- Cisco Community
- Technology and Support
- Security
- VPN
- VPN Site-2-Site between Single ISP and Dual ISP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN Site-2-Site between Single ISP and Dual ISP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2012 07:13 AM
Hello community,
I'm looking for a smart way to achieve this configuration, the edge devices are both ASA 5520.
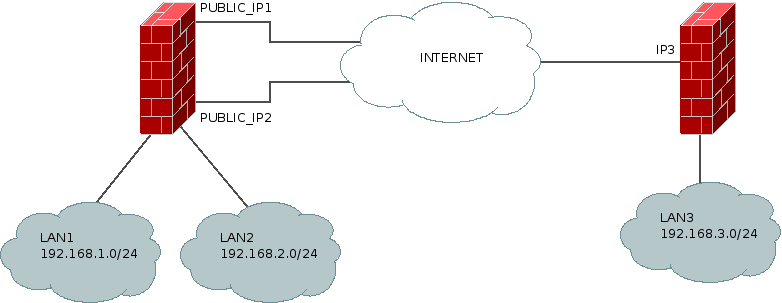
I would like to create 2 differents IPSEC tunnel:
- LAN1 <> LAN3 using PUBLIC_IP1
- LAN2 <> LAN3 using PUBLIC_IP2
The problem I have: the peer IP3 have only one IP, so it is the same peer address for the 2 differents. And, moreover, I don't know if is should be possible to use different route for a same peer...
Is anyone has an idea how to do it...?
Thanks a lot...
--
Erwan
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2012 08:34 AM
Sorry Erwan, but I don't think you will make it working.
You basically need two IP addressess on the LAN3 side. There is no policy based routing on ASA, so no way to achieve something like that.
There were people who were trying to do PBR through the NAT, but never heard of this magic really working for outgoing traffic. Especially from the box.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2012 09:00 AM
Hi,
Thanks for you answer... Effectively, there no PBR on ASA...
What I'm asking, the LAN3 is a public network (routed address), don't you think that it could be possible to establish a tunnel from IP1/IP2 to the IP of LAN3 affected on the "lan" port of the ASA ...?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2012 12:51 PM
Alright so the key is that 3.0 needs to be addressed differently by 1.0 than 2.0 and ASA with dual ISPs needs to have something that'll tell it how to route when PBR is not an option
Here's what I believe should get it working. I haven't had a chance to test it out and if you can lab/implement it please let us know the reasults
on FW with dual ISPs:
static (ISP1,inside) 192.168.4.0 192.168.3.0 netmask 255.255.255.0
static (ISP2,dmz) 192.168.5.0 192.168.3.0 netmask 255.255.255.0
The hosts behind this dual ISP FW will need to address the remote (3.0) subnet using the above ips (4.0 and 5.0)
i.e when 192.168.1.5 wants to ping to 192.168.3.15 it actually needs to ping 192.168.4.15
when 192.168.2.5 wants to ping to 192.168.3.15 it actually needs to ping 192.168.5.15
and above statics will handle the natting and switch 4.15 and 5.15 to 3.15 and send it over
Since we have static (ISP1,inside) and static (ISP2,dmz) traffic will be sent over correct ISP depending on which subnet (1.0 or 2.0) it originates from
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 12:07 AM
Yeah routing to 3.0 network you could do with NAT on >8.3. In configuration that you posted it is pre 8.3 and I am preety sure that traffic from 5.0 won't go to 3.0 through dmz since order of operations on ASA 8.2 is different (first route-lookup).
This part you could workaround with ASA > 8.3, but the biggest problem is that you would need to set up the same set peer IP3 in two crypto maps on two different interfaces. On ASA you can have only one route to one host, so there is no chance that ASA with two ISPs will go both links to IP3.
Regarding to Erwan statement - if the IP addresses inside are routable that it would be the best to create S2S tunnel with some other router inside the LAN - with ASA you won't achieve exactly what you want.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 01:07 AM
Thanks for your answers.
The main problem is the 2 differents tunnels with the same peer IP3.... There is no other router/firewall inside the LAN3.
Can you suggest me a device able to do what I'm looking for ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 01:59 AM
That's why it is NOT a good idea to terminate VPN on ASA with complex scenarios. ASA is not designed for this kind of thing.
Go with Cisco IOS. It can do exactly what you'r looking for either with DMVPN or GRE/IPSec with floating route. Either will work. You manipulate with routing metric.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 02:21 AM
Ok, I will take a look to Cisco IOS for next purchase...
BTW, David, I think we already met before . Are you working for the red square provider ...?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 02:28 AM
where is red square provider located, India? What does it do?
I live in Wash. DC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 02:32 AM
Hum ok, so it was a namesake... The David Tran I'm talking about is working in France .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 11:59 AM
Not true
Order of operation for destination nat is nat first and then route lookup
Whoever has access to asas, I would suggest labbing up my approach
I don't have access to Asas currently so I can't lab it
Sent from Cisco Technical Support iPhone App
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: