,CN=xxxxxx
crl configure
crypto ca certificate chain AnyConnectVPNSSL
certificate ca 0301
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
quit
crypto isakmp identity address
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable Cogent100Mbps client-services port 443
crypto ikev2 enable corpnet client-services port 443
crypto ikev2 enable VPN client-services port 443
crypto ikev1 enable Cogent100Mbps
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
<--- More --->
group 5
lifetime 86400
telnet timeout 20
ssh 0.0.0.0 0.0.0.0 corpnet
ssh timeout 20
ssh version 2
console timeout 10
management-access corpnet
vpn-sessiondb max-other-vpn-limit 250
vpn-sessiondb max-anyconnect-premium-or-essentials-limit 52
dhcprelay server 192.168.5.19 corpnet
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 192.168.5.1 source corpnet
ssl trust-point ASDM_Launcher_Access_TrustPoint_1 corpnet vpnlb-ip
ssl trust-point ASDM_TrustPoint1 Cogent100Mbps
ssl trust-point ASDM_Launcher_Access_TrustPoint_1 corpnet
ssl trust-point AnyConnectVPNSSL VPN
webvpn
enable Cogent100Mbps
<--- More --->
enable corpnet
no anyconnect-essentials
csd image disk0:/csd_3.6.6249-k9.pkg
anyconnect image disk0:/anyconnect-win-3.1.06073-k9.pkg 1
anyconnect image disk0:/anyconnect-macosx-i386-3.1.06073-k9.pkg 2
anyconnect image disk0:/anyconnect-win-3.1.05160-k9.pkg 3 regex "Windows NT"
anyconnect image disk0:/anyconnect-macosx-i386-3.1.05160-k9.pkg 4 regex "Intel Mac OS X"
anyconnect profiles xxxxxxdisk0:/xxx-xxx-vpn.xml
anyconnect enable
tunnel-group-list enable
group-policy DfltGrpPolicy attributes
wins-server value 192.168.5.19 192.168.5.20
dns-server value 192.168.5.19 192.168.5.20
vpn-tunnel-protocol ikev2 ssl-client ssl-clientless
group-lock value xxxxxx
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_tunnel_corp
default-domain value xxxxxx.com
address-pools value AnyConnectClients
webvpn
anyconnect ask none default anyconnect
group-policy GroupPolicy_xxxxxxinternal
group-policy GroupPolicy_xxxxxxattributes
wins-server value 192.168.5.19 192.168.5.20
<--- More --->
dns-server value 192.168.5.19 192.168.5.20
vpn-simultaneous-logins 30
vpn-idle-timeout 180
vpn-session-timeout 10080
vpn-tunnel-protocol ikev2 ssl-client ssl-clientless
group-lock value xxxxxx
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_tunnel_corp
default-domain value xxxxxx.com
split-tunnel-all-dns enable
msie-proxy method no-modify
address-pools value AnyConnectClients
webvpn
url-list value xxxxxx-Default
anyconnect mtu 1250
anyconnect keep-installer installed
anyconnect profiles value xxxxxx-VPN type user
anyconnect ask none default anyconnect
customization value xxxxxx-Default
url-entry disable
anyconnect ssl df-bit-ignore enable
anyconnect routing-filtering-ignore enable
always-on-vpn profile-setting
group-policy Taftmine internal
<--- More --->
group-policy Taftmine attributes
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec
group-policy GroupPolicy_xxx.xxx.xxx.xxxinternal
group-policy GroupPolicy_xxx.xxx.xxx.xxxattributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_xxx.xxx.xxx.xxxinternal
group-policy GroupPolicy_xxx.xxx.xxx.xxxattributes
vpn-tunnel-protocol ikev1
username xxxxxxadmin password xxxxxxx encrypted privilege 15
username view_only password xxxxxxencrypted
tunnel-group xxx.xxx.xxx.xxxtype ipsec-l2l
tunnel-group xxx.xxx.xxx.xxxgeneral-attributes
default-group-policy GroupPolicy_xxxxxxxx
tunnel-group xxx.xxx.xxx.xxxipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group xxx.xxx.xxx.xxxtype ipsec-l2l
tunnel-group xxx.xxx.xxx.xxxgeneral-attributes
default-group-policy GroupPolicy_xxxxxxx
tunnel-group xxx.xxx.xxx.xxxipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
<--- More --->
tunnel-group xxxxxx-VPN type remote-access
tunnel-group xxxxxx-VPN general-attributes
address-pool AnyConnectClients
authentication-server-group ODC-Chicago
authorization-server-group ODC-DCs
default-group-policy GroupPolicy_xxxxxx-VPN
password-management
tunnel-group xxxxxx-VPN webvpn-attributes
group-alias xxxxxx-VPN enable
tunnel-group 192.168.95.0 type ipsec-l2l
tunnel-group 192.168.95.0 general-attributes
default-group-policy Taftmine
tunnel-group 192.168.95.0 ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
class-map global-class
match any
class-map REMOVE_MARKING
match access-list qos_remove_marking
class-map inspection_default
match default-inspection-traffic
!
<--- More --->
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class global-class
flow-export event-type all destination 192.168.5.55 192.168.5.10
class class-default
<--- More --->
user-statistics accounting
policy-map strip_qos
class REMOVE_MARKING
!
service-policy global_policy global
smtp-server 192.168.5.23
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:5f57eab3dc2c2ba5736a15b761ae8b94
: end
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 02:24 AM
Can you maybe post a picture from a capture on the client on how the licensing packet looks?
If it's a broadcast or something like that it will not work. I do remember some weird licensing software, which we also use, which is exactly because of this not working. The users learned to avoid this software now via VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 07:36 AM
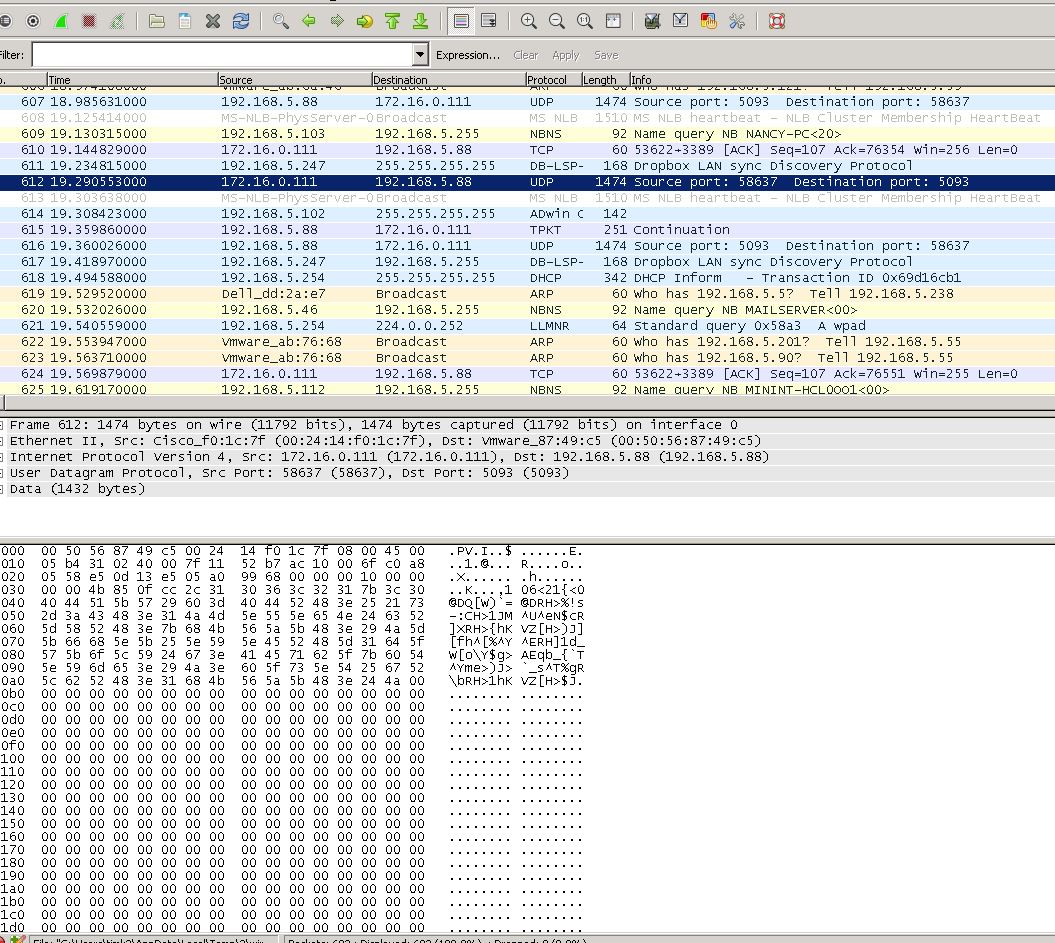
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 07:41 AM
On first view that looks good to me, the client even gets an anser in packet 616. I don't like the 613 packet though, do you happen to have a loadbalancer in use for the license server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 07:43 AM
No load balancer in use. It's a Windows 2008R2 virtual server in a VMWare environment with windows firewall disabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 07:52 AM
Just found this: http://sentineldiscussion.safenet-inc.com/topic/can-t-access-license-server-behind-a-nat
If it's the same license software, then you might need to do some configuration changes on the client side to get it working without the broadcast function.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 08:03 AM
It's not the same server as we do not use any dongles on the machines. I have spoken with LANSA regarding this and they say that it should work while Cisco cannot find an issue as I have spent hours on the phone with them in WebEx sessions. I use a WlmAdmin.exe software to check the licensing which works through the LAN but the packet is dropped at the ASA when connected to the VPN. I will check to see if the LANSA client does have a broadcast function that could be causing this, but according to LANSA, they do not. Attached is a screen cap of the testing software I am using and the error message.
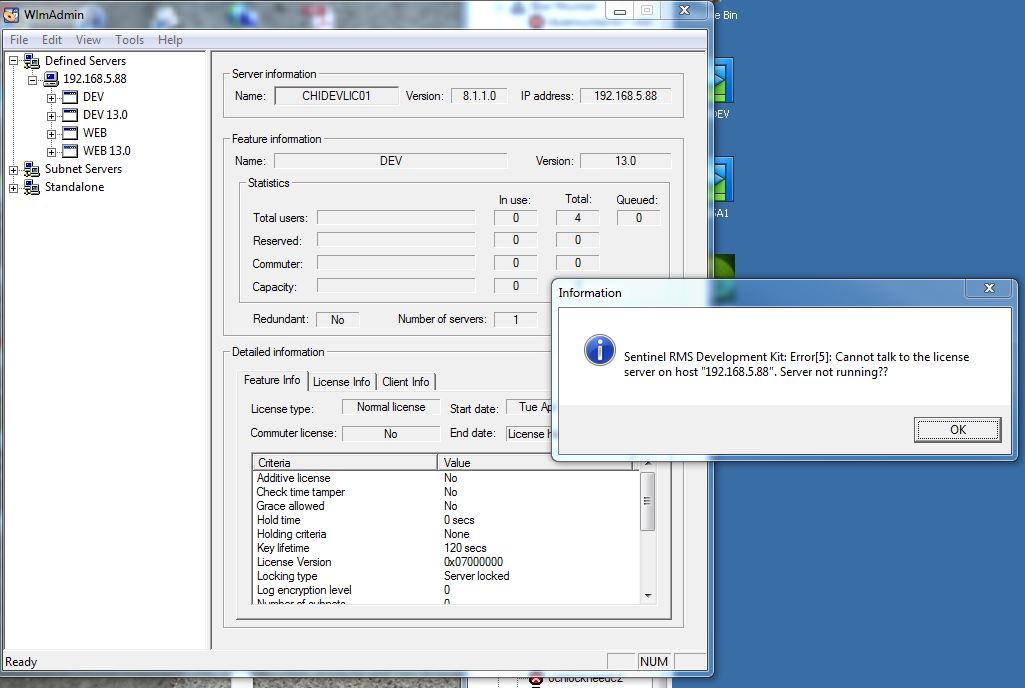
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 08:08 AM
Can you do two captures, one where your client is in your internal network, but different subnet and one on VPN?
You can filter the wireshark output by adding the display filter "ip.host == 192.168.5.88"
That way we can compare the packets and maybe see which reply is missing in the VPN trace. I don't really have an other idea besides doing it all again from the ground up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 08:14 AM
Well, the problem is that the packet will never reach the server from the VPN connected client, but I will work on that trace. The packet is dropped upon reaching the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2015 08:21 AM
That sounds like the packet is dropped by an inspect (or the lack of one) or by an other special ASA function which also verifies the packets (I forgot the name...).
For inspect drops (which aren't logged in some cases) try on the ASA: show service-policy
The second command to see the other drops, which are also not logged, use:
show asp drop
and check if the counters are increasing when the ASA drops the packet. I once had that with a loadbalancer which didn't reply on the same interface as it had received the packet on and the ASA dropped the TCP-Ack because of that (which is correct).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2019 11:20 PM
Might be problem occurring during traffic reverse path verification time. Could you please check once remove the below command.
ip verify reverse-path interface Cogent100Mbps
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide