- Cisco Community
- Technology and Support
- Security
- VPN
- ASA anyconnect VPN not able to access remote LAN (inside) network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 01:35 AM
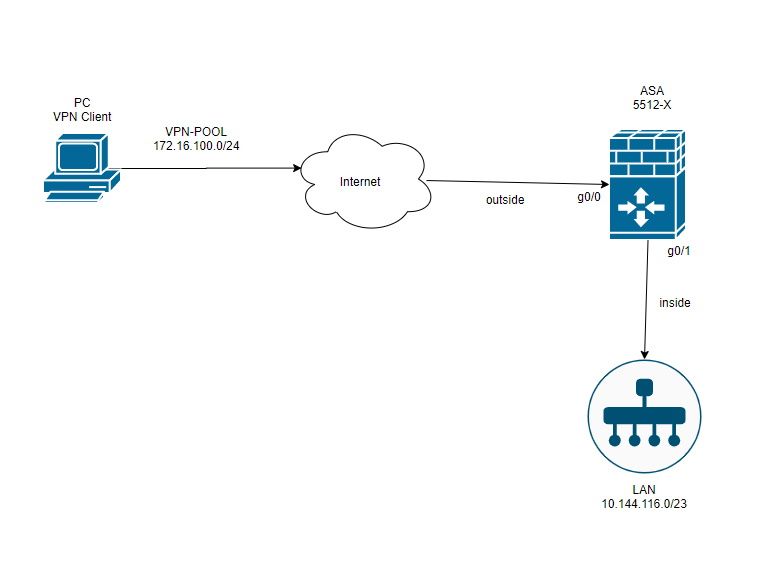
Hello everyone, I have Cisco ASA 5512 with configured Anyconnect VPN. The connection is established normally, but VPN clients do not see the network resources such as computers and servers inside LAN. My topology:
And here is running config:
Hardware: ASA5512, 4096 MB RAM, CPU Clarkdale 2800 MHz, 1 CPU (2 cores)
:
ASA Version 9.12(3)2
!
hostname DKRS-ASA
domain-name DKRS.ORG
enable password ***** encrypted
service-module 0 keepalive-timeout 4
service-module 0 keepalive-counter 6
service-module ips keepalive-timeout 4
service-module ips keepalive-counter 6
service-module cxsc keepalive-timeout 4
service-module cxsc keepalive-counter 6
names
no mac-address auto
ip local pool tempVPNpool2 10.144.116.58-10.144.116.65 mask 255.255.254.0
ip local pool tempVPNpool1 10.144.116.52-10.144.116.56 mask 255.255.254.0
ip local pool VPN-POOL 172.16.100.2-172.16.100.250 mask 255.255.255.0
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 217.175.147.40 255.255.255.240
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 10.144.116.40 255.255.254.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.100 255.255.255.0
!
ftp mode passive
clock timezone MSK/MSD 3
clock summer-time MSK/MDD recurring last Sun Mar 2:00 last Sun Oct 3:00
dns domain-lookup outside
dns server-group DefaultDNS
name-server 8.8.8.8 outside
name-server 8.8.4.4 outside
domain-name DKRS.ORG
same-security-traffic permit inter-interface
object network lan-subnet
subnet 10.144.116.0 255.255.254.0
object network NETWORK_OBJ_10.144.116.48_28
subnet 10.144.116.48 255.255.255.240
access-list SPLIT-ACL standard permit 10.144.116.0 255.255.254.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-7122.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 8192
nat (inside,outside) source static any any destination static NETWORK_OBJ_10.144.116.48_28 NETWORK_OBJ_10.144.116.48_28 no-proxy-arp route-lookup
!
object network lan-subnet
nat (inside,outside) dynamic interface
route outside 0.0.0.0 0.0.0.0 217.175.147.33 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 management
http 10.144.116.0 255.255.254.0 inside
snmp-server host inside 10.144.116.36 community ***** version 2c
no snmp-server location
no snmp-server contact
snmp-server community *****
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint ASDM_TrustPoint0
enrollment self
subject-name CN=DKRS-ASA
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_TrustPoint0
certificate 8609735e
308201e1 3082014a a0030201 02020486 09735e30 0d06092a 864886f7 0d01010b
05003035 3111300f 06035504 03130844 4b52532d 41534131 20301e06 092a8648
86f70d01 09021611 444b5253 2d415341 2e444b52 532e4f52 47301e17 0d323030
33313931 32343230 305a170d 33303033 31373132 34323030 5a303531 11300f06
03550403 1308444b 52532d41 53413120 301e0609 2a864886 f70d0109 02161144
4b52532d 4153412e 444b5253 2e4f5247 30819f30 0d06092a 864886f7 0d010101
05000381 8d003081 89028181 00a66d12 09b19b79 e75f9f3c 2dc6ce47 417f8515
d722c4c8 549696a2 b671568a 34ea2bda cc5c039d 2897e689 9c3e341c a6d2efba
614c4e4c 0e01eb16 10a49458 93b42c15 f5c7d3d9 432c600c 0186e9b1 250ced5d
f8d9d534 345824a3 58e09867 a9bf71a2 2aaf8693 4f54cb1c b00bc25b c36bfa72
533b0bf4 a6acecf7 321daae5 93020301 0001300d 06092a86 4886f70d 01010b05
00038181 002c5ead e11e2af8 791306e4 487a1e6b 6b8d98a9 5a92eb22 09955614
26759aab 0a5c1a69 5e2c8161 8d6893ec b6f11e10 70fe0da4 eed7a69d b6f7ed14
921d10b8 b39fffeb 26346c83 26f39f96 d64de75f 0b70d3d8 a7d31860 65d6a7d4
3cb85864 4836c7fa abe66237 a32201c1 c448dbf1 49deb917 77181ae0 053e8dc4
4960f5d0 16
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside client-services port 443
crypto ikev2 remote-access trustpoint ASDM_TrustPoint0
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group14-sha256
ssh 10.144.116.0 255.255.254.0 inside
console timeout 0
dhcpd address 192.168.1.101-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 88.147.254.235 source outside prefer
ssl trust-point ASDM_TrustPoint0 outside
ssl trust-point ASDM_TrustPoint0 inside
webvpn
enable outside
hsts
enable
max-age 31536000
include-sub-domains
no preload
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-4.8.02045-webdeploy-k9.pkg 1
anyconnect profiles DKRS-VPN_client_profile disk0:/DKRS-VPN_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_DKRS-VPN internal
group-policy GroupPolicy_DKRS-VPN attributes
wins-server value 10.144.116.12
dns-server value 10.144.116.12
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT-ACL
default-domain value DKRS.ORG
webvpn
anyconnect profiles value DKRS-VPN_client_profile type user
dynamic-access-policy-record DfltAccessPolicy
username bfg password ***** pbkdf2
username admin password ***** pbkdf2 privilege 15
username dzhuvalyakovds password ***** pbkdf2
tunnel-group DKRS-VPN type remote-access
tunnel-group DKRS-VPN general-attributes
address-pool VPN-POOL
default-group-policy GroupPolicy_DKRS-VPN
tunnel-group DKRS-VPN webvpn-attributes
group-alias DKRS-VPN enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:33ac6d421218c16044a1d4e87c639cd5
: endCan anyone help me, what setting did i miss? Thanks a lot.
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 04:49 AM
Hi,
Configure the following:
object network vpn-subnet
subnet 172.16.100.0 255.255.255.0
!
nat (inside, outside) source static lan-subnet lan-subnet destination static vpn-subnet vpn-subnet route-lookup
!
management-access inside
icmp permit any inside
Establish the VPN session and ping the ASA's inside IP address, like ping 10.144.116.40. It has to work, so it means you should be able to access LAN resources, as long as:
- there is no other layer 3 device behind the ASA, and everyone has the ASA as the default gateway
- if there is another layer 3 device behind the ASA, that device routes for the VPN pool range towards the ASA
Regards,
Cristian Matei.
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 03:03 AM
Hi,
Whateverclient or server has another default gateway than the ASA (10.144.116.4), it needs to be configured to route for the VPN Client Pool IP Range (172.16.100.0/24) towards the ASA (next-hop of 10.144.116.4). So if the layer 3 device which is used as the default gateway for some users, for example 10.144.116.1, is a Cisco device, you would go and configure "ip route 172.16.100.0 255.255.255.0 10.144.116.4).
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 02:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 02:50 AM
Hi,
You need to perform NAT exemption for traffic going to and from your VPN clients. Add the following config:
object network vpn-subnet
subnet 172.16.100.0 255.255.255.0
!
nat (inside, outside) source static lan-subnet lan-subnet destination static vpn-subnet vpn-subnet
Not sure what is the scope of the following NAT statement, either, but it should not interfere with your VPN traffic:
nat (inside,outside) source static any any destination static NETWORK_OBJ_10.144.116.48_28 NETWORK_OBJ_10.144.116.48_28 no-proxy-arp route-lookup
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 04:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 08:50 AM
Suppose Cristian is right.
But not sure about nat zone.
I suppose this should work
nat (inside,any) source static NETWORK_OBJ_10.144.116.48_28 NETWORK_OBJ_10.144.116.48_28 destination static vpn-subnet vpn-subnet no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 11:15 PM
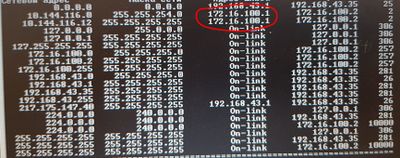
I tried it, but it didn't help, and i noticed one thing. I check windows route table after establish connection, and saw that gateway assign - 172.16.100.1, but asa has no such ip address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2020 04:49 AM
Hi,
Configure the following:
object network vpn-subnet
subnet 172.16.100.0 255.255.255.0
!
nat (inside, outside) source static lan-subnet lan-subnet destination static vpn-subnet vpn-subnet route-lookup
!
management-access inside
icmp permit any inside
Establish the VPN session and ping the ASA's inside IP address, like ping 10.144.116.40. It has to work, so it means you should be able to access LAN resources, as long as:
- there is no other layer 3 device behind the ASA, and everyone has the ASA as the default gateway
- if there is another layer 3 device behind the ASA, that device routes for the VPN pool range towards the ASA
Regards,
Cristian Matei.
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 01:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 03:03 AM
Hi,
Whateverclient or server has another default gateway than the ASA (10.144.116.4), it needs to be configured to route for the VPN Client Pool IP Range (172.16.100.0/24) towards the ASA (next-hop of 10.144.116.4). So if the layer 3 device which is used as the default gateway for some users, for example 10.144.116.1, is a Cisco device, you would go and configure "ip route 172.16.100.0 255.255.255.0 10.144.116.4).
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2020 03:37 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide