- Cisco Community
- Technology and Support
- Security
- VPN
- VPN ISR High Availability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN ISR High Availability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 07:49 AM
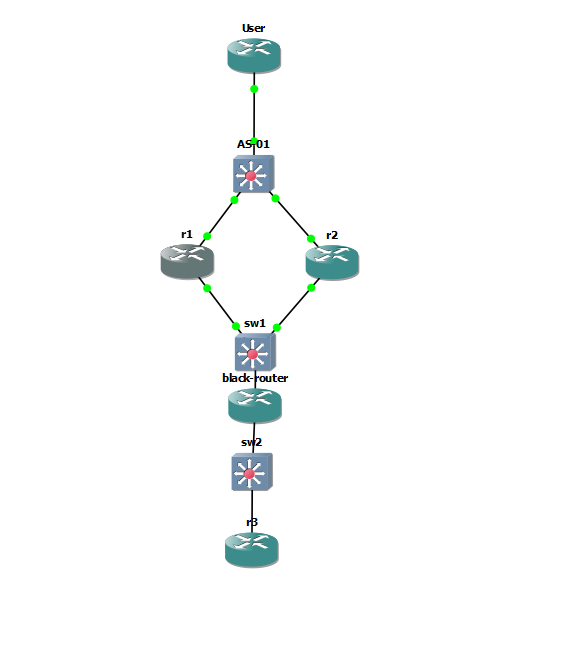
I have the following lab setup in GNS3. R1 & R2 are VPN endpoint at my datacenters and R3 is simulating a remote site. What i'm trying to accomplish is having one tunnel from R3 to the datacenter that leverages both R1 & R2 using HSRP and stateful failover. The configurations I'm attaching work, however the failover time is slow (30 sec+) and also fails when normalizing the solution. Would there be some timers I can adjust or perhaps leverage something else to speed up this process? Or would it just be best to scrap the HSRP solution and use two tunnels and let OSPF failover?
R1:
!
hostname r1
!
ipc zone default
association 1
no shutdown
protocol sctp
local-port 5000
local-ip 172.16.1.2
remote-port 5000
remote-ip 172.16.1.3
!
redundancy inter-device
scheme standby HA-Out
security ipsec TUNNEL-PROFILE-SITE
!
redundancy
!
crypto ikev2 proposal IKEv2-PROPOSAL
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy IKEv2-POLICY
match fvrf any
proposal IKEv2-PROPOSAL
!
crypto ikev2 keyring IKEv2-KEYRING
peer TO-SITE
address 172.16.2.1
pre-shared-key cisco123
!
!
crypto ikev2 profile IKEv2-PROFILE-SITE
match identity remote any
authentication local pre-share
authentication remote pre-share
keyring local IKEv2-KEYRING
!
crypto ipsec transform-set MYSET esp-gcm 256
mode tunnel
!
crypto ipsec profile TUNNEL-PROFILE-SITE
set transform-set MYSET
set ikev2-profile IKEv2-PROFILE-SITE
redundancy HA-Out stateful
!
interface Loopback0
ip address 10.1.1.1 255.255.255.255
!
interface Tunnel208
description <== Datacenter Connection to SITE ==>
ip unnumbered Loopback0
tunnel source 172.16.1.1
tunnel mode ipsec ipv4
tunnel destination 172.16.2.1
tunnel protection ipsec profile TUNNEL-PROFILE-SITE
!
interface GigabitEthernet0/0
ip address 172.16.1.2 255.255.255.240
standby 1 ip 172.16.1.1
standby 1 priority 110
standby 1 preempt
standby 1 name HA-Out
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 10.1.200.2 255.255.255.0
standby 0 name HA-In
standby 1 ip 10.1.200.1
standby 1 priority 110
standby 1 preempt
duplex auto
speed auto
media-type rj45
!
router ospf 1
passive-interface default
no passive-interface Tunnel208
network 10.1.1.1 0.0.0.0 area 0
network 10.1.200.0 0.0.0.255 area 0
network 10.254.2.32 0.0.0.3 area 0
!
ip route 0.0.0.0 0.0.0.0 172.16.1.10
!
!
hostname r2
!
ipc zone default
association 1
no shutdown
protocol sctp
local-port 5000
local-ip 172.16.1.3
remote-port 5000
remote-ip 172.16.1.2
!
redundancy inter-device
scheme standby HA-Out
security ipsec TUNNEL-PROFILE-SITE
!
redundancy
!
crypto ikev2 proposal IKEv2-PROPOSAL
encryption aes-gcm-256
prf sha384
group 20
!
crypto ikev2 policy IKEv2-POLICY
match fvrf any
proposal IKEv2-PROPOSAL
!
crypto ikev2 keyring IKEv2-KEYRING
peer TO-SITE
address 172.16.2.1
pre-shared-key cisco123
!
!
crypto ikev2 profile IKEv2-PROFILE-SITE
match identity remote any
authentication local pre-share
authentication remote pre-share
keyring local IKEv2-KEYRING
!
crypto ipsec transform-set MYSET esp-gcm 256
mode tunnel
!
crypto ipsec profile TUNNEL-PROFILE-SITE
set transform-set MYSET
set ikev2-profile IKEv2-PROFILE-SITE
redundancy HA-Out stateful
!
interface Loopback0
ip address 10.1.1.2 255.255.255.255
!
interface Tunnel208
description <== Datacenter Connection to SITE ==>
ip unnumbered Loopback0
tunnel source 172.16.1.1
tunnel mode ipsec ipv4
tunnel destination 172.16.2.1
tunnel protection ipsec profile TUNNEL-PROFILE-SITE
!
interface GigabitEthernet0/0
ip address 172.16.1.3 255.255.255.240
standby 1 ip 172.16.1.1
standby 1 priority 105
standby 1 name HA-Out
duplex auto
speed auto
media-type rj45
!
interface GigabitEthernet0/1
ip address 10.1.200.3 255.255.255.0
standby 0 name HA-In
standby 1 ip 10.1.200.1
standby 1 priority 105
duplex auto
speed auto
media-type rj45
!
router ospf 1
passive-interface default
no passive-interface Tunnel208
network 10.1.1.2 0.0.0.0 area 0
network 10.1.200.0 0.0.0.255 area 0
network 10.254.2.32 0.0.0.3 area 0
!
ip route 0.0.0.0 0.0.0.0 172.16.1.10
!
! hostname r3 ! crypto ikev2 proposal IKEv2-PROPOSAL encryption aes-gcm-256 prf sha384 group 20 ! crypto ikev2 policy IKEv2-POLICY match fvrf any proposal IKEv2-PROPOSAL ! crypto ikev2 keyring IKEv2-KEYRING peer TO-DC01 address 172.16.1.1 pre-shared-key cisco123 ! ! crypto ikev2 profile IKEv2-PROFILE-DC01 match identity remote any authentication local pre-share authentication remote pre-share keyring local IKEv2-KEYRING ! crypto ipsec transform-set MYSET esp-gcm 256 mode tunnel ! crypto ipsec profile TUNNEL-PROFILE-DC01 set transform-set MYSET set ikev2-profile IKEv2-PROFILE-DC01 ! interface Loopback0 ip address 10.10.1.1 255.255.255.255 ! interface Tunnel208 description <== Datacenter Connection ==> ip unnumbered Loopback0 tunnel source 172.16.2.1 tunnel mode ipsec ipv4 tunnel destination 172.16.1.1 tunnel protection ipsec profile TUNNEL-PROFILE-DC01 ! interface GigabitEthernet0/0 ip address 172.16.2.1 255.255.255.240 duplex auto speed auto media-type rj45 bfd template sample no cdp enable ! ! router ospf 1 passive-interface default no passive-interface Tunnel208 network 10.10.1.1 0.0.0.0 area 0 network 10.254.2.32 0.0.0.3 area 0 ! ip route 0.0.0.0 0.0.0.0 172.16.2.10 !
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 08:14 AM
I would not use HSRP, let the routing protocol determine failover, this should be quicker. You can use a metric to determine an Active router, upon failover you would automatically failover to the other tunnel. Alternatively you can run Active/Active over both tunnels.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 08:19 AM
Even through you could speed up the HSRP timer to make the failover faster, you still losing time (at least 1 packet lost) on tunnel formation during failover. And after you reduced the HSRP timer, the reliability will become another issue to think.
Building 2x active tunnels with both router, and determine the route using dynamic protocol is the best choice, in my opinion.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: