- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect on Linux Apparently Not Trusting Imported Root CA's
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2019 07:28 PM - edited 02-21-2020 09:43 PM
Hi,
We are experiencing an issue whereby the Cisco AnyConnect Client, running on Linux (CentOS 7), is not trusting the imported System and Firefox Root CA’s when connecting to a VPN endpoint (ASA). Said VPN endpoint is using an self-signed certificate. The Root and Chain CA’s which signed the ASA's certificate are imported and therefore trusted in Firefox and in the Computer certificate store.
I'm looking for some help in configuring the AnyConnect client so it trusts the Firefox or Computer CA trust stores.
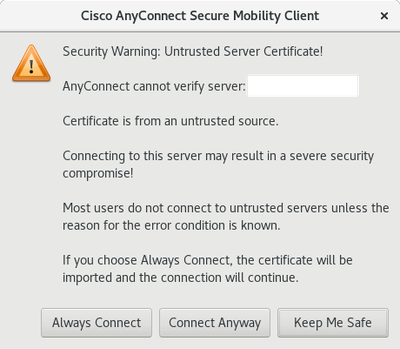
The error on attempting to connect:
If I accept, the connection succeeds.
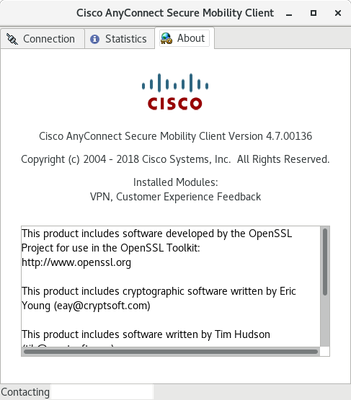
AnyConnect client version:
Proof the system trusts the VPN endpoint:
curl test:
[root@desktop anyconnect]# curl https://fw1.companyx.com
<html>
<script>
document.cookie = "tg=; expires=Thu, 01 Jan 1970 22:00:00 GMT; path=/; secure";
document.cookie = "sdesktop=; expires=Thu, 01 Jan 1970 22:00:00 GMT; path=/; secure";
document.location.replace("/+CSCOE+/logon.html");
</script>
</html>
openssl test:
[root@desktop anyconnect]# openssl s_client -connect fw1.companyx.com:443 CONNECTED(00000003) depth=2 C = AU, ST = New South Wales, L = Sydney, O = companyx, OU = IT Operations, CN = companyx Production CA - SHA256, emailAddress = camaster@companyx.com verify return:1 depth=1 C = AU, ST = New South Wales, L = Sydney, O = companyx, OU = IT Operations, CN = companyx Production - Chain1 CA - SHA256, emailAddress = camaster@companyx.com verify return:1 depth=0 C = AU, ST = NSW, L = Chatswood, O = companyx, OU = IT Operations, CN = fw1.companyx.com, emailAddress = comms@companyx.com verify return:1 --- Certificate chain 0 s:/C=AU/ST=NSW/L=Chatswood/O=companyx/OU=IT Operations/CN=fw1.companyx.com/emailAddress=comms@companyx.com i:/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production - Chain1 CA - SHA256/emailAddress=camaster@companyx.com 1 s:/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production - Chain1 CA - SHA256/emailAddress=camaster@companyx.com i:/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production CA - SHA256/emailAddress=camaster@companyx.com 2 s:/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production CA - SHA256/emailAddress=camaster@companyx.com i:/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production CA - SHA256/emailAddress=camaster@companyx.com --- Server certificate -----BEGIN CERTIFICATE----- <snip> -----END CERTIFICATE----- subject=/C=AU/ST=NSW/L=Chatswood/O=companyx/OU=IT Operations/CN=fw1.companyx.com/emailAddress=comms@companyx.com issuer=/C=AU/ST=New South Wales/L=Sydney/O=companyx/OU=IT Operations/CN=companyx Production - Chain1 CA - SHA256/emailAddress=camaster@companyx.com --- No client certificate CA names sent Server Temp Key: DH, 1024 bits --- SSL handshake has read 4641 bytes and written 487 bytes --- New, TLSv1/SSLv3, Cipher is DHE-RSA-AES256-SHA Server public key is 2048 bit Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1 Cipher : DHE-RSA-AES256-SHA Session-ID: 645ABA59B32B6579111E3D8769F4D18EBADA0A856B8391BF7E9BE54BDFACDAAC Session-ID-ctx: Master-Key: B2974FBF86C106D43914A3BD35A0F2961AF8665A3D24564F12CAB9E045E5FD397A0A209E3471DEE11F182BD7D9B2C5D0 Key-Arg : None Krb5 Principal: None PSK identity: None PSK identity hint: None Start Time: 1564632371 Timeout : 300 (sec) Verify return code: 0 (ok)
AnyConnect Client Config and Connection Details:
[root@desktop anyconnect]# cat profile/unixanyconnectprofile.xml <?xml version="1.0" encoding="UTF-8"?> <AnyConnectProfile xmlns="http://schemas.xmlsoap.org/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap.org/encoding/ AnyConnectProfile.xsd"> <ClientInitialization> <UseStartBeforeLogon UserControllable="false">false</UseStartBeforeLogon> <AutomaticCertSelection UserControllable="false">false</AutomaticCertSelection> <ShowPreConnectMessage>false</ShowPreConnectMessage> <CertificateStore>All</CertificateStore> <CertificateStoreOverride>false</CertificateStoreOverride> <ProxySettings>Native</ProxySettings> <AllowLocalProxyConnections>true</AllowLocalProxyConnections> <AuthenticationTimeout>12</AuthenticationTimeout> <AutoConnectOnStart UserControllable="false">false</AutoConnectOnStart> <MinimizeOnConnect UserControllable="false">true</MinimizeOnConnect> <LocalLanAccess UserControllable="false">false</LocalLanAccess> <DisableCaptivePortalDetection UserControllable="false">false</DisableCaptivePortalDetection> <ClearSmartcardPin UserControllable="false">true</ClearSmartcardPin> <IPProtocolSupport>IPv4</IPProtocolSupport> <AutoReconnect UserControllable="false">true <AutoReconnectBehavior UserControllable="false">ReconnectAfterResume</AutoReconnectBehavior> </AutoReconnect> <AutoUpdate UserControllable="false">false</AutoUpdate> <RSASecurIDIntegration UserControllable="false">Automatic</RSASecurIDIntegration> <WindowsLogonEnforcement>SingleLocalLogon</WindowsLogonEnforcement> <WindowsVPNEstablishment>LocalUsersOnly</WindowsVPNEstablishment> <AutomaticVPNPolicy>false</AutomaticVPNPolicy> <PPPExclusion UserControllable="false">Disable <PPPExclusionServerIP UserControllable="false"></PPPExclusionServerIP> </PPPExclusion> <EnableScripting UserControllable="false">false</EnableScripting> <EnableAutomaticServerSelection UserControllable="false">false <AutoServerSelectionImprovement>20</AutoServerSelectionImprovement> <AutoServerSelectionSuspendTime>4</AutoServerSelectionSuspendTime> </EnableAutomaticServerSelection> <RetainVpnOnLogoff>false </RetainVpnOnLogoff> <AllowManualHostInput>true</AllowManualHostInput> </ClientInitialization> <ServerList> <HostEntry> <HostName>fw1.companyx.com</HostName> <HostAddress>fw1.companyx.com</HostAddress> <PrimaryProtocol>IPsec <StandardAuthenticationOnly>false</StandardAuthenticationOnly> </PrimaryProtocol> </HostEntry> </ServerList> </AnyConnectProfile>
[root@desktop anyconnect]# cat AnyConnectLocalPolicy.xml <?xml version="1.0" encoding="UTF-8"?> <!--ANSIBLE CONTROLLED--> <AnyConnectLocalPolicy xmlns="http://schemas.xmlsoap.org/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap.org/encoding/ AnyConnectLocalPolicy.xsd" acversion="4.7.00136"> <!--with BypassDownloader enabled there are some sort of SSL/TLS handshake errors which prevent the client and concentrator connecting. since we are not relying on the download we will disable it--> <BypassDownloader>true</BypassDownloader> <ExcludeFirefoxNSSCertStore>true</ExcludeFirefoxNSSCertStore> <ExcludeMacNativeCertStore>false</ExcludeMacNativeCertStore> <ExcludePemFileCertStore>false</ExcludePemFileCertStore> <ExcludeWinNativeCertStore>false</ExcludeWinNativeCertStore> <FipsMode>true</FipsMode> <RestrictPreferenceCaching>false</RestrictPreferenceCaching> <RestrictTunnelProtocols>false</RestrictTunnelProtocols> <RestrictWebLaunch>false</RestrictWebLaunch> <StrictCertificateTrust>false</StrictCertificateTrust> <UpdatePolicy> <AllowComplianceModuleUpdatesFromAnyServer>true</AllowComplianceModuleUpdatesFromAnyServer> <AllowISEProfileUpdatesFromAnyServer>true</AllowISEProfileUpdatesFromAnyServer> <AllowManagementVPNProfileUpdatesFromAnyServer>true</AllowManagementVPNProfileUpdatesFromAnyServer> <AllowServiceProfileUpdatesFromAnyServer>true</AllowServiceProfileUpdatesFromAnyServer> <AllowSoftwareUpdatesFromAnyServer>true</AllowSoftwareUpdatesFromAnyServer> <AllowVPNProfileUpdatesFromAnyServer>true</AllowVPNProfileUpdatesFromAnyServer></UpdatePolicy> </AnyConnectLocalPolicy>
Certs are trusted by the System:
[root@desktop anyconnect]# ls -ltra /etc/pki/ca-trust/source/anchors/ total 12 drwxr-xr-x. 4 root root 80 Jul 30 18:09 .. -rw-r--r--. 1 root root 1830 Jul 31 07:40 companyx_prod_ca_top_sha256_2016-2037.pem -rw-r--r--. 1 root root 1964 Jul 31 07:40 companyx_prod_ca_chain1_crld_sha256_2017-2027.pem -rw-r--r--. 1 root root 1830 Jul 31 07:40 companyx_prod_ca_chain1_sha256_2016-2027.pem drwxr-xr-x. 2 root root 161 Jul 31 07:40 .
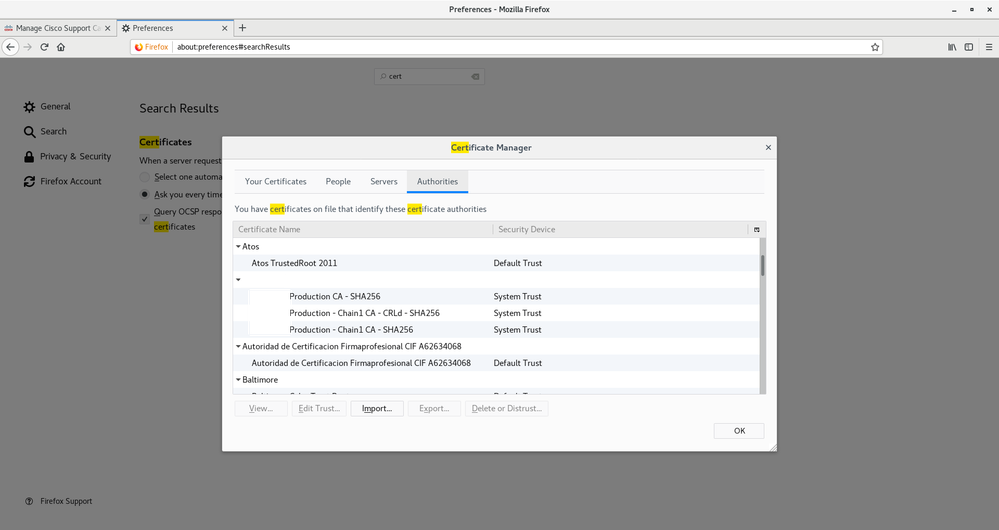
Certs are trusted by Firefox:
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2019 02:17 PM
I found out the following:
On a Linux machine, the Anyconnect client validates certificates by:
- The client validates it against the Mozilla certificate store if the user has a valid Firefox profile.
- If the client is unable to validate the certificate based on the Mozilla certificate store or if a firefox profile isn't associated with that user, it validates the certificate against the PEM certificate store.
The machine CA PEM stores are located at the following path: /opt/.cisco/certificates/ca/
I resolved my issue by placing my trusted certs in the path above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2019 05:53 PM
bump?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2019 02:17 PM
I found out the following:
On a Linux machine, the Anyconnect client validates certificates by:
- The client validates it against the Mozilla certificate store if the user has a valid Firefox profile.
- If the client is unable to validate the certificate based on the Mozilla certificate store or if a firefox profile isn't associated with that user, it validates the certificate against the PEM certificate store.
The machine CA PEM stores are located at the following path: /opt/.cisco/certificates/ca/
I resolved my issue by placing my trusted certs in the path above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2024 12:10 PM - edited 02-20-2024 11:31 AM
Tried to place my trusted root certificate in /opt/.cisco/certificates/ca & $USER_HOME/.cisco/certificates/ca but AnyConnect/SecureClient still gives the following error:
csc_webhelper[83801]: Function: webViewLoadFailedWithTLSErrorsCB File: ../../../vpn/WebHelper/Linux/GtkBrowserWindow.cpp Line: 101 Failed to load page: The signing certificate authority is not known. (https://vpn.company.com/+CSCOE+/saml/sp/login?ctx=221416110%0A&acsamlcap=v2)
Edit: I just found that the above error can be fixed by installing root certificate to /usr/local/share/ca-certificates and re-run 'sudo update-ca-certificates.' It turns out that the default certificate storage used by acwebhelper actually points to the system certificate storage(/etc/ssl/certs) rather than ~/.cisco/certificates/ca(which is the default used by vpn/vpnui). It would be great if Cisco could add ~/.cisco/ceritifcates/ca or /opt/.cisco/certificates to acwebhelper in their future release such that we can have a consistent view of CA certificate storage across all the VPN binaries(acwebhelper, vpn, vpnui, ...).
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: