- Cisco Community
- Technology and Support
- Security
- VPN
- ASA 5516x Ikev1 Phase 2 Error
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5516x Ikev1 Phase 2 Error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2020 10:59 AM
We have a, IKEv1 VPN tunnel between two 5516x firewalls, that fails phase 2 continuously until we do a shut/no shut on the tunnel interface. At times one side of the tunnel will show as mm_active, while the other side will show that it is rekeying. This problem is not consistent, it does not occur every time that the tunnel lifetime expires, it will only occur sometimes. Recently as well we noticed that the tunnels will just stop sending DPD packets at random for several hours at a time.
We have been working with TAC for a few months on this issue with no resolution yet so wanted to see if anyone else has experienced something similar. They have verified that this is not a configuration issue.
Both of these ASAs are running the most recent version of 9.14.1 Interim.
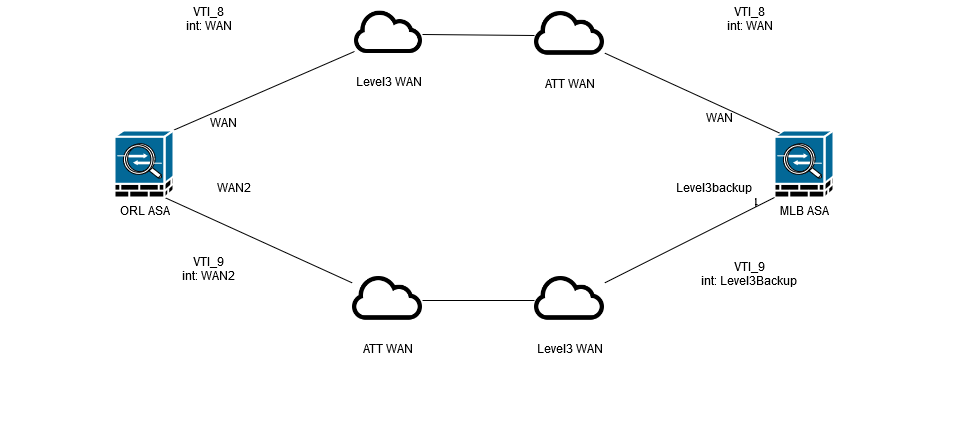
There are two VPN tunnels that run between these two sites, one runs over the main internet connection and the other runs over the backup internet connection of both sites. Below is a basic diagram with how the two sites are connected.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2020 12:34 PM
Look at the diagram, looks odd, maybe diagram wrong i guess here ATT WAN going vial Level3 WAN --odd diagram)
Coming back to your problem - Can you post ASA version code and configuration of both the device? (by removing confidential information)
when it fails or stops - did you collect any Logs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2020 12:43 PM
So in ORL we have a main Level3 circuit, and a backup ATT circuit. In MLB Level3 is the main circuit and ATT is the backup. So VTI_8 builds over both main circuits and VTI_9 builds over both backup circuits. I guess I should have included an internet object between.
We have debug logs and syslog, syslog has been reviewed and turned up nothing, TAC is reviewing our debug logs which is the output of "debug crypto ikev1 250". I will work on getting the configuration sanitized, but TAC has told us it is not a configuration issue. We are starting to think there is an issue with having two tunnels between the same devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2020 01:23 PM - edited 09-04-2020 01:24 PM
I have included what I believe are the relevant parts of the configuration below with changed IPs, as well as an updated diagram with the changed IP address
In the diagram, "WAN2" should be ATTBackup
ORL ASA Config:
ASA Version 9.14(1)10
interface GigabitEthernet1/1
description Level3
duplex full
nameif WAN
security-level 0
ip address 100.0.0.1 255.255.255.248
interface GigabitEthernet1/7
duplex full
nameif ATTbackup
security-level 0
ip address 200.0.0.1 255.255.255.248
interface Tunnel8
description VTI to ORL
nameif VTI_8
ip address 192.168.210.5 255.255.255.252
tunnel source interface WAN
tunnel destination 150.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSECPROF
interface Tunnel9
description Backup VTI to ORL
nameif VTI_9
ip address 192.168.212.5 255.255.255.252
tunnel source interface ATTbackup
tunnel destination 250.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSECPROF
crypto ipsec profile IPSECPROF
set ikev1 transform-set ESP-AES-128-SHA
set security-association lifetime kilobytes unlimited
set security-association lifetime seconds 86400
crypto ikev1 enable WAN
group-policy tunnelGP internal
group-policy tunnelGP attributes
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol ikev1
tunnel-group 150.0.0.1 type ipsec-l2l
tunnel-group 150.0.0.1 general-attributes
default-group-policy tunnelGP
tunnel-group 150.0.0.1 ipsec-attributes
ikev1 pre-shared-key
tunnel-group 250.0.0.1 type ipsec-l2l
tunnel-group 250.0.0.1 general-attributes
default-group-policy tunnelGP
tunnel-group 250.0.0.1 ipsec-attributes
ikev1 pre-shared-key
MLB ASA Config:
ASA Version 9.14(1)10
interface GigabitEthernet1/1
description ATT
duplex full
nameif WAN
security-level 0
ip address 150.0.0.1 255.255.255.248
interface GigabitEthernet1/7
duplex full
nameif Level3backup
security-level 0
ip address 250.0.0.1 255.255.255.248
interface Tunnel8
description VTI to MLB
nameif VTI_8
ip address 192.168.210.5 255.255.255.252
tunnel source interface WAN
tunnel destination 100.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSECPROF
interface Tunnel9
description Backup VTI to MLB
nameif VTI_9
ip address 192.168.212.5 255.255.255.252
tunnel source interface Level3backup
tunnel destination 200.0.0.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSECPROF
crypto ipsec profile IPSECPROF
set ikev1 transform-set ESP-AES-128-SHA
set security-association lifetime kilobytes unlimited
set security-association lifetime seconds 86400
crypto ikev1 enable WAN
group-policy tunnelGP internal
group-policy tunnelGP attributes
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol ikev1
tunnel-group 100.0.0.1 type ipsec-l2l
tunnel-group 100.0.0.1 general-attributes
default-group-policy tunnelGP
tunnel-group 100.0.0.1 ipsec-attributes
ikev1 pre-shared-key
tunnel-group 200.0.0.1 type ipsec-l2l
tunnel-group 200.0.0.1 general-attributes
default-group-policy tunnelGP
tunnel-group 200.0.0.1 ipsec-attributes
ikev1 pre-shared-key
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: