- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect client to AnyConnect client conversations
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect client to AnyConnect client conversations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 09:26 AM
Scenario;
ASA5555x v 9.14.1 and ASA v 9.18.2
AnyConnect clients connect and ASA obtains client ip addresses from dhcp via inside interface on 10.173.96.0/19 network.
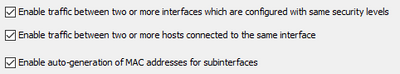
Clients are unable to establish connections between each other even though "same-security-traffic permit intra-interface" is enabled which used to function on older ASA5550 devices.... yeas ago.
I've been reading up other conversations and not quite reached a conclusion how to fix this, advice would be appreciated.
- Labels:
-
AnyConnect
-
IPSEC
-
Remote Access
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2022 03:39 AM
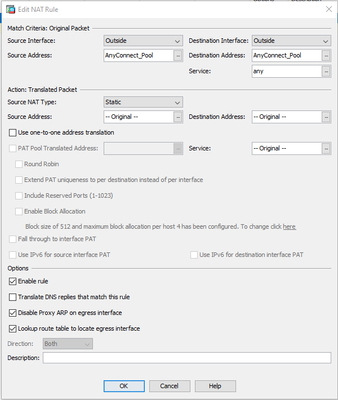
Realized that it's nat (Outside,Outside) configured, so it doesn't apply to inside->outside traffic and hence this statement is not correct: "BTW, with the below config AnyConnect users should not be able to ping inside router, because the router will also ARP for the AnyConnect client IP and ASA won't respond ("no-proxy-arp")". Everything else should be right.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2022 08:52 AM
Little bit of progress today after breaking things a bit.
I took out all of the configs and started afresh, testing as i went along.
My original statement that i gould ping the router gateway was incorrect.... i couldn't. However i could and can ping from the router gateway address to any client address ... the arp cache shows them all present. So this proves the issue isn't router or routing based. This is an ASR router acting as a local PE.
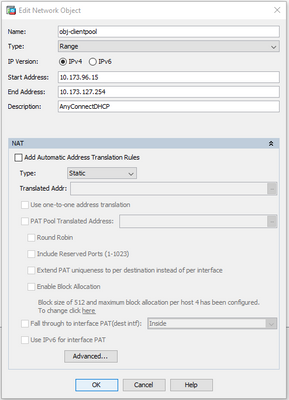
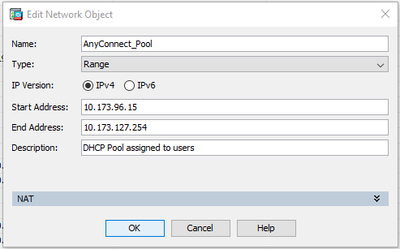
So then i added a network group and object from fresh using the dhcp pool that is assigned to clients via the inside interface.
The corresponding config is as follows;
object network obj-clientpool
network-object object obj-clientpool
range 10.173.96.15 10.173.127.254
object-group network AnyConnectClientPool
I can now ping the gateway and clients on another local ASA attached t the same subnet. This is my test ASA so i will have to wait till another client connects to test if this works between clients. It's a step in the right direction at least
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2022 08:57 AM
If this works i could actually add some advanced config to control what traffic can use it I guess as at the moment it is SIP traffic that is the challenge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2023 06:08 AM
So I've been working with TAC to find a solution, none of the discussion here resulted in a solution but obviously it's useful to show how we fixed it in the end.
1. Interface configuration
2. Network Object configuration for the DHCP range or internal pool
3. NAT configuration
4. Crypto configuration
crypto dynamic-map Outside_dyn_map 1 set reverse-route
* NOTE this will force any current connected vpns/clients to disconnect so you need to consider the timing and impact of the change
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide