- Cisco Community
- Technology and Support
- Security
- VPN
- VPN in Active/Active ASA escenario with router in one end
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN in Active/Active ASA escenario with router in one end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2012 11:09 AM
Hi guys!! I have a big trouble resolving a issue with ASA in Active/Active and VPNs First I have this escenario |
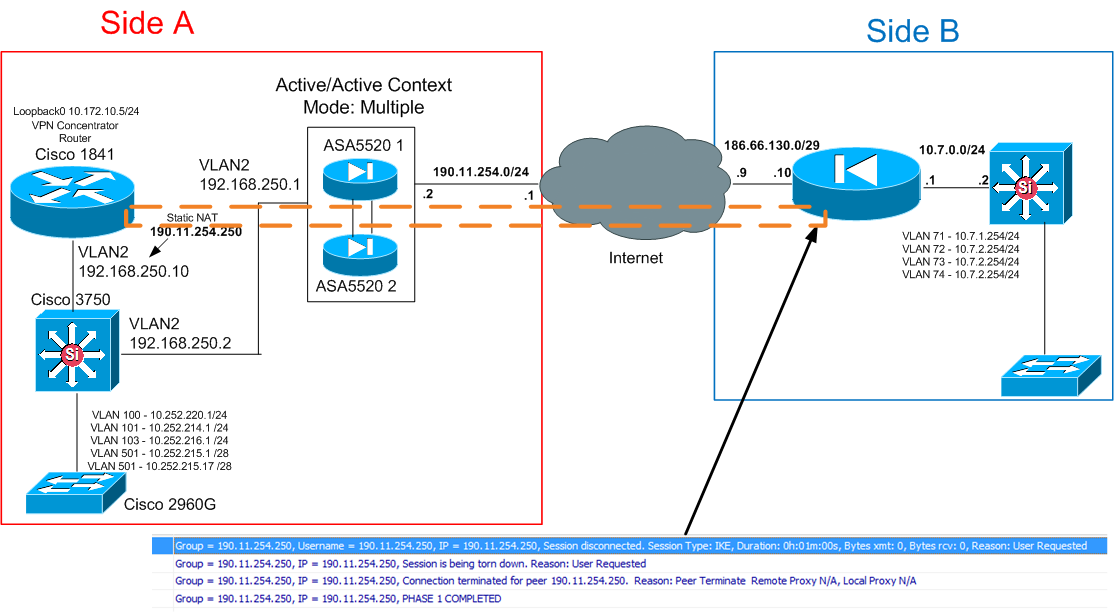
Because in Active/Active implementation I cannot use any VPN function, I have to put a Router (1841) behind the ASA arrangement to operate as VPN Concentrator. For VPN Client (Dynamic VPN) everything works fine, but I have a big trouble with VPN Site-to-Site. In graphic, you can see the error in the remote end.
I need to connect all VLANs in one end (Side A) to all VLANs in other end (Side B). Because I cannot use directly the Public IP of ASA Arrangement (190.11.254.2) I created a complete NAT of one IP available in public range to the router, for that reason the router appears as 190.11.254.250 and I used this IP to create the IPSec Site-to Site. The network in this side consists in Swith 3750 for InterVLAN routing and many 2960G as access switch.
In the other end the network is more simple and only have an ASA 5510 acting as VPN concentrator and firewall, then a Swith for Intervlan routing, and one switch for access.
Next, I put the relevant information in the equipment, in the information you see below I make the ACLs based in Loopback connection
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!FW_SideA (Context Admin)
ASA Version 8.4(2) <context>
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
interface GigabitEthernet0/0
description Hacia el Internet (Conex. al GE0/2 de RTR14_CORE 2951)
nameif Outside
security-level 0
ip address 190.11.254.2 255.255.254.0 standby 190.11.254.3
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object network TEST_VPN
host 192.168.250.10
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object-group service DM_INLINE_SERVICE_1
service-object gre
service-object esp
service-object udp destination eq isakmp
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Outside_access_in extended permit icmp any any
access-list Outside_access_in extended permit tcp any any object-group Puertos_Adm_Remota
access-list Outside_access_in extended permit tcp any any eq 4500
access-list Outside_access_in remark Para VPN ADMIN
access-list Outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list Outside_access_in extended permit udp any any object-group DM_INLINE_UDP_1
access-list Outside_access_in extended permit ah any any
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Outside_access_in extended permit ip any object TEST_VPN
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Inside_access_in extended permit ip host 192.168.250.10 any
access-list Inside_access_in extended permit udp host 192.168.250.10 eq 4500 any eq 4500
access-list Inside_access_in extended permit udp host 192.168.250.10 eq isakmp any eq isakmp
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object network TEST_VPN
host 192.168.250.10
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
nat (any,Outside) after-auto source dynamic any interface dns
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
route Outside 0.0.0.0 0.0.0.0 190.11.254.1 1
route Inside 10.10.10.0 255.255.255.0 192.168.250.10 1
route Inside 10.172.10.0 255.255.255.0 192.168.250.10 1
route Inside 10.252.213.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.214.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.215.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.216.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.220.0 255.255.255.0 192.168.250.2 1
timeout xlate 3:00:00
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect ipsec-pass-thru
class class-default
user-statistics accounting
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!End!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!VPN Concentrator
!!!Router 1841
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
version 12.4
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
aaa new-model
!
!
aaa authentication login ciscocp_vpn_xauth_ml_1 local
aaa authorization network ciscocp_vpn_group_ml_1 local
!
aaa session-id common
ip cef
!
!
!
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
crypto isakmp key ******** address 186.66.130.210
!
crypto isakmp client configuration group Users_VPN_New_Dta
key *********
dns 190.108.64.2
domain new-access.net
pool SDM_POOL_1
acl 108
max-users 50
!
!
crypto ipsec transform-set SDM_TRANSFORMSET_1 esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-SHA1 esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-md5-hmac
!
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set ESP-3DES-SHA
!
!
crypto map Policy1 client authentication list ciscocp_vpn_xauth_ml_1
crypto map Policy1 isakmp authorization list ciscocp_vpn_group_ml_1
crypto map Policy1 client configuration address respond
crypto map Policy1 1 ipsec-isakmp
description Tunnel to186.66.130.210
set peer 186.66.130.210
set transform-set ESP-3DES-SHA
match address 100
reverse-route
crypto map Policy1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
!
!
!
interface Loopback0
ip address 10.172.10.5 255.255.255.0
!
interface FastEthernet0/0
ip address 192.168.250.10 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
no ip route-cache cef
no ip route-cache
speed 100
full-duplex
crypto map Policy1
!
interface FastEthernet0/1
ip address 192.168.0.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
no ip route-cache cef
no ip route-cache
duplex auto
speed auto
no mop enabled
!
interface FastEthernet0/1.1
encapsulation dot1Q 30
ip address 10.10.10.1 255.255.255.0
no ip route-cache
!
ip local pool SDM_POOL_1 192.168.241.1 192.168.241.50
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.250.1
!
!
ip http server
no ip http secure-server
!
access-list 100 remark CCP_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 10.172.10.0 0.0.0.255 10.7.0.0 0.0.255.255
access-list 108 permit ip 10.10.10.0 0.0.0.255 192.168.241.0 0.0.0.255
access-list 108 permit ip 10.172.10.0 0.0.0.255 192.168.241.0 0.0.0.255
access-list 108 permit ip 192.168.250.0 0.0.0.255 192.168.241.0 0.0.0.255
!
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!SW 3750 Side A
Building configuration...
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
version 15.0
no service pad
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
vtp mode off
ip routing
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
vlan 2
name CONEX_PRINCIPAL
!
vlan 100
name MANAGEMENT
!
vlan 101
name SERVERS
!
vlan 102
name SERVERS_PRIVATE
!
vlan 103
name SERVERS_PRIVATE_RK12
!
vlan 501
!
vlan 502
name VLAN_ASISTECOOPER
!
vlan 503
name VLAN_INT_SINOPEC
!
vlan 504
name MOVIX
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!interface GigabitEthernet1/0/1
interface GigabitEthernet1/0/46
description OUT_WAN_FW14DATA (Conex. GE0/2 de FW14DATA ASA5520)
switchport access vlan 2
switchport mode access
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!interface Vlan1
!
interface Vlan2
ip address 192.168.250.2 255.255.255.0
!
interface Vlan100
description MANAGEMENT
ip address 10.252.220.1 255.255.255.0
traffic-shape group 20 3000000 375000 375000 1000
!
interface Vlan101
description SERVERS
ip address 10.252.214.1 255.255.255.0
rate-limit output access-group 11 512000 96000 192000 conform-action transmit exceed-action drop
traffic-shape group 10 512000 64000 64000 1000
!
interface Vlan103
description SERVERS_PRIVATE_RK12
ip address 10.252.216.1 255.255.255.0
!
interface Vlan501
description 501
ip address 10.252.215.1 255.255.255.240
!
interface Vlan502
description ASISTECOOPER
ip address 10.252.215.17 255.255.255.248
!
interface Vlan503
description SINOPEC_INTERNET
ip address 10.252.215.25 255.255.255.248
!
interface Vlan504
description MOVIX
ip address 10.252.215.33 255.255.255.248
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
ip route 0.0.0.0 0.0.0.0 192.168.250.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!Firewall Side B
ASA Version 8.2(5)
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
!
interface Ethernet0/0
nameif Outside
security-level 0
ip address 186.66.130.210 255.255.255.248
!
interface Ethernet0/1
description Salida de Internet
nameif Inside
security-level 100
ip address 10.7.0.1 255.255.255.240
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object-group network DM_INLINE_NETWORK_1
network-object 10.10.10.0 255.255.255.0
network-object 10.172.10.0 255.255.255.0
object-group network DM_INLINE_NETWORK_2
network-object 10.10.10.0 255.255.255.0
network-object 10.172.10.0 255.255.255.0
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Outside_1_cryptomap extended permit ip 10.7.0.0 255.255.0.0 10.1.0.0 255.255.0.0
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 10.1.0.0 255.255.0.0
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 10.5.0.0 255.255.0.0
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 10.2.0.0 255.255.0.0
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 object-group DM_INLINE_NETWORK_1
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 object-group DM_INLINE_NETWORK_2
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 10.172.10.0 255.255.255.0
access-list Outside_2_cryptomap extended permit ip 10.7.0.0 255.255.0.0 10.5.0.0 255.255.0.0
access-list Outside_3_cryptomap extended permit ip 10.7.0.0 255.255.0.0 10.2.0.0 255.255.0.0
access-list Outside_4_cryptomap extended permit ip 10.7.0.0 255.255.0.0 10.172.10.0 255.255.255.0
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
global (Outside) 101 interface
nat (Inside) 0 access-list Inside_nat0_outbound
nat (Inside) 101 0.0.0.0 0.0.0.0
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
route Outside 0.0.0.0 0.0.0.0 186.66.130.209 1
route Inside 10.7.1.0 255.255.255.0 10.7.0.2 1
route Inside 10.7.2.0 255.255.255.0 10.7.0.2 1
route Inside 10.7.3.0 255.255.255.0 10.7.0.2 1
route Inside 10.7.4.0 255.255.255.0 10.7.0.2 1
route Inside 10.7.10.0 255.255.255.0 10.7.0.4 1
route Inside 10.7.11.0 255.255.255.0 10.7.0.4 1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
crypto map Outside_map 4 match address Outside_4_cryptomap
crypto map Outside_map 4 set peer 190.11.254.250
crypto map Outside_map 4 set transform-set ESP-3DES-SHA
crypto map Outside_map 4 set security-association lifetime seconds 86400
crypto map Outside_map 4 set nat-t-disable
crypto map Outside_map 4 set reverse-route
crypto map Outside_map interface Outside
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
crypto isakmp enable Outside
crypto isakmp policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
tunnel-group 190.11.254.250 type ipsec-l2l
tunnel-group 190.11.254.250 ipsec-attributes
pre-shared-key *****
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
I appreciate very much your help in this issue. Thanks!!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2012 11:40 PM
This line should be UDP instead of TCP:
access-list Outside_access_in extended permit tcp any any eq 4500
Also, i don't see the static NAT configuration on your ASA.
Also, why is the crypto ACL to the loopback address? shouldn't it be to 10.252.0.0 instead of 10.172.0.0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2012 08:06 AM
Hello,
When edited teh display information i don´t care about put the NAT but is configured in the ASA (side A), i correct the UDP issue but cannot connect
The crypto ACL only include the loopback network and the side B major network, for test, you can see in both (router and ASA Side B) and is coherent. But still have the error message. It shows the error is only in Phase 2, but I don´t understand why?.
The Active/Active ASA in side A needs other config to passthrough the VPN site-to-site??
Why is the problem only in Phase 2, although the crypto map are similar (only consider loopback network-remote network escenario)
!!!!!FW_SideA (Context Admin)
ASA Version 8.4(2)
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
interface GigabitEthernet0/0
description Hacia el Internet (Conex. al GE0/2 de RTR14_CORE 2951)
nameif Outside
security-level 0
ip address 190.11.254.2 255.255.254.0 standby 190.11.254.3
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object network TEST_VPN
host 192.168.250.10
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object-group service DM_INLINE_SERVICE_1
service-object gre
service-object esp
service-object udp destination eq isakmp
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Outside_access_in extended permit icmp any any
access-list Outside_access_in extended permit tcp any any object-group Puertos_Adm_Remota
access-list Outside_access_in extended permit udp any any eq 4500
access-list Outside_access_in remark Para VPN ADMIN
access-list Outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any any
access-list Outside_access_in extended permit udp any any object-group DM_INLINE_UDP_1
access-list Outside_access_in extended permit ah any any
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Outside_access_in extended permit ip any object TEST_VPN
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
access-list Inside_access_in extended permit ip host 192.168.250.10 any
access-list Inside_access_in extended permit udp host 192.168.250.10 eq 4500 any eq 4500
access-list Inside_access_in extended permit udp host 192.168.250.10 eq isakmp any eq isakmp
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!
object network TEST_VPN
host 192.168.250.10
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
object network TEST_VPN
nat (any,any) static 190.11.254.250
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
nat (any,Outside) after-auto source dynamic any interface dns
access-group Outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
route Outside 0.0.0.0 0.0.0.0 190.11.254.1 1
route Inside 10.10.10.0 255.255.255.0 192.168.250.10 1
route Inside 10.172.10.0 255.255.255.0 192.168.250.10 1
route Inside 10.252.213.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.214.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.215.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.216.0 255.255.255.0 192.168.250.2 1
route Inside 10.252.220.0 255.255.255.0 192.168.250.2 1
timeout xlate 3:00:00
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect ipsec-pass-thru
class class-default
user-statistics accounting
!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!Edited!!!!!!!!!!!!!
This is the crypto ACL in router
access-list 100 remark CCP_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 10.172.10.0 0.0.0.255 10.7.0.0 0.0.255.255
....
crypto map Policy1 1 ipsec-isakmp
description Tunnel to186.66.130.210
set peer 186.66.130.210
set transform-set ESP-3DES-SHA
match address 100
reverse-route
This is the crypto ACL in ASA
access-list Inside_nat0_outbound extended permit ip 10.7.0.0 255.255.0.0 10.172.10.0 255.255.255.0
....
crypto map Outside_map 4 match address Outside_4_cryptomap
crypto map Outside_map 4 set peer 190.11.254.250
crypto map Outside_map 4 set transform-set ESP-3DES-SHA
crypto map Outside_map 4 set security-association lifetime seconds 86400
crypto map Outside_map 4 set nat-t-disable
crypto map Outside_map 4 set reverse-route
crypto map Outside_map interface Outside
Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2012 08:03 PM
You don't need to configure AH since your policy is only ESP, so pls remove the following:
access-list Outside_access_in extended permit ah any any
and add:
access-list Outside_access_in extended permit esp any any
Please kindly run debugs on the VPN to see where it's failing:
debug cry isa
debug cry ipsec
Also, share the output of:
show cry isa sa
show cry ipsec sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2012 08:04 PM
Ohh, and also remove the following:
crypto map Outside_map 4 set nat-t-disable
Are you trying to disallow NAT-T? if not, pls remove and see if it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2012 09:38 AM
Hello Jennifer,
I change the configs with all suggestions, but I cannot connect
I included all the VLANs from side A to generate interest traffic but don´t have any result.
I make many test. When ping the loopback in side A (10.172.10.5) from equipment in side B (10.7.0.4) appears this error when make "debug crypto isakmp" and "debug crypto ipsec" in ASA 5510.

I attached the "debug crypto isakmp" and "debug crypto ipsec" of the VPN concentrator in side A. And all configs. (check the info.zip)
I thanks very much your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2012 11:16 PM
Can you try to remove the following 2 commands on site B:
crypto map Outside_map 4 set nat-t-disable
crypto map Outside_map 4 set connection-type originate-only
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

