- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect no login with AD credentials No internal net connection
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 11:51 AM
I am new to Cisco Firepower devices and trying to setup a Firepower 1140 with VPN and wanting to use our Windows AD server for login credentials with AnyConnect. It looks like the outside tunnel is setup I can reach the log in page getting a certificate error but when trying to log in with AD cred's I get a failed log in.
I have created the AD Server as an object and made it the Primary and secondary ID source same thing for DNS and using the Default Internal Cert. I have included some extra information bellow
2nd not as concerning I cannot access the user instruction page from the internal network so users can download pre-configured AnyConnect for the VPN connection
> show running-config tunnel-group
tunnel-group xx.xx.181.122 type ipsec-l2l
tunnel-group xx.xx.181.122 general-attributes
default-group-policy |s2sGP|xx.xx.181.122
tunnel-group xx.xx.181.122 ipsec-attributes
ikev2 remote-authentication pre-shared-key ****************************
ikev2 local-authentication pre-shared-key *******************************
tunnel-group Exxtr_VPN type remote-access
tunnel-group Exxtr_VPN general-attributes
address-pool VPN_Network
authentication-server-group Exxtr-SVR-01 LOCAL
secondary-authentication-server-group Exxtr-SVR-01 LOCAL
authorization-server-group Exxtr-SVR-01
tunnel-group Exxtr_VPN webvpn-attributes
group-alias Exxtr_VPN enable
>
>
> show running-config group-policy
group-policy DfltGrpPolicy attributes
banner value Welcome
banner value This portal is for authorized users only.
dns-server value 192.168.1.238
vpn-simultaneous-logins 3
vpn-session-timeout 550
vpn-tunnel-protocol ssl-client
webvpn
anyconnect ssl dtls none
anyconnect profiles value defaultClientProfile type user
group-policy |s2sGP|xx.xxx.181.122 internal
group-policy |s2sGP|xx.xxx.181.122 attributes
vpn-tunnel-protocol ikev2
>
>
>
> show running-config aaa-server
aaa-server Exxtr-SVR-01 protocol ldap
realm-id 3
aaa-server Exxtr-SVR (inside) host 192.168.1.238
server-port 389
ldap-base-dn CN=Users, CN=Builtin, DC=exxtr, DC=local
ldap-scope subtree
ldap-login-password ******************************************
ldap-login-dn XXXXXXXXXXXXXXXXXXXXXXX.com
server-type auto-detect
>
Solved! Go to Solution.
- Labels:
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 01:29 PM
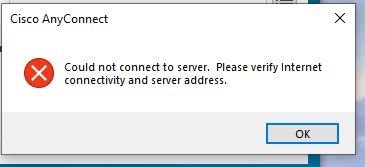
I'm using the Windows AD creds I normally sign in with that's what we are trying to achieve, the 192.168.168.xxx is the address schema I set up for VPN network that is my laptop trying to log in. I also have created an access rule from outside zone with vpn network to inside zone and inside network. From my phone using a WAN network I get to login page and cannot get passed that, on LAN when attempting to connect I get the picture bellow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 12:01 PM
@00u18jg7x27DHjRMh5d7 can you check the AD server logs to determine what the errors are? If you cannot see anything in the logs, run a packet capture to ensure communication from the FTD. Can you provide screenshots from FTD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 12:06 PM
I am getting these so an attempted connection is being made it looks like, I added the subnet to Sites and services and still cannot connect.
ET-SVR-01 5807 Warning NETLOGON System 12/16/2021 10:57:36 AM
10/20 10:48:22 [4580] Exxtr: NO_CLIENT_SITE: DESKTOP-SJ6RU80 192.168.168.129
10/20 10:53:39 [4580] Exxtr: NO_CLIENT_SITE: LT121720-CM 192.168.168.110
10/20 10:57:27 [12344] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:57:27 [4580] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:58:19 [4580] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:59:39 [4580] Exxtr: NO_CLIENT_SITE: LT121720-CM 192.168.168.110
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 12:34 PM - edited 12-16-2021 12:35 PM
@00u18jg7x27DHjRMh5d7 where are these logs from? The AD server? How do they relate to the FTD login events?
Look in the Windows event logs and see what the errors are.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 12:43 PM
5807 is from the Windows event logs its why I added the subnet in Sites and services that has stopped that error. But still cannot log in. When testing connection for the AD object created it passes connection test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 12:54 PM
The output below looks like authentications of computer/machine accounts from a unique IP address. What credentials are you using when trying to loging to the VPN?
10/20 10:48:22 [4580] Exxtr: NO_CLIENT_SITE: DESKTOP-SJ6RU80 192.168.168.129
10/20 10:53:39 [4580] Exxtr: NO_CLIENT_SITE: LT121720-CM 192.168.168.110
10/20 10:57:27 [12344] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:57:27 [4580] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:58:19 [4580] Exxtr: NO_CLIENT_SITE: LT122120-JS 192.168.168.114
10/20 10:59:39 [4580] Exxtr: NO_CLIENT_SITE: LT121720-CM 192.168.168.110
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2021 01:29 PM
I'm using the Windows AD creds I normally sign in with that's what we are trying to achieve, the 192.168.168.xxx is the address schema I set up for VPN network that is my laptop trying to log in. I also have created an access rule from outside zone with vpn network to inside zone and inside network. From my phone using a WAN network I get to login page and cannot get passed that, on LAN when attempting to connect I get the picture bellow.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide