- Cisco Community
- Technology and Support
- Security
- VPN
- Re: AnyConnect Using ISE does not get IP address
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 11:52 PM
WE have been using AnyConnect for 3rd party access to our network for some time, using local auth on the ASA, and IP addressing coming from local pools, and split tunnel ACL to control access, so when 3rd party connect they get the drop down box to select the correct group.
We moved the authentication to the AD server via ISE, now ISE works ok authenticates and downloads the DACL for the correct group
The next step is to remove the " tunnel-group-list enable" from webvpn We followed the video and configured the ASA
as below
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 ikev2 ssl-clientless l2tp-ipsec ssl-client
exit
tunnel-group DefaultWEBVPNGroup general-attributes
authentication-server-group ISE
But now we get the message when trying to connect that there was no Ip address, and disconnects.
I understand the way it should work is once the anyconnect authentication reaches the ISE, the user is linked to a specific group, which then tells the ASA to use that group for IP addressing etc.
anybody help with this
efault
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 08:10 AM
Hi,
Your Group Policy does not reference a VPN Pool, but the tunnel-group does. I've tested the following configuration inconjuction with the ISE configuration in a previous message. User connects to the Default Tunnel Group (no drop down list to select profile), ISE authenticates and authorizes the session, either the GP-1 or GP-2 group-policy is successfully assigned to the users' session, depending on AD group membership. The VPN pool is reference in the group-policy
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ssl-client
group-policy GP-1 attributes
dns-server value 192.168.10.5 192.168.10.6
vpn-tunnel-protocol ssl-client
address-pools value POOL_1
group-policy GP-2 attributes
dns-server value 192.168.10.5
vpn-tunnel-protocol ssl-client
address-pools value POOL_2
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 12:07 AM
We need to look how your DHCP IP handover configured.
look some example :
https://www.petenetlive.com/KB/Article/0001155
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 12:52 AM
BB
We are not using DHCP, but local pools on the ASA.
and the example in the link you supplied uses local pools
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 04:45 AM
I can interpret your last sentence in different ways "the user is linked to a specific group, which then tells the ASA to use that group for IP addressing etc."
When you say groups are you referring to an ASA tunnel-group or are you referring to AD groups?
All users connect on the Default tunnel-group and are you then attempting to send a different tunnel-group to the user session via authorization, is that correct? Or will all users remain on the Default tunnel-group and use the same VPN Pool?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 06:07 AM
Thanks for your response
When you say groups are you referring to an ASA tunnel-group or are you referring to AD groups? << ASA groups
All users connect on the Default tunnel-group and are you then attempting to send a different tunnel-group to the user session via authorization, is that correct? <<<< Yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 06:49 AM
Sorry, I meant to say group-policy not tunnel-group.
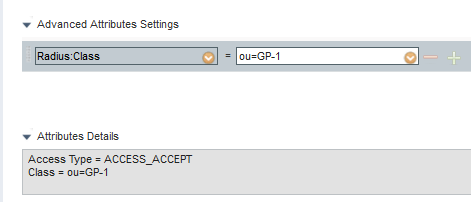
Do you have a authorization profile configured with "Advanced Attribute Settings" -> Class = ou=<GROUP-POLICY-NAME>? Where <GROUP-POLICY-NAME> is the group-policy name configured on the ASA? As long as the group-policy referenced correctly has the address-pool defined that should work.
E.g:-
group-policy GP-1 attributes
address-pools value VPN_POOL
ip local pool VPN_POOL 192.168.14.10-192.168.14.254 mask 255.255.255.0
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 03:28 PM
Hi RJI,
That is the problem we have it is etup as you say. but it still says no assigned address when trying to connect
Does the 'Tunnel-group' and the 'Group-policy' name have to be the same? in the examples I have seen they are.
that is the next thing to try at the moment the names are different.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 03:50 PM
We tried the Tunnel-group and Group-policy name the same but still get the same problem.
remember when we allow the user to select profile at login page it is ok
it is only when we dont allow this.
Note we use ISE 2.3 and the contractor who looks after it has tested on another ASA and is ok.
please find below the relevant ASA config
tunnel-group innotech type remote-access
tunnel-group innotech general-attributes
address-pool innotech_vpn
authentication-server-group ISE
authentication-server-group (inside) ISE
default-group-policy innotech
tunnel-group innotech webvpn-attributes
group-alias innotech enable
group-policy innotech internal
group-policy innotech attributes
wins-server none
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_innotech
default-domain value healthecare.net
webvpn
anyconnect ssl keepalive 300
anyconnect dpd-interval client 120
anyconnect dpd-interval gateway 120
group-policy DfltGrpPolicy internal
group-policy DfltGrpPolicy attributes
banner none
wins-server none
dns-server none
dhcp-network-scope none
vpn-access-hours none
vpn-simultaneous-logins 3
vpn-idle-timeout 30
vpn-idle-timeout alert-interval 1
vpn-session-timeout none
vpn-session-timeout alert-interval 1
vpn-filter none
vpn-tunnel-protocol ikev1 ssl-client
ip-comp disable
group-lock none
pfs disable
split-tunnel-policy tunnelall
ipv6-split-tunnel-policy tunnelall
split-tunnel-network-list none
default-domain value healthecare.net
split-dns none
split-tunnel-all-dns disable
client-bypass-protocol disable
gateway-fqdn none
msie-proxy server none
msie-proxy method no-modify
msie-proxy except-list none
msie-proxy local-bypass disable
msie-proxy pac-url none
msie-proxy lockdown enable
address-pools none
ipv6-address-pools none
smartcard-removal-disconnect enable
security-group-tag none
periodic-authentication certificate none
webvpn
homepage none
anyconnect ssl dtls enable
anyconnect mtu 1406
anyconnect firewall-rule client-interface private none
anyconnect firewall-rule client-interface public none
anyconnect keep-installer installed
anyconnect ssl keepalive 20
anyconnect ssl rekey time none
anyconnect ssl rekey method none
anyconnect dpd-interval client 30
anyconnect dpd-interval gateway 30
anyconnect ssl compression none
anyconnect dtls compression none
anyconnect modules none
anyconnect profiles none
anyconnect ssl df-bit-ignore disable
anyconnect routing-filtering-ignore disable
tunnel-group DefaultWEBVPNGroup type remote-access
tunnel-group DefaultWEBVPNGroup general-attributes
no address-pool
no ipv6-address-pool
authentication-server-group ISE
secondary-authentication-server-group none
no accounting-server-group
default-group-policy DfltGrpPolicy
no dhcp-server
no nat-assigned-to-public-ip
no password-management
no authorization-required
username-from-certificate CN OU
secondary-username-from-certificate CN OU
authentication-attr-from-server primary
authenticated-session-username primary
tunnel-group DefaultWEBVPNGroup webvpn-attributes
authentication aaa
no radius-reject-message
no pre-fill-username ssl-client
no secondary-pre-fill-username ssl-client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 08:10 AM
Hi,
Your Group Policy does not reference a VPN Pool, but the tunnel-group does. I've tested the following configuration inconjuction with the ISE configuration in a previous message. User connects to the Default Tunnel Group (no drop down list to select profile), ISE authenticates and authorizes the session, either the GP-1 or GP-2 group-policy is successfully assigned to the users' session, depending on AD group membership. The VPN pool is reference in the group-policy
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ssl-client
group-policy GP-1 attributes
dns-server value 192.168.10.5 192.168.10.6
vpn-tunnel-protocol ssl-client
address-pools value POOL_1
group-policy GP-2 attributes
dns-server value 192.168.10.5
vpn-tunnel-protocol ssl-client
address-pools value POOL_2
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2019 03:12 PM
RJI ,
thanks for all your help.
that fixed it!!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: