- Cisco Community
- Technology and Support
- Security
- VPN
- VPN from VRF Router and CISCO ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN from VRF Router and CISCO ASA 5510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2012 04:21 PM
Hi guys,
I have a problem with connection beetween a Router and Cisco ASA 5510 conection through VPN.
The originator VPN have this configuration in router
===================================
access-list 181 remark SIAE
access-list 181 permit ip host 200.7.215.11 host 190.152.16.30
access-list 181 permit ip host 200.7.215.98 host 190.152.16.30
access-list 181 permit ip host 200.7.215.99 host 190.152.16.30
!
crypto ipsec transform-set SOLO_3DES esp-3des esp-sha-hmac
!
crypto keyring vrf_otecel_ipsec1_keys vrf otecel_ipsec1
pre-shared-key address 190.152.16.30 key AAAAAAA
!
crypto isakmp profile vrf_otecel_ipsec1_profile
match identity address 190.152.16.30 255.255.255.255 otecel_ipsec1
!
crypto map vrf_otecel_ipsec1 365 ipsec-isakmp
description ---- SIAE ----
set peer 190.152.16.30
set transform-set SOLO_3DES
set isakmp-profile vrf_otecel_ipsec1_profile
match address 181
=========================================
I have this configuration in my Cisco ASA 5510 ver 8.2(3). Initially I thinked: It's not posible because the other end has a VPN VRF based, but I tried in this way:
ASA Version 8.2(3)
===============
interface Ethernet0/0
nameif outside
security-level 0
ip address 190.152.216.30 255.255.255.252
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
===============
object-group network DM_INLINE_NETWORK_1
network-object host 10.114.0.12
network-object host 10.114.0.13
network-object host 10.114.0.14
=========
object-group network DM_INLINE_NETWORK_4
network-object host 200.7.215.11
network-object host 200.7.215.98
network-object host 200.7.215.99
access-list inside_nat0_outbound extended permit ip 192.168.1.0 255.255.255.0 any
access-list inside_access_in extended permit icmp any any
access-list inside_access_in extended permit ip any any
access-list natin standard permit 192.168.1.0 255.255.255.0
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit ip any any
access-list outside_access_in extended permit esp any any
access-list outside_access_in extended permit ah any any
access-list outside_access_in extended permit gre any any
access-list outside_2_cryptomap extended permit ip host 190.152.216.30 object-group DM_INLINE_NETWORK_4
access-list outside_2_cryptomap extended permit ip 192.168.1.0 255.255.255.0 object-group DM_INLINE_NETWORK_1
=============
route outside 0.0.0.0 0.0.0.0 190.152.216.29 1
======
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside_map 2 match address outside_2_cryptomap
crypto map outside_map 2 set connection-type originate-only
crypto map outside_map 2 set peer 200.24.221.26
crypto map outside_map 2 set transform-set ESP-3DES-SHA
crypto map outside_map 2 set nat-t-disable
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
======
tunnel-group 200.24.221.26 type ipsec-l2l
tunnel-group 200.24.221.26 ipsec-attributes
pre-shared-key AAAAAAA
Is possible the connection?
In this case what I have to do in Cisco ASA because only have to connect through public address and no matter the local LAN.
At this time I have this errors:
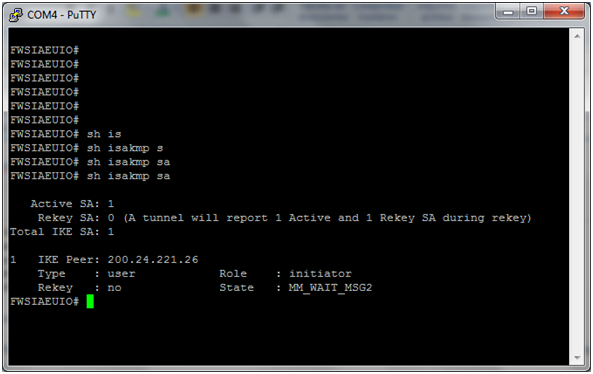
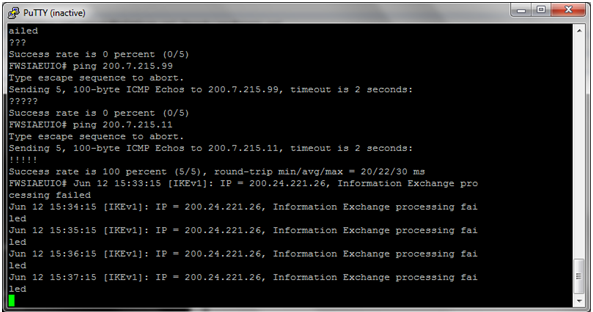
Thank you for your advice!!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2012 08:20 PM
From part of the config on the ASA, I can see some conflicting configuration.
Are you trying to PAT your VPN interesting traffic to the ASA outside interface, or are you trying to configure NAT exemption? This will determine what to be configured on the crypto ACL.
Please share all your NAT statement as well.
Secondly, the crypto ACL needs to mirror image between the ASA and router, currently you have 1 extra line on your ASA crypto ACL (outside_2_cryptomap)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2012 07:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2012 11:22 PM
On ASA, pls configure the following:
access-list outside_2_cryptomap extended permit ip 192.168.1.0 255.255.255.0 object-group DM_INLINE_NETWORK_1
no access-list outside_2_cryptomap extended permit ip host 190.156.16.30 object-group DM_INLINE_NETWORK_1
On router, pls configure the following:
- Remove the following access-list:
access-list 181 permit ip host 200.7.215.11 host 190.152.16.30
access-list 181 permit ip host 200.7.215.98 host 190.152.16.30
access-list 181 permit ip host 200.7.215.99 host 190.152.16.30
- and just configure the following:
access-list 181 permit ip host 200.7.215.11 192.168.1.0 255.255.255.0
access-list 181 permit ip host 200.7.215.98 192.168.1.0 255.255.255.0
access-list 181 permit ip host 200.7.215.99 192.168.1.0 255.255.255.0
Clear the tunnels on both ends and try to connect again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2012 08:25 AM
Hello Jennifer,
The big problem is the remote end is an ISP router and they don´t want change the access list as you suggest me. In this escenario the ISP only want to create an IPSEC tunnel beetween the Public IPs, and permit in my side, to access other three public IPs 200.7.215.11, 200.7.215.98 and 200.7.215.99 and no more.
This happend because the ISP has the network 192.168.1.0/24 in some point in their internal network and no want to create a conflict in routes, from their point of view the ISP only want to see my public IP 190.152.16.30 and no matter the internal network.
They say me all my network has to NATed as my public IP to their network but the traffic go over the tunnel.
Is possible to ASA to make this job??
And how can I do this? I neer an extra equipment like a router? I need other Public IP to create the tunnel and then NATed the traffic to my internal network? I need put routes to reach the tunnel from my Internal Network
At this time, only complete the PHASE 1 successful
but the Phase 2 is not possible
I appreciate so much your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2012 04:01 PM
you can PAT your internal LAN to a public IP.
The crypto map has to be defined for the PAT address to the remote LAN , as NAT is taking place first.
please post " sh cry isa sa" and "sh cry ipsec sa"
regards
Claudio
Sent from Cisco Technical Support iPad App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2012 08:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2012 07:32 AM
The following line needs to be "permit" instead of "deny":
access-list outside_2_cryptomap extended deny ip interface outside object-group DM_INLINE_NETWORK_1
To change it to:
access-list outside_2_cryptomap extended permit ip interface outside object-group DM_INLINE_NETWORK_1
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

