- Cisco Community
- Technology and Support
- Security
- VPN
- Re: VPN Site to Site and a site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 03:43 AM - edited 03-12-2019 04:53 AM
Dears,
let me explain a brief of my topology,
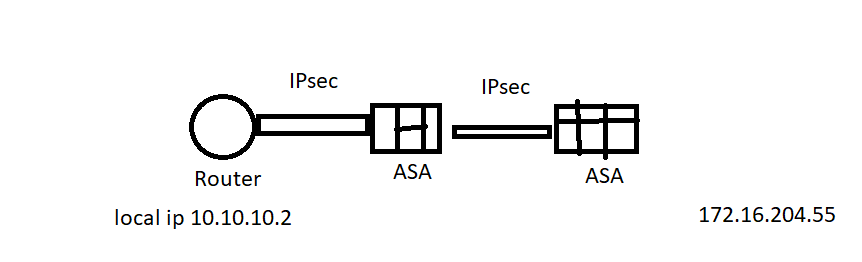
there is an active IP sec tunnel between the ROuter and ASA,
and there is another IPsec tunnel with the middle ASA and the right ASA,
my point is the local IP in the router 10.10.10.2 need to contact 172.16.204.55
what is the need configure need?
I added the IPs to each one.
as well what can I do to the middle ASA
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 03:52 AM
To sum it up you would need to do the following:
- add the corresponding destinations to the crypto acl for the end devices (router and asa)
- the go through asa will have the necessary source and destination added to the crypo acls
- route and nat in order to send the packets out the correct interface and with the correct IP
- the go through asa will have to accept and send packets coming in the same interface: same-security-traffic permit intra-interface
Here is a config guide:
HTH
Bogdan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 03:52 AM
To sum it up you would need to do the following:
- add the corresponding destinations to the crypto acl for the end devices (router and asa)
- the go through asa will have the necessary source and destination added to the crypo acls
- route and nat in order to send the packets out the correct interface and with the correct IP
- the go through asa will have to accept and send packets coming in the same interface: same-security-traffic permit intra-interface
Here is a config guide:
HTH
Bogdan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 04:11 AM
can I get more explain to the second one?
route it's needed?
also nat from to outside to outside interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 04:23 AM
I think it is easier to explain with examples so I will use the guide for reference:
- second point:
config that should be added
access-list VPN-to-Branch1 permit ip object-group Branch1-networks object-group Branch2-networks
access-list VPN-to-Branch2 permit ip object-group Branch2-networks object-group Branch1-networks
already existing config:
crypto map IPSec_VPN 1 match address VPN-to-Branch1
crypto map IPSec_VPN 2 match address VPN-to-Branch2
- routing:
you have to make sure that traffic is being sent out the outside interface, if you already have default routes those are fine
- nat from to outside to outside
you may need to configure nat from to outside to outside to avoid translating in public IP, if that is not the case the nat from to outside to outside config can be skiped
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: