- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN between ASA and Draytek on similar subnets
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 06:16 AM
Hi, I have a Draytek 2926 on IP range 10.1.8.0 / 255.255.255.0 and a Cisco ASA on IP range 10.1.1.0 / 255.255.0.0
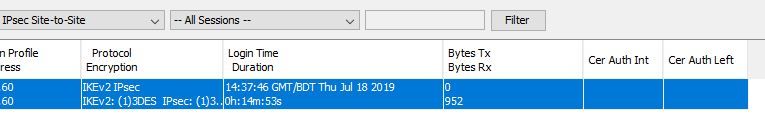
I've set up a site to site VPN but no traffic passes. I see if I ping from the Draytek to the 10.1.1 range that the byte count of the firewall RX on the Cisco goes up but that's all.
I'm guessing that this may be due to the subnet mask on the CIsco. I followed this how-to in order to set up the VPN: https://cloudrun.co.uk/networking/configuring-site-to-site-vpn-from-cisco-asa-to-a-draytek-router/
I am a novice with Cisco and use GUI only. If anyone can offer any advice I'd be grateful, thanks.
Solved! Go to Solution.
- Labels:
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 01:16 AM
Thanks. That didn't work either so I changed the IP addressing on the Draytek end to 192.168.11.0 and removed all settings from Cisco and Draytek for VPN and NAT/Access rules, and re-followed the first link I posted. Exactly the same results, no traffic passing.
Then I had a thought and moved the NAT rule higher up the table, and it started working!
Thanks for your help with this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 06:38 AM - edited 07-18-2019 06:43 AM
Hello
You are right, the packet is probably going on the inside on the Cisco ASA. The route on Cisco ASA for 10.1.1.0/ 16 point to the inside interface( interface can have a different name) and not to the interface which has the vpn config. Is it possible for you to define a subset of the networks on each side, in case they are differnet otherwise you would need to nat the network that you want to go over the VPN so the VPN is triggered and your subnets are able to talk over the VPN.
Regards
Shikha Grover
*****Please rate the helpful answers*******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 07:00 AM - edited 07-18-2019 07:06 AM
Thanks for the quick reply.
Anticipating that this was the issue I've made a change.
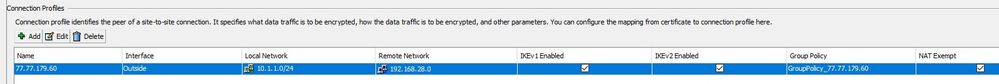
The CIsco (HA pair) is a live unit with a large network behind it which I am unable to make changes on easily, so on the Draytek I have changed the IP to 192.168.28.0 / 24, but the problem still remains.
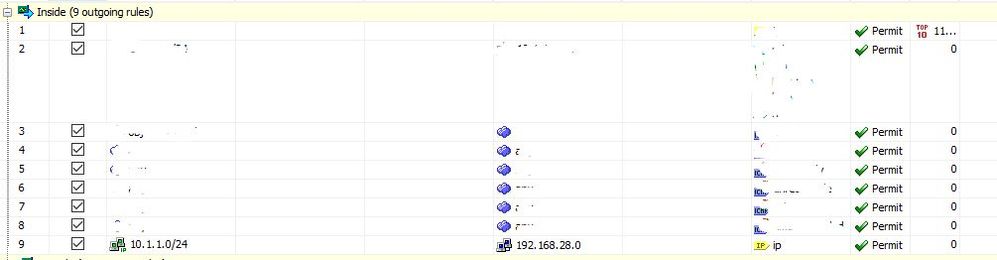
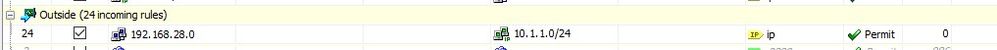
If there is anything missing on the how-to I followed it would be great to know. I attach some screenshots of the setup but I have followed the link exactly so that should tell you what I have done.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 07:32 AM
Hello,
I Suggest you please open a case with TAC, they can set it right for you. Since you are new to ASA and your devices are in production, I dont want us to make any changes that might lead to a outage on your end.
Regards
Shikha Grover
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 07:39 AM
I'm not sure we have a support contract on these devices as they were provided by the datacentre, and they are refusing to assist.
Any help here would be greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2019 07:50 AM
try this:-
https://www.petenetlive.com/KB/Article/0001446
yours would be scenario 1. the other end will also need to take care of natting.
the other end as per the example will receive the traffic with source 172.16.1.0/24 and destination as 172.16.2.0/24 and it would need to convert 172.16.2.0/24 to 192.168.1.10/24.
Better to open a case.. ,...
Regards
Shikha Grover
*****rate all helpful answers*****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 01:16 AM
Thanks. That didn't work either so I changed the IP addressing on the Draytek end to 192.168.11.0 and removed all settings from Cisco and Draytek for VPN and NAT/Access rules, and re-followed the first link I posted. Exactly the same results, no traffic passing.
Then I had a thought and moved the NAT rule higher up the table, and it started working!
Thanks for your help with this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 04:59 AM
hello,
Glad to know you have been able to get it to work.
The NAT rule might not have been getting hit. like access-list, NAT rule is also top to bottom.
Regards
Shikha Grover
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide