- Cisco Community
- Technology and Support
- Security
- VPN
- Re: ASA keeping session active after client powers down.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA keeping session active after client powers down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 08:37 AM
Hi,
My ASA is holding on to sessions too long. We have devices that use vpn tunnels in the field. They are occasionally rebooted. They use usernames for static IP assignment from the ASA. Trouble is when the device powers down, the VPN is not ending the session. When the device powers back up the ASA is not creating a new session for it or ending the previous session so it stays stuck offline.
I recently posted this similar situation here but felt it had evolved to a different problem to continuing in a new thread as the previous answer was on how to change the idle timeout. The idle timeout is currently at 1 minute but the vpn is not ending while the device is powered down.
Any help is greatly appreciated.
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 08:43 AM - edited 06-23-2022 08:44 AM
how is your DPD config on the firewall, if the peer dead the connection should disconnect :
check common troubleshoot tips :
check the logs and session DB information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 09:10 AM
Sorry, these arent anyconnect clients. Also, when I look at the anyconnect policies that I do have with the webvpn syntax in them. If I try to add to that I do not get the options for SVC syntax.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 09:09 AM
can I see show vpn session db?
before and after power down the VPN client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 09:19 AM
Sorry, I dont have the ability to power one down currently. Can I still show a "before"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 09:22 AM
Yes if you can share before.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
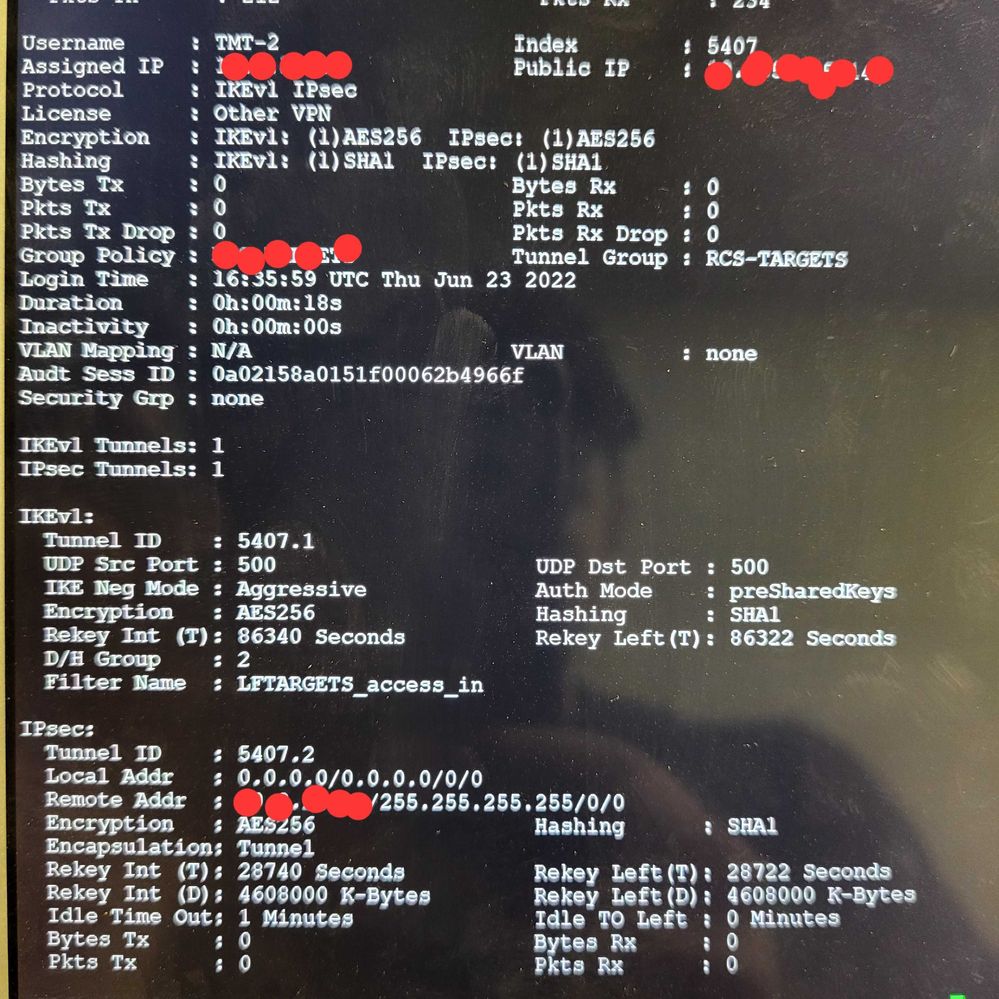
06-23-2022 09:39 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 10:32 AM
I've also been looking at setting up Keep alives for these ikev1 tunnels which should be more like an "are you there?" message or a DPD setting but I dont see any options to turn this feature on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 11:23 AM
Figured it out.
Needed to do a "show running-config all" to see hidden parameters.
Then i saw the error in where i was trying to do this.
*tunnel-group NAME ipsec attributes*
Then my commands would work: https://community.cisco.com/t5/security-documents/dead-peer-detection/ta-p/3111324
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: