- Cisco Community
- Technology and Support
- Security
- VPN
- anyconnect SSL VPN with SAML SSO: Failed to consume SAML assertion
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 03:05 AM - edited 12-05-2022 03:40 AM
Hi,
I have asa 5506-x and I configureted VPN with Azure SSO in my network but I have problem with that.
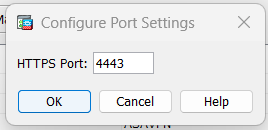
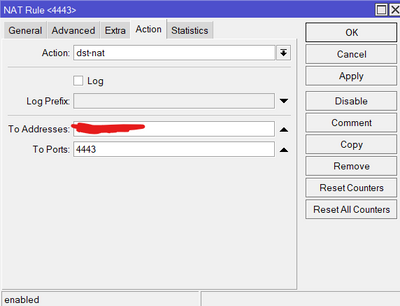
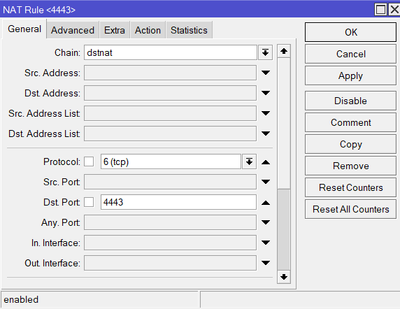
Between public IP address and ASA I have gateway ( mikrotik ) so I had to configure forwarding. To do this i changed ssl port on ASA to 4443 from 443.
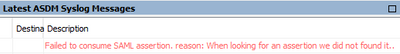
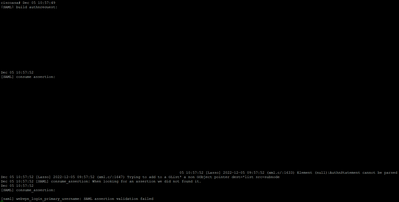
When I chose login, I get communicat from ASA's syslog:
From devops tools when I try to login to web anyconnect:
Failed to generate SAML AuthnReque
status code http 303
Debug webvpn saml 255 :
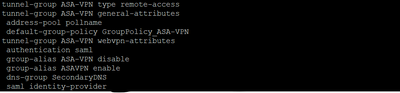
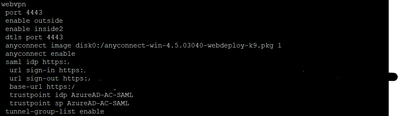
All configuration I prepared with instruction:
Anyone can help me where is the problem ?
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2022 10:59 AM
I did find solution. I had to upgrade software.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 11:08 AM
Hi @lukaszhar,
Given that you've changed your HTTP port from default 443, to non-standard 4443, you need to change that everywhere where your ASA FQDN is appearing:
- I believe your base-url under webvpn should remain without additional port (if still not working you can try modifying tis part too)
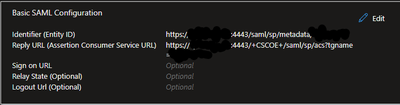
- I believe you'll need to modify Reply URL (Assertion Consumer Service URL) on Azure App to something like https://vpn.domain.com:4443/+CSCOE+/saml/sp/acs?tgname=TG_NAME, where you'll need to include your non-standard port. Otherwise, Azure is still sending SAML assertion to default HTTPS port, and it never reaches to your ASA.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 11:12 PM
Yes, I did this in this way.
Responce is coming to ASA because i did forwarding from 443 to 4443. So if ID provider send responce to 443 my gateway forward it to 4443. In my opinion. Am I wrong ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 11:22 PM
I believe Entity ID will have to be without 4443. This connection is initiated by ASA, and will originate from base-url, and it represents on how Azure sees incoming requests from ASA.
For Reply URL, yes, this is what I had in mind. Given that ASAs Web port is now 4443, it expects traffic to come on 4443. However, I'm not sure that I fully understand what you did ith port forwarding. I assumed you've just forwarded port 4443 from your Mtik to ASA? Azure needs to forward packet to 4443, and ASA needs to see that packet comming on 4443, so no room for standard 443 anymore.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 11:45 PM
i check it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 03:30 AM
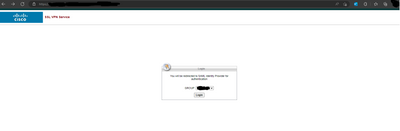
I got this effect:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2022 05:09 AM
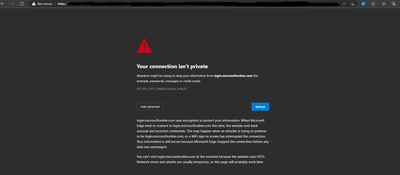
Given that there are multiple redirections with SSO, I can't really know for what service exactly you are getting this warning. You need to understand that based on FQDN inside URL, as well as from offered certificate.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022 02:00 AM
I repaired it and now i have the same problem and errors like before change port. could port forwarding be a problem ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2022 03:25 AM
Certificate errors don't usually have dependency from port, so I would doublt that port itself would be a root cause. However, as stated before, there are multiple redirections involved, so you'll need to understand for which FQDN/URL you are getting certificate warning (for login to ASA, for login to Azure, for redirection from Azure to ASA). From there on, you can proceed further with troubleshooting.
Kind regards,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2022 10:59 AM
I did find solution. I had to upgrade software.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide