- Cisco Community
- Technology and Support
- Security
- VPN
- Re: What is the best practice for DMVPN on ASA5500
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2010 08:40 AM - edited 02-21-2020 05:01 PM
Hi,
What is the best practice for DMVPN(IOS12.4) on ASA5510.
■Design 1
Placing dmvpn hub router behind ASA.
Q: In this case, does ASA have to configure NAT traversal, UDP encapsulation, and so on ?
■Design 2
Placing ASA behind dmvpn hub router.
Q: How are these addresses mapped ?
Q: Static NAT on DMVPN hub router ?

■Another design ...
Could you tell me the best practice and point of configuration.
Regards,
okumura
Solved! Go to Solution.
- Labels:
-
DMVPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2010 01:00 PM
For scenario 1) In the case where ASA is in front of DMVPN hub router following ports need to be allowed through:
UDP/500
UDP/4500
ESP/AH (IP proto 50/51) depending on configuration.
As should not be aware of any configuration of IPSec anywhere, so no NAT-traversal is needed.
Scenario 2) I would advise from creating NATing on DMVPN hub and move NATing towards ASA.
Note that both designs have it's flaws
Scenario 1) Traffic will have to go through ASA twice in each direction (post- or pre- encapsulation) which can cause significant and unnecessary load.
Scenario 2) Virtually all load is on the router, not clear private/public network boundry.
Design 1) Has major advantage because of added security and protection of the router traffic.
Why not adjust Design 1) To have DMZ hanging off DMVPN router or some other device behind ASA?
Here's a design we've discussed with Laurent a while back:
https://supportforums.cisco.com/servlet/JiveServlet/download/3185988-72419/Diagram1.jpeg
https://supportforums.cisco.com/message/3186744#3186744
Hope this helps,
Marcin
P.S.
For expert deisgn guideliness it's always best to contact your SE or AS team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2010 04:00 AM
Konichiwa Okumura-san (hope that's not rude :-))
This is the design I had in mind.

The switch in the middle is modeled on cat6k, but depending on traffic I'm pretty sure any L3 switch (3560 or similar) can do it.
Just remember that NAT is to be done on ASA, DMVPN termination on router.
Possibly some ACLs on L3 switch to police traffic.
The actual design implementaion - you need to take into account what would be majority of the traffic (between which portions of setup).
Devices to pick will depend on amount of traffic you're going to send.
In this case I'm assuming a more or less 50-50 spread between DMVPN and internet traffic.
In anyway I'd still run this design or any you pick by a Cisco SE or advanced service (if you have the contract).
Marcin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2010 01:00 PM
For scenario 1) In the case where ASA is in front of DMVPN hub router following ports need to be allowed through:
UDP/500
UDP/4500
ESP/AH (IP proto 50/51) depending on configuration.
As should not be aware of any configuration of IPSec anywhere, so no NAT-traversal is needed.
Scenario 2) I would advise from creating NATing on DMVPN hub and move NATing towards ASA.
Note that both designs have it's flaws
Scenario 1) Traffic will have to go through ASA twice in each direction (post- or pre- encapsulation) which can cause significant and unnecessary load.
Scenario 2) Virtually all load is on the router, not clear private/public network boundry.
Design 1) Has major advantage because of added security and protection of the router traffic.
Why not adjust Design 1) To have DMZ hanging off DMVPN router or some other device behind ASA?
Here's a design we've discussed with Laurent a while back:
https://supportforums.cisco.com/servlet/JiveServlet/download/3185988-72419/Diagram1.jpeg
https://supportforums.cisco.com/message/3186744#3186744
Hope this helps,
Marcin
P.S.
For expert deisgn guideliness it's always best to contact your SE or AS team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2010 01:46 AM
Hi, Marcin
Thank you for your reply.
I'v read your thread discussed with Laurent and thought that it is the best way for ASA and DMVPN-Hub-Router to have direct connectivity to internet.
But my site having ASA has only one physical connection to internet.
> Why not adjust Design 1) To have DMZ hanging off DMVPN router or some other device behind ASA?
Yes, I 'll try this.
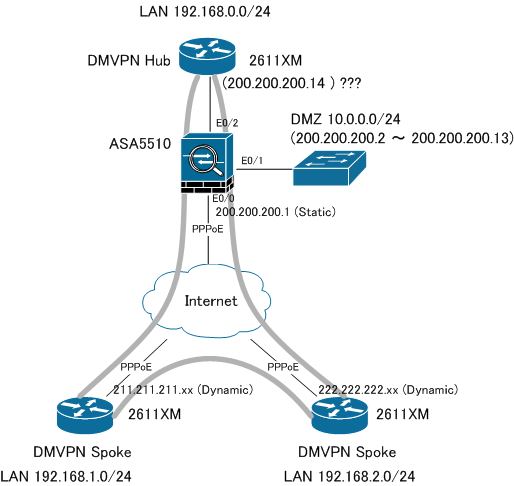
Do you mean like a following diagram?

If this is wrong, please point out the problems.
Regards,
okumura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2010 04:00 AM
Konichiwa Okumura-san (hope that's not rude :-))
This is the design I had in mind.

The switch in the middle is modeled on cat6k, but depending on traffic I'm pretty sure any L3 switch (3560 or similar) can do it.
Just remember that NAT is to be done on ASA, DMVPN termination on router.
Possibly some ACLs on L3 switch to police traffic.
The actual design implementaion - you need to take into account what would be majority of the traffic (between which portions of setup).
Devices to pick will depend on amount of traffic you're going to send.
In this case I'm assuming a more or less 50-50 spread between DMVPN and internet traffic.
In anyway I'd still run this design or any you pick by a Cisco SE or advanced service (if you have the contract).
Marcin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2010 04:13 PM
Hi, Marcin
Now I understand what you mean with your design.
I have an L3 switch (3550), so I'll try it and be back.
Thanks a lot for your help.
Best regards,
okumura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2010 04:42 PM
Hi, Marcin
I'm trying your design.
But before that, I must try another design which will contain basic element for your design.
That ISP does not provides IP16 but IP1, and client has no L3 switches.
Now I'll post a new thread, thank you.
Best Regards,
okumura
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: