- Cisco Community
- Technology and Support
- Security
- VPN
- Anyconnect SSL RA VPN Dual Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 07:32 AM - edited 01-30-2021 07:34 AM
Hi Experts
We've ASA Anyconnect Remote access SSL Dual Authentication managed through the Radius server- ISE.
When they connect, client will be validating the identity cert of the firewall (Server Authentication) and in return firewall validates the client user/machine certs (Client Authentication)
Once validated, they'll be entering their credentials, they'll be hitting the Default WebVPN tunnel group. And, firewall will pass their credentials to the Radius Server ISE which will push the Group-policy based on AD groups configured.
1. Is it understanding is correct or am i missing something in the traffic flow ?
2. If yes, how do we know if ASA is looking for the User cert or the Machine cert on the end-users?
Please assist.
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 07:43 AM
They'll hit the tunnel group specified either via the group URL or from the drop-down list. RADIUS can push the group policy settings if configured, it's not a requirement.
You can modify the AnyConnect XML profile, to either check user, machine or all certificate store. Default is "all".
Or you can edit the XML profile manually by changing the following values:-
<CertificateStore>All</CertificateStore>
<CertificateStore>User</CertificateStore>
<CertificateStore>Machine</CertificateStore>
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 07:43 AM
They'll hit the tunnel group specified either via the group URL or from the drop-down list. RADIUS can push the group policy settings if configured, it's not a requirement.
You can modify the AnyConnect XML profile, to either check user, machine or all certificate store. Default is "all".
Or you can edit the XML profile manually by changing the following values:-
<CertificateStore>All</CertificateStore>
<CertificateStore>User</CertificateStore>
<CertificateStore>Machine</CertificateStore>
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 07:53 AM - edited 01-30-2021 07:57 AM
Hi @Rob Ingram,
Thanks for the reply. Can you please assist on the below
If we do client authentication, do we need to add the Root CA of the User/Machine cert into the trusted certs on the firewall and change the tunnel-group authentication to certificate or certificate & password, as required.
1. Is it correct or any other config is required?
2. If managed thro' Radius server, under the Tunnel-group on ASA firewall if we configure username-from-certificate as the CN, will the firewall pass it to the ISE or ISE will look for the username based on AD?
And, typically, browsers will be loaded with the public CA cert to validate the identity of the URL for any HTTPS traffic. (server authentication).
3.So, when connecting to SSL RA VPN, which browser does the Anyconnect will look into to verify the Trusted CA certs list of public PKI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:01 AM
Yes, the ASA must have the root certificate used by the clients for authentication to succeed.
Yes the username will be passed to ISE, which can be used to perform authorization.
If you are using AnyConnect then the web browser certificate store won't be in use, the computers' certificate store (user/machine) will be used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:08 AM
Hi @Rob Ingram
Thanks for the assistance.
With regards to the Root CA certs (server Authentication), Anyconnect will look for the computers certificate store (user/machine). Where does the Anyconnect will look into when validating the identity cert of the firewall (Public PKI)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:13 AM
The client will check the "Trusted Root Certificate Authorities" in the local computer store.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:10 AM
2. If yes, how do we know if ASA is looking for the User cert or the Machine cert on the end-users?
-You have the ability to perform certificate matching which you can configure in your AnyConnect xml profile that will tell AnyConnect to automatically match/map to a user/comp certificate. Then in your connection profile (tunnel-group) you can extract something such as the UserPrincipalName (UPN) from the identity cert of the client that then gets passed to ISE for authorization and mapping against AD.
This is a pretty good overview tutorial that may help:SSL VPN Certificate-Based Authentication with AnyConnect
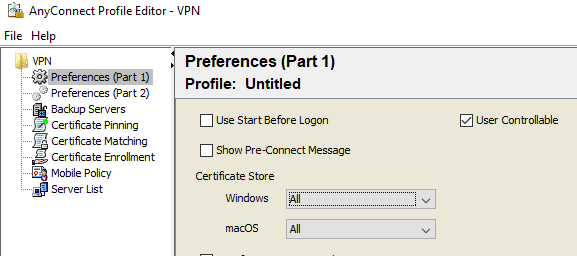
For the certificate matching configuration in the XML profile see the 'Certificate Matching' Section below Preferences part1/2. HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:17 AM - edited 01-30-2021 08:24 AM
Thanks for the assistance, so far. Final one on this thread. Please assist
I've just noticed the Backup Server and Server List on the Anyconnect XML profile.
1. what is the purpose of these?
2. Which one is used for the Backup/Secondary firewall VPN connection, if the primary goes down?
3. And how will the users be routed to the secondary firewall? Is it done automatically or how it works?
4.If Cert UPN is used for the username validation against the ISE AuthZ policies, when users enter the username/Password, what it does? Just a credential validation against the Identity Store sequence on ISE?
Cheers,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:23 AM - edited 01-30-2021 08:24 AM
No they are different.
Server List > Backup Servers, is a backup for that server list entry only. You can have multiple server lists, with unique primary and backup servers.
Backups Servers is global for all server lists.
When the primary fails, anyconnect will check the list and attempt to make a connection to the address on the backup list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:35 AM
4.If Cert UPN is used for the username validation against the ISE AuthZ policies, when users enter the username/Password, what it does? Just a credential validation against the Identity Store sequence on ISE?
-In that scenario inside your tunnel-group configuration you would configure it to certificate only, and under authorization tab under advanced you would configure the extraction of the unique field you wish to use to map/authorize the client/user via ISE/AD. Essentially in this scenario the user when connecting would not get prompted for username/pass. Good luck & HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2021 08:44 AM
Thanks for the reply mate. Yeah, you're right when we configured authentication certificate
But Under Tunnel-group, We've configured authentication aaa certificate. If the username is extracted from the Cert and forwarded to ISE for the AuthZ policies and AD group validation, when users enter the username/Password, what it does? Just a credential validation against the Identity Store sequence on ISE?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide